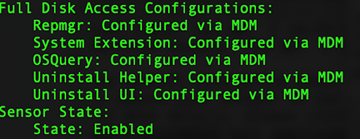
Identifier: com.vmware.carbonblack.cloud.daemon
Identifier Type: Bundle ID
Code Requirement:
identifier "com.vmware.carbonblack.cloud.daemon" and anchor apple generic
and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service: SystemPolicyAllFiles
Access: Allow
Identifier: com.vmware.carbonblack.cloud.osqueryi
Identifier Type: Bundle ID
Code Requirement:
identifier "com.vmware.carbonblack.cloud.osqueryi" and anchor apple generic
and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service: SystemPolicyAllFiles
Access: Allow
Identifier: com.vmware.carbonblack.cloud.se-agent.extension
Identifier Type: Bundle ID
Code Requirement:
identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic
and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service: SystemPolicyAllFiles
Access: Allow
Identifier: com.vmware.carbonblack.cloud.uninstall
Identifier Type: Bundle ID
Code Requirement:
identifier "com.vmware.carbonblack.cloud.uninstall" and anchor apple generic
and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service: SystemPolicyAllFiles
Access: Allow
Identifier: com.vmware.carbonblack.cloud.uninstallerui
Identifier Type: Bundle ID
Code Requirement:
identifier "com.vmware.carbonblack.cloud.uninstallerui" and anchor apple
generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service: SystemPolicyAllFiles
Access: Allow