This topic describes binary metadata for the process executable file.
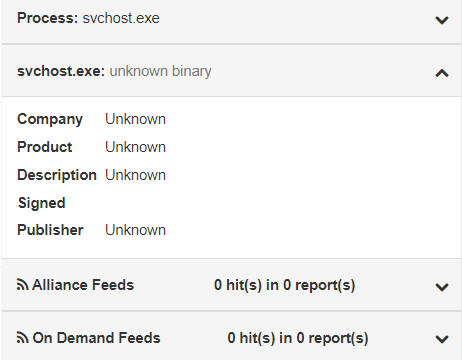
To view digital signature information and metadata about the process executable file, click the down-arrow next to the process executable file name at the bottom of the Process Execution Details panel:
For both Alliance Feeds and On Demand Feeds, only items that occur within the timeline selection window are displayed. For long-running processes, if the timeline selection window is large, Carbon Black might only report a subset of the Alliance and On Demand Feed hits. In this case, a message displays this status. The same limitations apply to the facets that are displayed.
Alliance Feeds shows if the process event details had any hits from Carbon Black Threat Intel partner feeds.
If there are any hits, the results appear below the Carbon Black Threat Intel feeds in rows that are expanded by default. Each row shows:
-
The source of the feed.
-
A link to information about the threat that was detected.
-
The date and score of the hit.
-
The IOC (Indicator of Compromise) value of the process event that caused the hit.
Click the IOC hash value to go directly to the process event row for that event.
On Demand Feeds shows if the process event details had any hits from on-demand feeds.
On-demand feeds provide information from the Carbon Black Threat Intel “on demand” when a process that is part of the Carbon Black Threat Intel database is viewed on the Process Analysis page. This information includes domain classification and threat geolocation. There might not be any on-demand data available for a process that you are analyzing.
Click the Sharing Settings link to access the Sharing page to set this up. For more information, see On-Demand Feeds from VMware CB Threat Intel.