After you upgrade to Splunk SIEM 2.x.x, consider the following action items.
- If you are using the Live Response
ListorKill Processactions, you must change the API key.- In the Splunk SIEM App, go to the Administration > Application Administration Page > Alert Actions tab.
- Deselect the old API Token and select the API Token using the Access Level you updated in Step 4 of Before you Upgrade from Splunk SIEM 1.x to 2.x.x.
- If you are using an audit log input, you must change the API key.
- In the Splunk SIEM App, go to the Administration > Application Administration Page > Audit Log Inputs tab.
- After upgrading, update the API Token used in the audit log input to the Custom type API key you updated in Step 5 of Before you Upgrade from Splunk SIEM 1.x to 2.x.x.
Note: When the API key has the audit log permission added, three days of audit logs will be ingested using that key. There can be three days of duplicate audit log data collected by Splunk when switching API keys.
- If you are using Carbon Black Cloud Enterprise EDR, you can ingest Authentication Events collected by Carbon Black Cloud into Splunk SIEM.
- In the Carbon Black Cloud Console:
- Click your username in the upper right corner of the page to verify that Carbon Black Cloud Enterprise EDR is enabled.
- Make sure that Auth Event collection is enabled in relevant policies. To enable Auth Event Collection, see Enable Auth Event Collection.
- In the Splunk SIEM App, go to the Administration > Application Administration Page > Auth Event Inputs tab.
Configure Auth Events as per the
Auth Eventssection of the Configure Built-in Inputs for Splunk SIEM.For more information, see Search Fields - Investigate.
- In the Carbon Black Cloud Console:
- If you are using the API ingest option, configure the types of alerts to ingest.
Note:
- Version 2.0.0 can ingest new types of alerts from Carbon Black Cloud.
- The Alert Type
Bothcan display after the upgrade.Bothincludes Carbon Black Analytics and Watchlist alert types, the were only two alert types that were supported in version 1.x.
- In the Splunk SIEM App, go to the Administration > Application Administration Page > Alerts Inputs tab.
- Choose the types of alerts to ingest. You can select
Allalert types.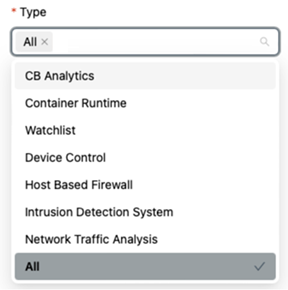
- If you are using the Data Forwarder Alerts Input, reconfigure the AWS SQS queue to consume the Alert v2 schema data.
Note: There can be duplicate data for the period during which both Data Forwarders were running.