An application or compute workload, running outside the Google Cloud Platform (GCP), can authenticate as a service account and use the service account's identity for authorization. Such impersonation of a service account is provided by the Workload Identity Federation service. This service allows you to use credentials from external identity providers (IdP) to generate ephemeral, short-lived credentials (token), which your external applications or workloads, temporarily identified as a service account, can use to access the Google Cloud services and resources from outside of GCP.
For more information, see Workload identity federation.
To organize and manage external identities, you must create a workload identity pool. The workload identity pool is a logical container of external identities.
Note: It is a best practice to isolate your pools by GCP environment. For example, one GCP workload identity pool for your development environment and a separate isolated pool for your production environment.
The following is a basic flow of an application impersonating a Google service account through the Workload Identity Federation service.
Prerequisites
Verify you are familiar with CEL expressions. For details, see Attribute mappings.
Procedure
- In the Google Cloud console, search for workload identity federation, and select it from the related drop-down menu.
The
Workload Identity Pools page displays under the IAM and Admin category.
- Click Create Pool.
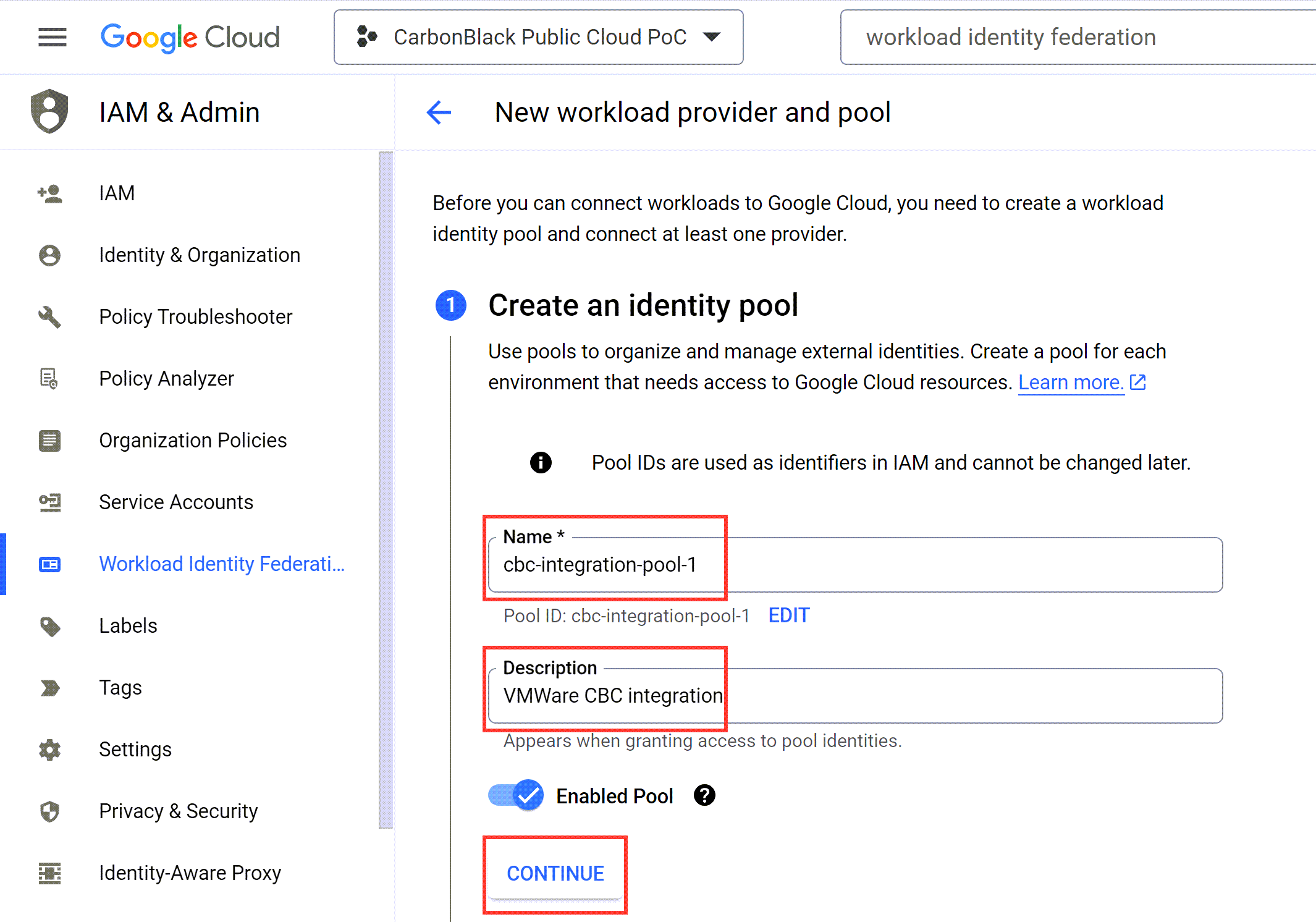
- In step 1, Create an identity pool, enter a name for the workload identity pool.
The console generates an ID based on the name you provide.
- Optional. Edit the ID.
Once you create the identity pool, you cannot change its ID.
- Optional. Enter a description for the purpose of the pool.
For example,
Carbon Black Cloud integration.
- To save your changes, click Continue.
- In step 2, Add a provider to pool, click the Select a provider drop-down menu and select AWS.
- Enter the name of the provider and the AWS account where Carbon Black Cloud Public Cloud services are running.
- Click Continue.
- In step 3, Configure provider attributes, to define how to obtain the value of the Google STS token attribute from an external token, click Edit Mapping and add an attribute mapping.
