This section describes how to perform basic process searches using search strings and predefined search criteria.
When you become aware of an incident that could be a threat, you can search all your systems and endpoints for processes that have Indicators of Compromise (IOCs). For example, you might receive a call reporting unusual software behavior or an alert from a threat intelligence report or watchlist. Carbon Black EDR sensors automatically collect data so that you can immediately start analyzing issues and finding solutions.
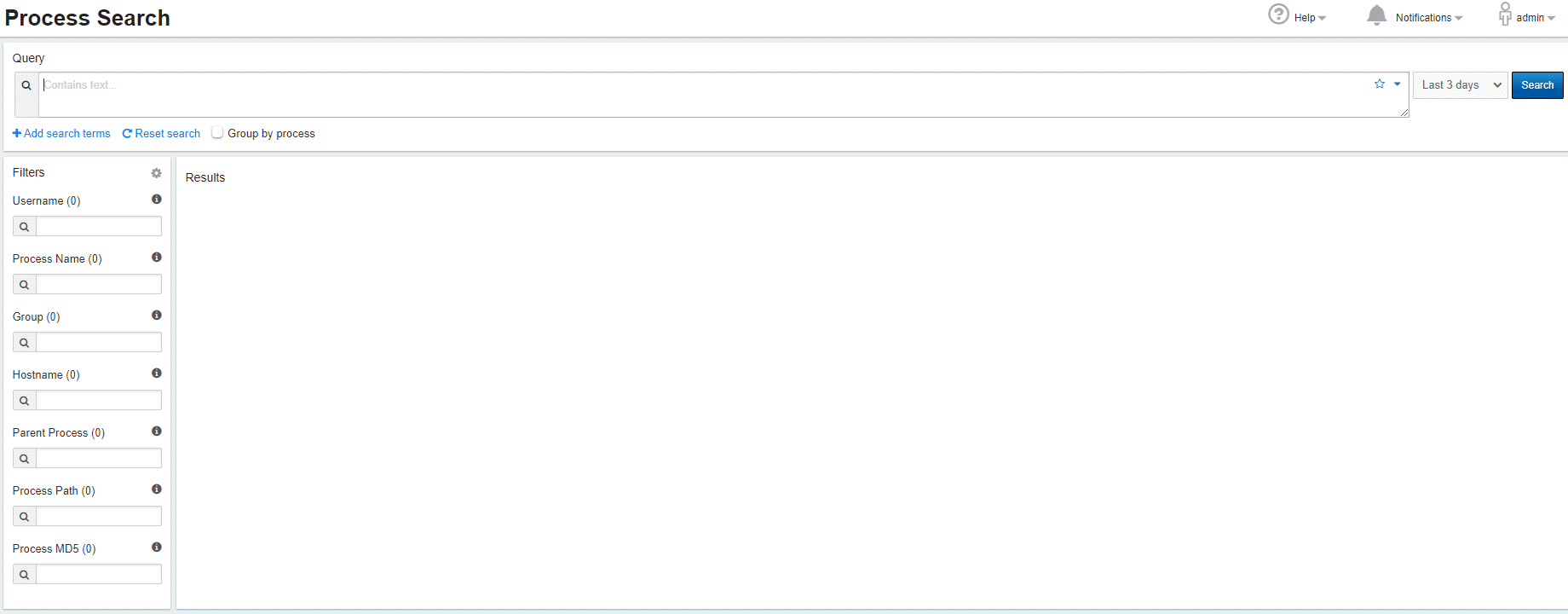
Use the Process Search page to begin investigating potential threats. On the navigation bar, click Process Search.