You can leverage the Data Forwarder and Custom Query Filters to forward Log4Shell-relevant EDR data to Splunk SIEM.
Required Product: Any
Required Data: Audit Logs (App Input)
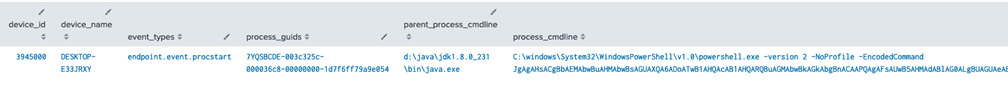
Identify Java Spawning Powershell
| tstats summariesonly=t values(All_CBC.Endpoint.parent_process_exec) AS parent_process_cmdline, values(All_CBC.Endpoint.procstart.childproc_name) as childproc_names, values(All_CBC.process_guid) as process_guids, values(All_CBC.type) as event_types latest(_time) AS latest, earliest(_time) AS earliest from datamodel=VMWare_CBC where ((All_CBC.Endpoint.parent_process_exec="*java*" OR All_CBC.Endpoint.parent_process_exec="*tomcat*") AND All_CBC.process_executable="*powershell*") by All_CBC.device_name, All_CBC.device_id, All_CBC.org_key, All_CBC.process_executable | rename All_CBC.* as *, process_executable as process_cmdline | eval _time=latest | reltime | convert ctime(latest), ctime(earliest) | table device_id, device_name, event_types, process_guids, parent_process_cmdline, process_cmdline, childproc_names, reltime, earliest, latest