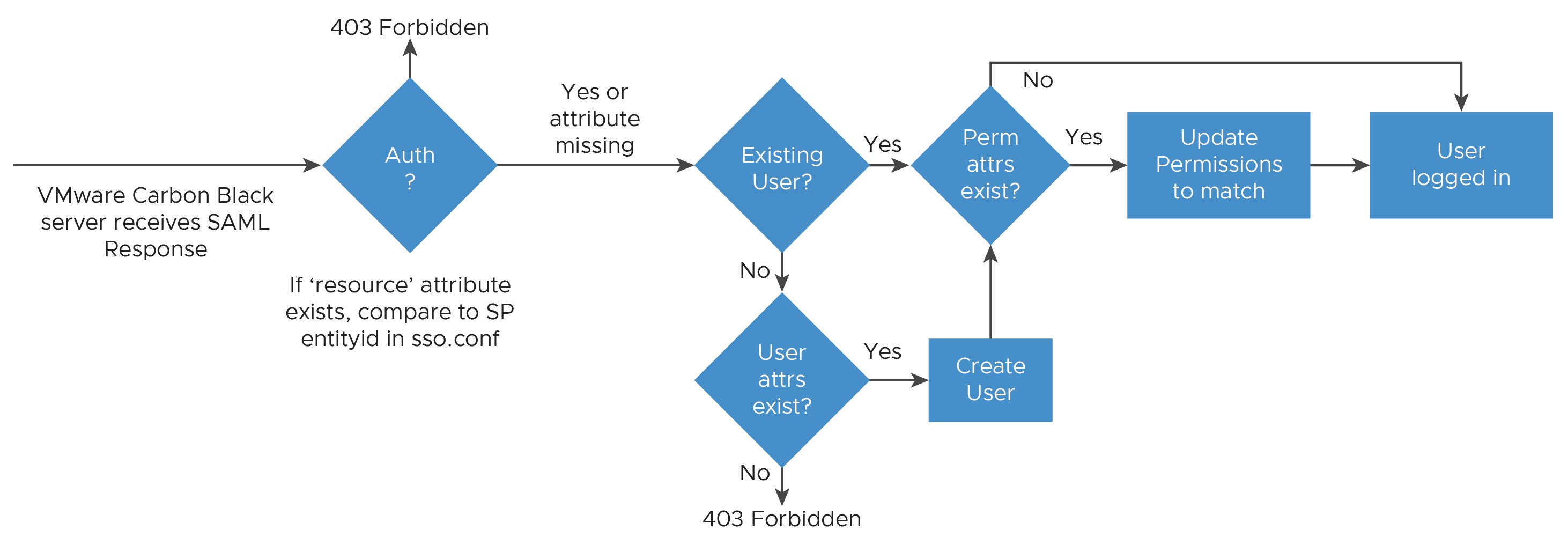
With Carbon Black EDR (version 5.2 and later), when SSO is configured, users who are authenticated by the configured IdP can be automatically provisioned in Carbon Black EDR if they are authorized and if the IdP returns the user’s first name, last name, and email address as user attributes.
The fields returned by the IdP are not part of the SAML 2.0 specification and vary between IdPs. For Carbon Black EDR, the attr_map.py script maps the attributes that are returned by an IdP to the fields that are required by Carbon Black EDR.
Carbon Black EDR supports the following seven attributes:
| Attribute |
Required |
Use |
|---|---|---|
| username |
Required |
The username to log in as. |
| authorized |
Optional (but strongly recommended) |
Required to authorize access. Boolean. “True” if this user is authorized access to the Carbon Black EDR server. |
| first_name |
Optional |
Required to provision a new user. |
| last_name |
Optional |
Required to provision a new user. |
| |
Optional |
Required to provision a new user. |
| builtin_roles |
Optional |
Required to set permissions. A list of roles. Valid roles: “GlobalAdmin” If None, this field is ignored. If an empty list ([]), all roles are removed. |
| teams |
Optional |
Required to set permissions. A list of teams this in which the user is a member. Names must match an existing configured team. If None, this field is ignored. If an empty list ([]), all team associations are removed. |
Your IdP administrator is responsible for providing you a list of attributes that are returned by the IdP. The username, first_name, last_name and email should map directly to the fields returned by your IdP. You must configure the authorized, builtin_roles, and teams fields, based on your business policies.
The following diagram describes the attribute mapping process: