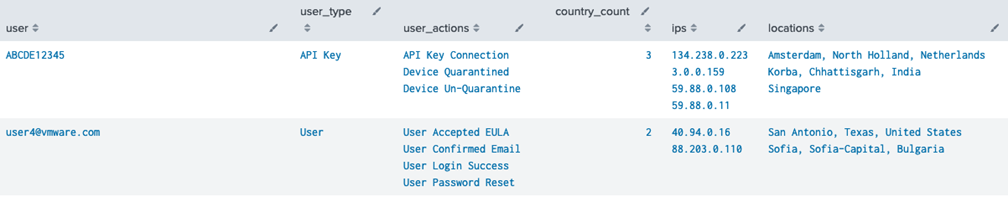
It can be helpful to break out user activity by category to see at a glance what each user (or API key) is doing and where the activity is coming from. Since most of the valuable information in the audit log is in plain text, the query parses the most common audit logs and outputs a category for more effective grouping. This query captures many common scenarios.
eventtype="vmware_cbc_auditlogs" user=*
| eval category = case(
like(description, "Updated report %"), "Report Updated",
like(description, "Connector % logged in successfully"), "API Key Connection",
like(description, "A bulk policy update has been applied%"), "Device Policy Updated",
like(description, "Changed device % policy %"), "Device Policy Updated",
like(description, "Added API ID %"), "API Key Created",
like(description, "Added user %"), "User Created",
like(description, "Alert % dismissed %"), "Alert Dismissed",
like(description, "Changed Password%"), "User Password Changed",
like(description, "Created Config: {%"), "Data Forwarder Created",
like(description, "Created custom role %"), "Role Created",
like(description, "Custom role % updated %"), "Role Updated",
like(description, "Deleted API ID %"), "API Key Deleted",
like(description, "Deleted Config: %"), "Data Forwarder Deleted",
like(description, "Device % uninstalled"), "Device Uninstalled",
like(description, "Downloaded policy configuration%"), "Policy Downloaded",
like(description, "LiveResponse%"), "Live Response",
like(description, "Logged in successfully"), "User Login Success",
like(description, "Login in successfully through %"), "User Login Success (MFA)",
like(description, "Password did not match %"), "User Login Failure",
like(description, "Password reset %"), "User Password Reset",
like(description, "Policy % was deleted"), "Policy Deleted",
like(description, "Account locked %"), "User Account Locked",
like(description, "Policy % was modified%"), "Policy Modified",
like(description, "Ran query%"), "Live Query Executed",
like(description, "Created grant%"), "User Grant Created",
like(description, "Requested sensor upgrade%"), "Device Version Update Requested",
like(description, "Searched for reputations%"), "Reputation Search",
like(description, "Sensor Bypass Enabled%"), "Sensor Bypass Enabled",
like(description, "Sensor Bypass Disabled%"), "Sensor Bypass Disabled",
like(description, "Set BACKGROUND_SCAN to off%"), "Device Background Scan Disabled",
like(description, "Set BACKGROUND_SCAN to on%"), "Device Background Scan Enabled",
like(description, "Set BYPASS to off%"), "Device Un-Bypassed",
like(description, "Set BYPASS to on%"), "Device Bypassed",
like(description, "Set QUARANTINE to off%"), "Device Un-Quarantine",
like(description, "Set QUARANTINE to on%"), "Device Quarantined",
like(description, "Successfully exported query results%"), "Live Query Results Exported",
like(description, "%Policy Settings Changed%"), "Policy Updated",
like(description, "Updated Config:%"), "Data Forwarder Updated",
like(description, "Successfully confirmed the email%"), "User Confirmed Email",
like(description, "Updated custom role%"), "Role Updated",
like(description, "Updated watchlist%"), "Watchlist Updated",
like(description, "User % added Reputation Override%"), "Reputation Override Added",
like(description, "User % retrieved secret%"), "API Key Secret Viewed",
like(description, "User % accepted EULA%"), "User Accepted EULA",
like(description, "%Tab:Settings (Enrollment)%"), "Viewed Devices Page",
like(description, "Hash % was %requested to be deleted %"), "Device Malware Deleted",
like(description, "Failure deleting hash %"), "Device Malware Delete Failed",
like(description, "Looked up reputation %"), "Reputation Lookup",
like(description, "Replaced % reports in %"), "Watchlist Updated",
like(description, "Re-registration of device %"), "Device Re-Registered",
like(description, "Sent deregister request %"), "Device De-Registered",
like(description, "Delete Deregistered Devices %"), "Device Deleted",
like(description, "% was deleted from your organization %device%"), "Device Deleted",
like(description, "% deregistered through %"), "Device De-Registered",
like(description, "Success deleting hash % off of device %"), "Device Malware Deleted",
like(description, "Downloaded output of job %"), "Search Results Downloaded",
