CI/CD integration and a shift-left approach is an effective strategy; however, continuously monitoring the security posture in production is also required.
Cluster scanning provides the same level of visibility as scanning applications developed in CI/CD to third-party and infrastructure-level components. It is critical to ensure container images used in any running workload are up-to-date and can detect vulnerabilities.
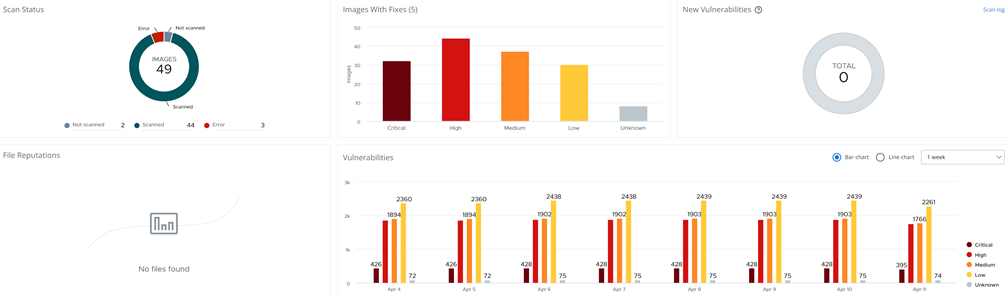
Runtime cluster scanning ensures all running images are scanned for misconfigurations and vulnerabilities to better evaluate overall risk. For example, to confirm that the applied configuration and manifest still aligns with the policy, thereby identifying vulnerable misconfigurations and making sure that the cluster itself does not have any clear text secrets or malicious containers running. This capability enables DevOps and Security teams to understand the level of security in the run state, and to make any necessary changes to the pipeline to better secure workloads.
Container images present some security challenges. Images are usually built by layering other images, which could contain vulnerabilities, and those vulnerabilities can find their way into production systems. Defects and malware can also affect container images. When the provenance of a container is unknown, these risks increase.
Container image registries with the following functionality can reduce these risks:
- Scan images for vulnerabilities found in the Common Vulnerabilities and Exploits (CVE) database.
- Sign images as known and trusted by using a notary.
- Set up secure, encrypted channels for connecting to the registry.
- Authenticate users and control access by using existing enterprise accounts managed in a standard directory service, such as Active Directory.
- Tightly control access to the registry using the principles of least privilege and separation of duties.
- Enact policies that let users consume only those images that meet your organization’s thresholds for vulnerabilities.
Vulnerability Scanning
Most applications use components that are sourced from third-party image registries. Having realized this, attackers often insert malicious code into these registries. Containers often use base images of operating systems like Ubuntu and CentOS from a public image repository such as DockerHub. The packages of an operating system and the applications on it can contain vulnerabilities.
Vulnerability scanning helps detect known vulnerabilities to reduce the risk of security breaches. Identifying an image vulnerability or malware on an image, and keeping those from going into production, reduces the attack surface of a containerized application.