VMware Cloud Director uses SSL handshakes to secure communications between clients and servers.
Signed certificates are signed by authorized Certificate Authorities (CA) and, as long as the local OS truststore has a copy of the root and of the intermediate certificates of the CA, they are trusted by browsers. Some CAs require that you submit the requirements for a certificate, others require you to submit a Certificate Signing Request (CSR). In both scenarios, you are creating a self-signed certificate, and you generate a CSR that is based on that certificate. The CA signs your certificate with their private key, which you can then decrypt with your copy of their public key, and establish a trust.
When you renew an expired SSL certificate, you don't need to provide VMware Cloud Director with any data about the expired certificate. This means that after you import the required SSL certificates into the VMware Cloud Director appliance, you don't need to back them up.
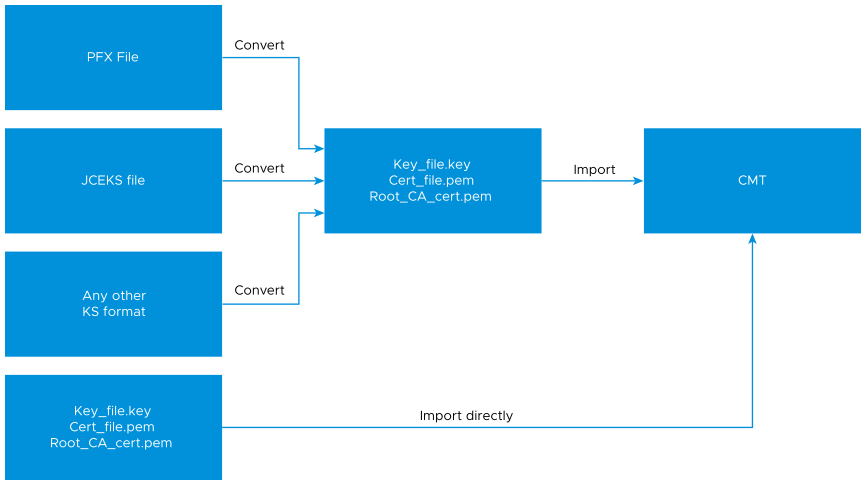
You can import PEM files directly into the VMware Cloud Director appliance. If your certificate files are in another format, you can use OpenSSL to convert them to PEM before importing them to VMware Cloud Director with the cell management tool.
- If you want to deploy a VMware Cloud Director with signed wildcard certificates, see Deploy Your VMware Cloud Director 10.5.0 Appliance with a Signed Wildcard Certificate for HTTPS Communication.
- If you want to replace the self-signed certificates of a newly deployed appliance with CA-signed certificates. see Import Private Keys and CA-Signed SSL Certificates to Your VMware Cloud Director 10.5.0 Appliance.
- If you want to create CA-signed certificates and import them to the VMware Cloud Director appliance, see Create and Import CA-Signed SSL Certificates for Your VMware Cloud Director 10.5.0 Appliance.
- If you want to renew the certificates for HTTPS communication of VMware Cloud Director, as well as for the embedded PostgreSQL database and theVMware Cloud Director appliance management UI, see Renew Your VMware Cloud Director 10.5.0 Appliance Certificates.