Carbon Black EDR provides endpoint threat detection and a rapid response solution for Security Operations Center (SOC) and Incident Response (IR) teams.
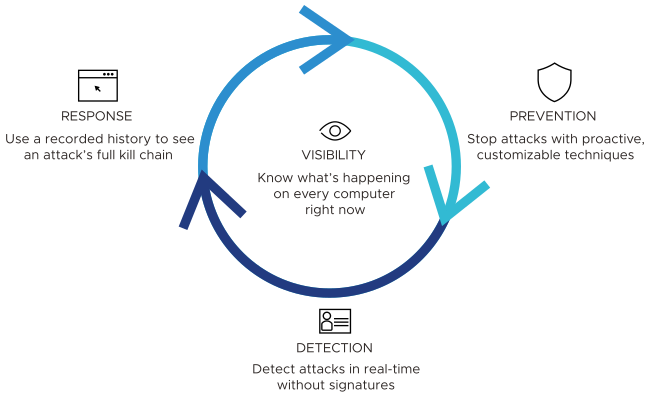
With Carbon Black EDR, enterprises can continuously monitor and record all activity on endpoints and servers. The combination of Carbon Black EDR’s endpoint visibility with Carbon Black Threat Intel helps enterprises to proactively hunt for threats, customize their detection, and respond quickly. The following diagram shows how Carbon Black EDR features work together to help you answer these questions:
-
How did the problem start?
-
What did the threat do?
-
How many machines are infected?
-
How can we resolve the threat?
Carbon Black EDR provides these solutions:
-
Visibility – Know what’s happening on every computer at all times. With Carbon Black EDR, you have immediate real-time visibility into the files, executions, network connections, and critical system resources on every machine, and the relationships between them. You can see how every file got there, what created it, when it arrived, what it did, if it made a network connection, if it deleted itself, if a registry setting was modified, and much more.
-
Detection – See and record everything; detect attacks in real time without signatures. Carbon Black EDR’s threat research team analyzes threat techniques and creates Advanced Threat Indicators (ATIs) to alert you to the presence of an attack. These ATIs look for threat indicators and are not based on signatures. You can detect advanced threats, zero-day attacks, and other malware that evades signature-based detection tools—in real time. There is no wait for signature files, no testing and updating .dat files, and no sweeps, scans or polls. You get immediate, proactive, signature-less detection.
-
Response – Use a recorded history to see the full “kill chain” of an attack, and contain and stop attacks. When you need to respond to an alert or threat, you will instantly have the information you need to analyze, scope, contain, and remediate the problem. With the recorded details about every machine, you can “go back in time” to see what happened on any of your machines to understand the full “kill chain” of an attack. You will also have a copy of any binary that ever executed, so you can analyze it yourself, submit it to a third party, and so on. You can also contain and stop attacks by globally blocking the execution of any file automatically or with a single click.
-
Prevention via Carbon Black App Control – Stop attacks with proactive, signatureless prevention techniques by integrating Carbon Black App Control with Carbon Black EDR. With Carbon Black App Control, you can choose from different forms of advanced endpoint protection to match your business and systems. Carbon Black App Control’s proactive “Default-Deny” approach ensures that only software you trust can run on your machines. Carbon Black App Control’s “Detect-and-Deny” technology uses ATIs to detect malware and stop its execution, and Carbon Black App Control’s unique “Detonate-and-Deny” approach automatically can send every new file that arrives on any endpoint or server to leading network security tools for “detonation.” If a tool reports finding malicious files, Carbon Black App Control can automatically stop them from running on all of your machines.
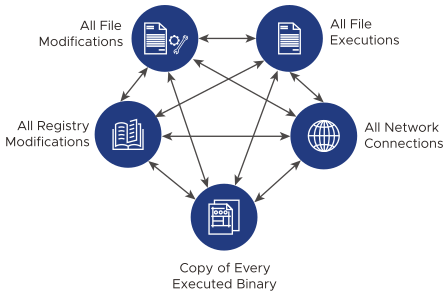
Carbon Black EDR accelerates detection by going beyond signatures, and reduces the cost and complexity of incident response. Using a real-time endpoint sensor, Carbon Black EDR delivers clear and accurate visibility and automates data acquisition by continuously recording and maintaining the relationships of every critical action on all machines, including events and event types such as executed binaries, registry modifications, file modifications, file executions, and network connections.
Carbon Black EDR provides a cross-process event type that records an occurrence of a process that crosses the security boundary of another process. While some of these events are benign, others can indicate an attempt to change the behavior of the target process by a malicious process.
Unlike scan-based security solutions, Carbon Black EDR can expand detection beyond the moment of compromise with its robust endpoint sensor and access to the information provided by Carbon Black Threat Intel.
Carbon Black Threat Intel provides three types of intelligence:
-
Carbon Black Threat Intel Reputation – A cloud-based intelligence database that provides highly accurate and up-to-date insight into known-good, known-bad, and unproven software. It provides IT and security teams with actionable intelligence about the software installed in their enterprise. The capabilities of the reputation service are further enhanced by feeds from third party partners.
-
Carbon Black EDR Threat Indicators – Search for patterns of behavior or indicators of malicious behavior. Unlike signature-based detection, threat indicators can recognize distinct attack characteristics, based on the relationships between network traffic, binaries, processes loaded, and user accounts. Carbon Black EDR also offers watchlists that are fully customizable saved searches that you can use to look for specific threat indicators.
-
Third Party Attack Classification – Uses intelligence feeds from third-party sources to help you identify the type of malware and the threat actor group behind an attack. This enables security teams to have a better understanding of attacks so that they can respond more quickly and effectively. You can also leverage your own intelligence feeds to enhance response capabilities.
Carbon Black EDR compares endpoint activity with the latest synchronization of Carbon Black Threat Intel feeds as it is reported. You can add intelligence feeds that you already have set up to give you zero-friction consumption of threat intelligence in Carbon Black EDR, regardless of the source.
Carbon Black EDR’s sensor is lightweight and can be easily deployed on every endpoint, requiring little to no configuration. This enables endpoint security analysts and incident responders to deploy thousands of sensors across their environment to immediately answer key response questions.
Carbon Black EDR’s continuously-recorded sensor data is stored in a central server, which lets your team see and understand the entire history of an attack, even if it deleted itself.
Carbon Black EDR integrates with leading network security providers. This integration enables you to prioritize alerts that are detected on the network by correlating them with events that occurred on endpoints and servers. This enables you to fully investigate your entire enterprise instantly to accelerate detection, reduce dwell time, minimize scope, and immediately respond to and contain advanced threats.
You can use Carbon Black EDR’s APIs to customize or integrate with existing security technologies that you are using, and Security Information and Event Management systems (SIEMs).
Carbon Black Hosted EDR includes extensive support for programmatic access to the underlying data and configuration through APIs.
Documentation, example scripts, and a helper library for each of these libraries is available at https://developer.carbonblack.com .