If an endpoint stops checking in to Carbon Black Cloud, consider launching an investigation. you can accomplish this by forwarding process start endpoint events (custom query filter type:endpoint.event.procstart) to Splunk.
Required Product: Carbon Black Cloud Enterprise EDR
Required Data: Endpoint Events (Data Forwarder), VMware CBC Device Info (App Custom Command)
These events comprise only a small percent of all EDR data, but provide tremendous visibility. Nearly every endpoint will generate process starts during a normal day.
Consider filtering further, such as by device group or policy:
- Critical endpoints such as Domain Controllers or production servers, where investigation should occur if data is missing for just a few hours.
- User endpoints such as laptops, where being offline for days can be normal.
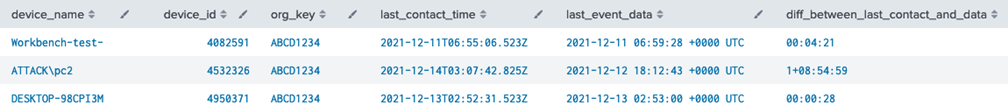
Run this query across the past 5-10 days. The query will identify the top 100 endpoints whose last event was received more than 24 hours ago. Then, retrieve the endpoint’s last contact time from the Carbon Black Cloud Devices API.
| `vmware_tstats` latest(All_CBC.Endpoint.backend_timestamp) as last_event_data from datamodel=VMWare_CBC where nodename=All_CBC.Endpoint by All_CBC.device_name, All_CBC.device_id, All_CBC.org_key | rename All_CBC.* as * | eval epoch_last_event_data = strptime(last_event_data, "%Y-%m-%d %H:%M:%S %z") | eval window = relative_time(now(), "-24h@h") | where epoch_last_event_data <= window | sort last_event_data | head 100 | cbcdvcinfo | eval epoch_last_contact = strptime(last_contact_time, "%Y-%m-%dT%H:%M:%S.%3N%Z") | eval diff = floor(abs(epoch_last_contact - epoch_last_event_data)) | eval diff_between_last_contact_and_data = tostring(diff, "duration") | table device_name, device_id, org_key, last_contact_time, last_event_data, diff_between_last_contact_and_data