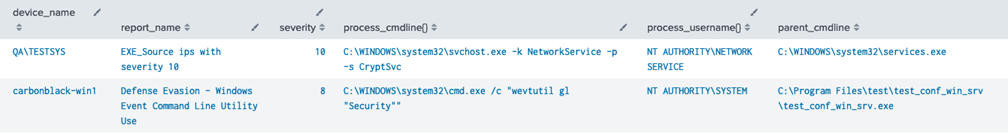
Carbon Black Cloud has dozens of metadata fields about every process that executes on an endpoint. While not all of this metadata is included in a Watchlist Alert, the Process GUID Details Alert action can automatically query Carbon Black Cloud for all process details following a Watchlist Alert.
Required Product: Carbon Black Cloud Enterprise EDR
Required Data/Configurations: Alerts (App Input or Data Forwarder), Process GUID Details (App Alert Action), Process GUID Details (user-created Splunk Alert)
Any field tagged DETAILS in the Process Search Fields documentation will be available.
eventtype="vmware_cbc_watchlist"
| join process_guid [
search eventtype="vmware_cbc_action_index" sourcetype="vmware:alert_action:vmware-process-guid-details"
| rename results{}.* as *
]
| table device_name, report_name, severity, process_cmdline{}, process_username{}, parent_cmdline