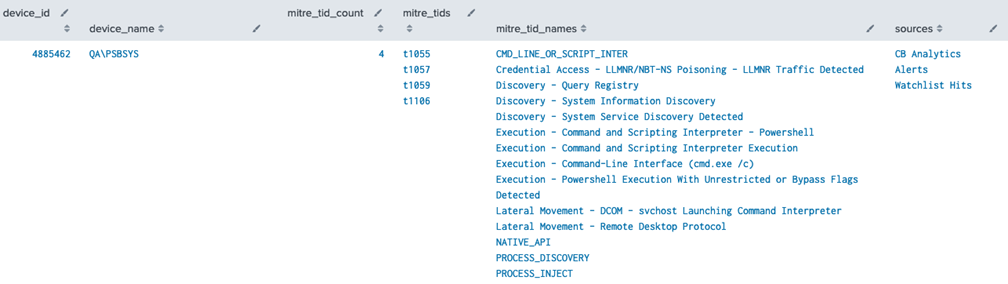
If you have both Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR, you can combine CB Analytics Alerts and Watchlist Hits for a unified view of MITRE.
Required Product: Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR
Required Data: Alerts (App Input or Data Forwarder), Watchlist Hits (Data Forwarder)
Top MITRE TIDs by Endpoint Count, including Technique Name and Data Source
eventtype="vmware_cbc_cb_analytics"
| rename threat_indicators{}.ttps{} as mitre_ttps
| mvexpand mitre_ttps
| rex field=mitre_ttps "^MITRE_(?<mitre_tid>T\d+(\_\d{3})?)_(?<mitre_tid_name>.*)$"
| where not isnull(mitre_tid)
| eval mitre_tid = lower(mitre_tid), source = "CB Analytics Alerts"
| fields device_id, device_name, mitre_tid, mitre_tid_name, source
| append [
search eventtype="vmware_cbc_base_index" sourcetype="vmware:cbc:s3:watchlist:hits"
| rename report_tags{} as mitre_tids
| mvexpand mitre_tids
| regex mitre_tids="^t\d+$"
| eval mitre_tid_name = report_name, source = "Watchlist Hits"
| fields device_id, device_name, mitre_tid, mitre_tid_name, source
]
| stats
dc(mitre_tid) as mitre_tid_count
values(mitre_tid) as mitre_tids,
values(mitre_tid_name) as mitre_tid_names,
values(source) as sources
by device_id, device_name
| sort -mitre_tid_count