like(description, "Sensor registered on VM %"), "Device Registered on VM",
like(description, "Invalid authentication method %"), "User Login Failure",
like(description, "Upload Hash %"), "Device Malware Upload",
like(description, "%Tab:Malware Removal%"), "Viewed Malware Removal Page",
like(description, "Delete Hash % requested for device%"), "Device Malware Deleted",
like(description, "Going to update device% to version%"), "Device Version Updated",
like(description, "Created event export job%"), "Search Results Exported",
like(description, "Registration Id not found for VM %"), "Device Registration on VM Failure",
like(description, "Request to delete owner %"), "User (Owner) Deleted",
like(description, "Sent upgrade sensor version request %"), "Device Version Update Requested",
like(description, "%devices were bulk % policy%"), "Device Policy Updated",
like(description, "Bulk ignored % report%"), "Watchlist Report Ignored",
like(description, "Appliance%Registration %"), "Appliance Registered",
like(description, "Success"), "Something was Successful",
like(description, "Uploaded file%"), "File Uploaded",
like(description, "Log export % for appliance %"), "Appliance Logs Exported",
like(description, "Updated access profile %"), "Role Updated",
like(description, "Updated user %"), "User Updated",
like(description, "Alert % undismissed %"), "Alert Undismissed",
like(description, "Undismissed % alert%"), "Alert Undismissed",
like(description, "Dismissed % alert%"), "Alert Dismissed",
like(description, "Created policy%"), "Policy Created",
like(description, "Created%feed%"), "Feed Created",
like(description, "Created%watchlist%"), "Watchlist Created",
like(description, "Created report%"), "Watchlist Report Created",
like(description, "Deleted custom role%"), "Role Deleted",
like(description, "Deleted grant%"), "User Grant Deleted",
like(description, "Initiated request%to undismiss%"), "Alert Undismissed",
like(description, "Initiated request%to dismiss%"), "Alert Dismissed",
like(description, "Query%deleted%"), "Live Query Deleted",
like(description, "Query run%stopped%"), "Live Query Run Stopped",
like(description, "%dashboard%"), "Dashboard Updated",
like(description, "Set Quarantine to On%"), "Device Quarantined",
like(description, "Set Quarantine to Off%"), "Device Unquarantined",
like(description, "Set Bypass to On%"), "Device Bypassed",
like(description, "Set Bypass to Off%"), "Device Unbypassed",
like(description, "Updated alert notification%"), "Alert Notification Updated",
like(description, "%tagging for watchlist%"), "Watchlist Tagging Updated",
like(description, "Installation triggered %"), "Device Installation Triggered",
like(description, "Sensor installation failed%"), "Device Installation Failed",
like(description, "Regenerated API key %"), "API Key Updated",
like(description, "Updated API %"), "API Key Updated",
like(description, "Threat ID % undismissed%"), "Threat Undismissed",
like(description, "Threat ID % dismissed%"), "Threat Dismissed",
like(description, "%deleted Reputation Overrides%"), "Reputation Override Deleted",
like(description, "Vulnerability%export%"), "Vulnerabilities Exported",
like(description, "Password is not set%"), "User Password Not Set",
like(description, "Bulk-applied % policy changes %"), "Device Policy Updated",
like(description, "Deleted admin%"), "User (Admin) Deleted",
like(description, "Sensor installation is ERROR%"), "Device Sensor Installation Failed",
like(description, "Sensor installation is SUCCESS%"), "Device Sensor Installation Succeeded",
like(description, "Updated policy%"), "Policy Updated",
like(description, "Updated grant%"), "User Grant Updated",
match(description, "device"), "Device Other",
match(description, "disabled"), "Other: Disabled",
match(description, "enabled"), "Other: Enabled",
match(description, "updated"), "Other: Updated",
match(description, "changed"), "Other: Changed",
match(description, "deleted"), "Other: Deleted",
match(description, "downloaded"), "Other: Downloaded",
1=1, "Other"
)
| eval user_type = if(match(user, "^[0-9A-Z]{10}$"), "API Key", "User")
| iplocation src
| eval location = case(Region = "", Country, City = "", Region + ", " + Country, 1=1, City + ", " + Region + ", " + Country)
| stats
values(category) as user_actions,
dc(Country) as country_count
values(src) as ips,
values(location) as locations,
by user, user_type