This section describes how to enable alerts and syslog output for banning events.
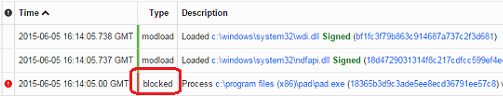
Unless banning is disabled entirely, process block events are sent to the Carbon Black EDR server and viewable on the Process Analysis page. (See Process Search and Analysis.)
To configure alerts and syslog output for process blocks, a special Banning Events panel is available on the Threat Intelligence Feeds page. (See Threat Intelligence Feeds.) This is not a feed in the normal sense because the events for blocks are sent to the server regardless of whether the feed is enabled. However, the feed must be enabled if you want to configure notifications for banning events.
The Banning Events feed is available by default and does not require enabling communication with Carbon Black Threat Intel.
Enable Alerts and Syslog Output for Banning Events
Perform the following procedure to enable alerts and syslog output for banning events.
Procedure
View Banned Hash Alerts
Perform the following procedure to view banned hash alerts.