The Security Token Service exchanges Google or third-party credentials for a temporary access token to Google Cloud resources.
- In the Google 2 text field, enter the custom token attribute attribute.aws_role.
- In both AWS 1 and AWS 2 text fields, enter the extraction expression, which specifies the name of the assumed role or the identity's ARN to extract.
assertion.arn.contains('assumed-role') ? assertion.arn.extract('{account_arn}assumed-role/') + 'assumed-role/' + assertion.arn.extract('assumed-role/{role_name}/') : assertion.arn
- In the Attribute Conditions section, set the Condition CEL to true.
- To create the identity pool, click Save.
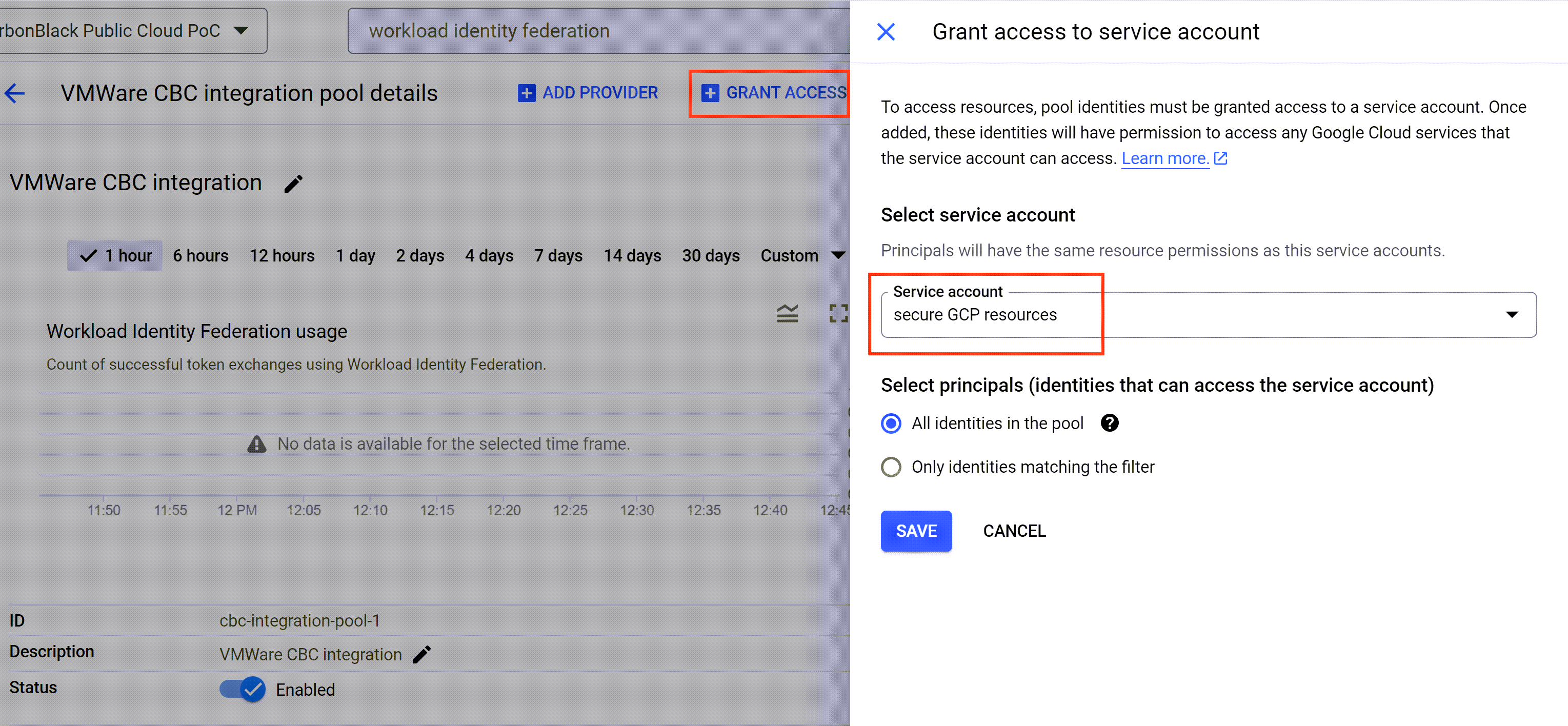
- To associate the identity federation pool with a Google Cloud service account, click Grant Access.
- In the Grant access to service account panel, click the Service account drop-down menu and select the service account you previously created.
- In the Select principals section, select the Only identities matching the filter option and set the AWS role.
- Select aws_role from the attribute name drop-down menu.
- Enter the attribute value for the aws_role.
Follow the syntax
arn:aws:sts::<aws_id>:assumed-role/<role_name>, where the AWS ID is
132308400445 and the assumed role name
<role_name> can be either of the following depending on the region.
| Option |
Description |
| USA |
mcs2-app-prd5use1-pub-cloud-gcp-service-role |
| Europe (eu-west-2) |
mcs2-app-prd1ew2-pub-cloud-gcp-service-role |
| Europe (eu-central-1) |
mcs2-app-prd1ec1-pub-cloud-gcp-service-role |
| Sydney |
mcs2-app-prd1apse2-pub-cloud-gcp-service-role |
| Tokyo |
mcs2-app-prd1apne1-pub-cloud-gcp-service-role |
- In the Configure your application pop up, select the name of the identity provider from the related drop-down menu.
For example,
CBC console AWS provider.
- Click the Download Config button.
The
Carbon Black Cloud console uses the downloaded configuration JSON file to access the Google Cloud.