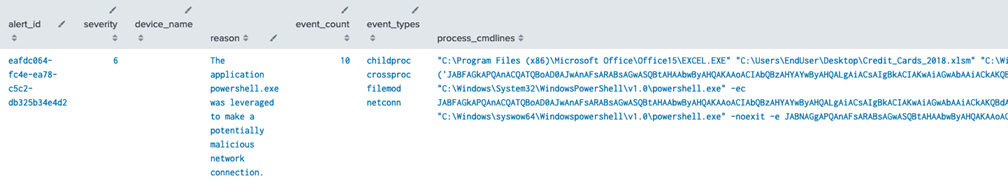
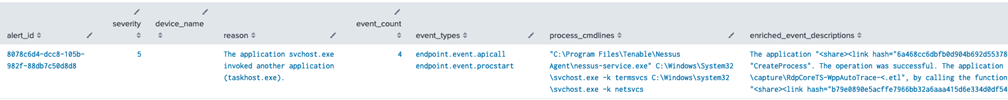
Every CB Analytics (NGAV) alert is tied to one or more Enriched Events. It’s very helpful to pivot to these events (also known as “Alerted Events”) and identify the behavior that led to the alert. This activity can provide insights such as what processes, cmdlines, and users were involved if any network connections occurred, and what files or registry keys were modified.
Required Product: Carbon Black Cloud Endpoint Standard
The syntax varies depending on whether you’re using the App Inputs and Alert Actions or Data Forwarder.
-
Using App Input and Alert Actions
-
Required Data and Configurations: Alerts (App Input), Enrich CB Analytic Events (App Alert Action), CB Analytics - Ingest Enriched Events (Splunk Alert)
-
eventtype="vmware_cbc_cb_analytics"
| eval alert_id = id
| dedup alert_id
| join alert_id [
search eventtype="vmware_cbc_base_index" sourcetype="vmware:alert_action:vmware-enrich-events"
| rename alert_id{} as alert_id
| stats dc(event_id) as event_count, values(event_type) as event_types, values(process_cmdline{}) as process_cmdlines, values(event_description) as enriched_event_descriptions by alert_id
]
| table alert_id, severity, device_name, reason, event_count, event_types, process_cmdlines, enriched_event_descriptions
-
Using the Data Forwarder
-
Required Data: (Data Forwarder), Endpoint Events (Data Forwarder)
-
You can configure the Data Forwarder to push both Alerts and Endpoint Events into Splunk through an AWS S3 bucket. To send only Alerted Events, which are just a small fraction of all endpoint events, use the following Custom Query Filter: