This section describes how to review alerts on the Triage Alerts page in the Carbon Black EDR console.
Each row in the Alerts table shows the description and data for an individual alert. The description and data that appears can vary depending on a variety of factors, including:
The source and type of the alert.
Whether the binary for a process has been signed.
Whether a binary is “Trusted” by the Carbon Black EDR Alliance.
The Alerts table has multiple tools for adjusting the table display:
Sort order – You can sort the Alerts table using the Sort By button You can sort by:
Severity (default)
Most Recent
Least Recent
Alert Name Ascending
Alert Name Descending
Page navigator – You can use the page navigation bar in the bottom-right corner of the Alerts table to move between pages for table views that do not fit on a single page.
Alerts Table Data
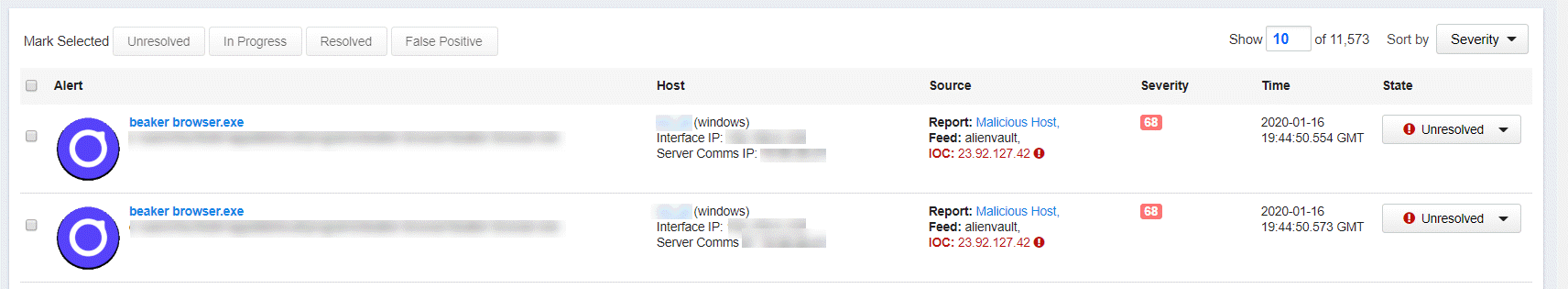
- Alert – Contains the following details:
- An icon that represents the process or binary that caused the threat alert, if available. If there is no special icon for this binary, a generic file icon is used.
Note: Tamper alerts show what feed is triggered; the icon is of the host type.
- The directory path where the process or binary is installed.
- If this is a binary, the blue process link takes you to the Binary Details page. If this is a process, the blue process link takes you to the Process Analysis page.
- An icon that represents the process or binary that caused the threat alert, if available. If there is no special icon for this binary, a generic file icon is used.
- Host – Shows host details and a link to the Sensor Details page.
- Source – The watchlist or feed that triggered the alert with a link to that watchlist or feed.
- Severity – The severity score of the alert that Carbon Black EDR produces based on underlying alert data. Click the Severity number to show additional details by which the severity is calculated:
-
Feed rating
-
Report scores
-
Confidence
-
Criticality
The Severity numbers are color-coded, with red being severe threats and green being low threats. A score of 100 represents the most severe alerts.
-
- Time – The time when the alert was triggered.
- State – The alert state, which includes:
-
Mark as Resolved – Select this when the alert is resolved.
-
Mark as Unresolved – By default, only unresolved alerts are displayed.
-
Mark as In-Progress – Select this for alerts that have resolutions in progress.
-
Mark as False Positive – Select this for alerts that were not true threats.
-