This topic provides search examples for process event searches on the Process Analysis page.
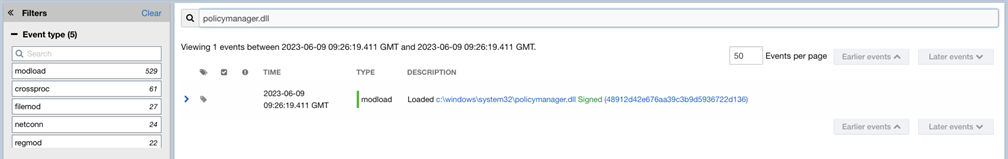
Example 1: Search Criteria Applied
In this example, the user wants to find module load (modload) events where c:\windows\system32\policymanager.dll was loaded. Even though modload is not selected in the Event type Filters facet, the user can find only modload events where c:\windows\system32\policymanager.dll was loaded by searching for policymanager.dll.
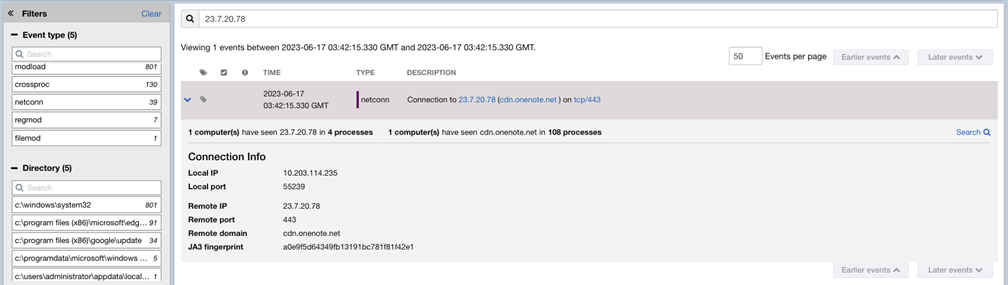
Example 2: Search Criteria Applied
In this example, the user wants to find network connection (netconn) events, where the Remote IP value equals 23.7.20.78.
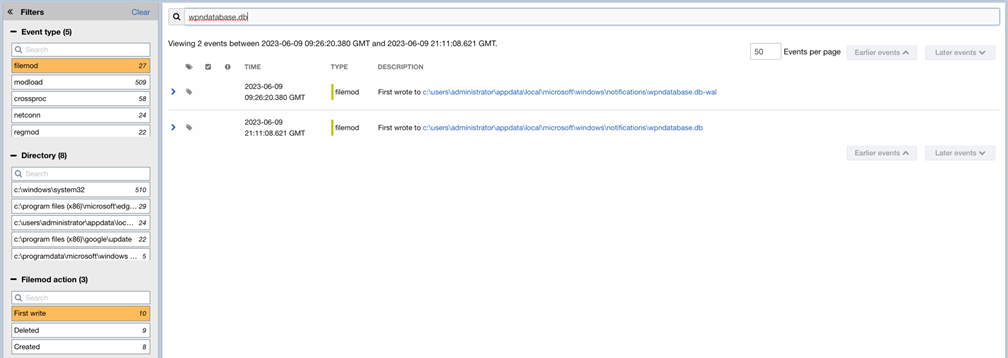
Example 3: Search and Filters Criteria Applied
In this example, the user wants to find file modification (filemod) events, where the Filemod action equals First write and the process first wrote to a file path that contains wpndatabase.db. The user can use Filters to filter by Event type = filemod and Filemod action = First write, and then the user can search for wpndatabase.db to further refine the search results to only those where the process first wrote to a file path that contains wpndatabase.db. As shown in the following image, two results are returned: one where the file name is wpndatabase.db, and one where the file name is wpndatabase.db-wal because both values match the search content.