Starting with version 10.5.1, VMware Cloud Director offers support for NSX multitenancy by mapping organizations directly to NSX projects.
You can learn more about NSX projects by familiarizing yourself with the relevant NSX Projects documentation in the NSX Administration Guide.
To use NSX tenancy in the context of VMware Cloud Director, begin by activating NSX tenancy for an organization.
After that, you can opt in or out of using NSX tenancy when you create VDCs in this organization. The NSX project is actually created during the creation of the first VDC in the organization for which you activated NSX tenancy. The name of the NSX project is the same as the name of the organization to which it is mapped.
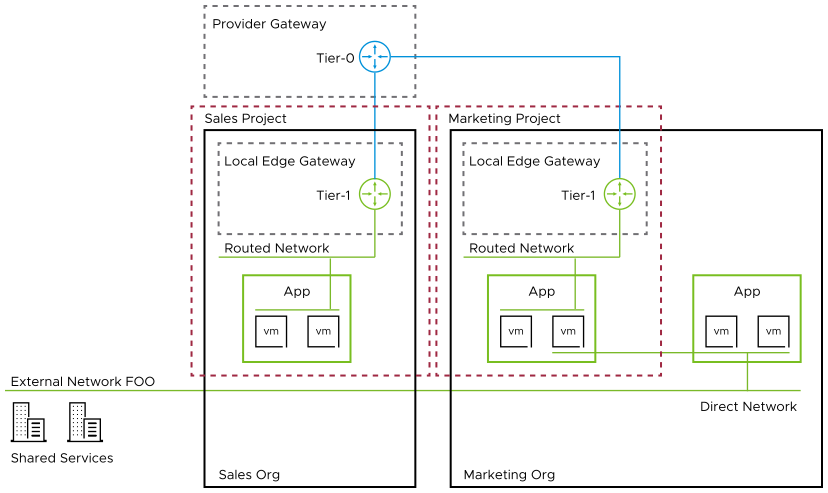
In the diagram, the Sales and Marketing VMware Cloud Director organizations are mapped to the corresponding NSX projects. All NSX components created within the organization context are part of the NSX project. The provider (tier-0) gateway is associated to the NSX project but it is not part of it, providing connectivity to local edge gateways and to direct NSX networks, if necessary. An external network connection is available to the Marketing Org through a direct network. There are no restrictions on whether the backing segments for the imported and external networks are within the NSX project or not.
If you choose not to activate NSX tenancy during the creation of an organization VDC, you cannot change this setting later.
Some use cases do not require organization VDC participation in NSX tenancy, for example, if the VDC only needs VLAN networks. Additionally, organization VDCs using NSX tenancy are restricted to using the network pool that is backed by the default overlay transport zone, so, in order to be able to use a different network pool, you might wish to opt out of NSX tenancy.
If you opt into NSX tenancy during the creation of an organization VDC, you cannot change its network pool later. However, you may still add external network connections to edge gateways and create imported networks within the VDC.
You can deactivate NSX tenancy for an organization only after you delete all its affiliated VDCs and data center groups with active NSX tenancy.
When you enable NSX tenancy for an organization, any organization VDCs that you create after that have NSX tenancy enabled by default. For existing organization VDCs and VDC groups, NSX tenancy is not enabled.
Data Center Group Networking
When a tenant creates a data center group, if the starting VDC uses NSX tenancy, then the data center group will use NSX tenancy as well. The tenant can scope edge gateways to the data center group only if the edge gateways are also using NSX tenancy and if they belong to the same organization as the data center group.
Tenants can create data center groups that include both organization VDCs that are using NSX tenancy and VDCs that aren't using NSX tenancy.
In a multisite context, tenants can create data center groups that include organization VDCs from associated organizations. In this case, all networking and security components in the data center group remain within the NSX project of the starting organization VDC.
Because the NSX project is mapped to the organization of the starting VDC, in this kind of mixed data center groups, distributed firewall rules and security groups are all deployed within the context of the NSX project.
Note that associated organizations can have their own NSX, but these have no impact on the DC group networks. VMs and vApps can connect to these DC networks and to local networks that are not part of the project at the same time.
Caveats and Limitations
Not all VMware Cloud Director networking features are supported within the context of NSX tenancy. To learn more, see the full list of the Features Available for Consumption under NSX Projects.
Activate NSX Tenancy for an Organization in VMware Cloud Director Service Provider Admin Portal
To use NSX tenancy in the context of VMware Cloud Director, first you define the NSX project in VMware Cloud Director by activating NSX tenancy for an organization.
Prerequisites
- Verify that you configured a default overlay transport zone in NSX. See Create Transport Zones in the NSX Installation Guide
- Verify that you created a network pool that is backed by the default overlay transport zone that you created. See Geneve Network Pools in Your VMware Cloud Director.
- Verify that your role includes the Organization: Edit Properties right.
Procedure
What to do next
- Create an Organization VDC That Uses NSX Tenancy.
- To use vApp network services within the project, assign an edge cluster to the organization VDC that uses NSX tenancy. See Assign an Edge Cluster to a VMware Cloud Director Organization Virtual Data Center
- Create an NSX edge gateway scoped to the organization VDC. See Add an Edge Gateway Backed by an NSX Provider Gateway in VMware Cloud Director.