Network Segment
This network design has the following features:
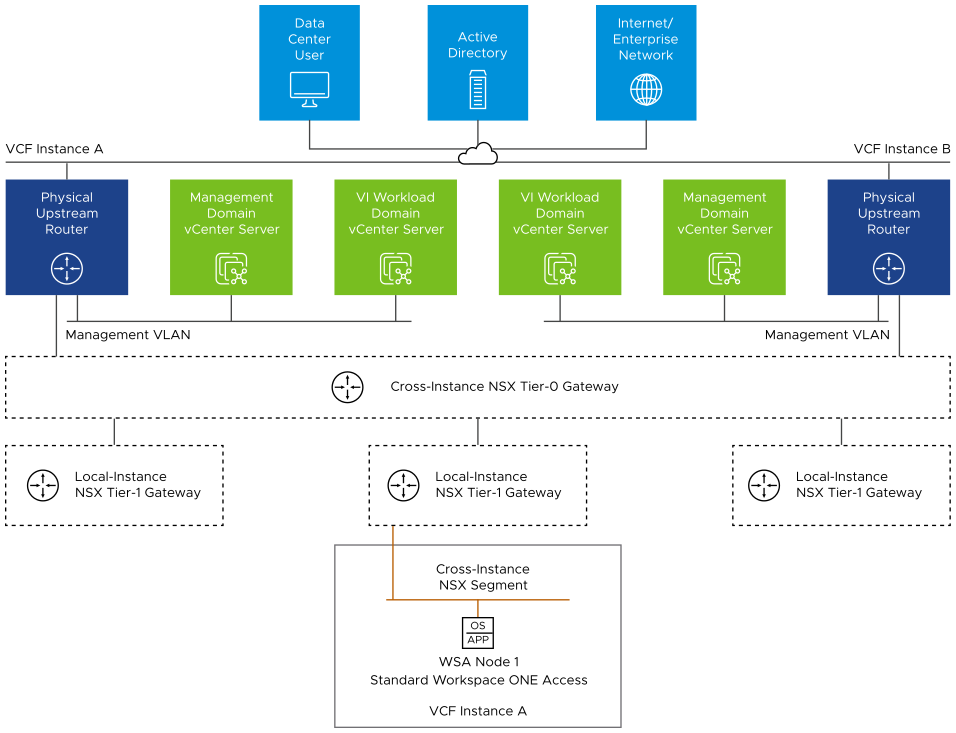
All Workspace ONE Access components have routed access to the management VLAN through the Tier-0 gateway in the NSX-T Data Center instance for the management domain.
Routing to the management network and other external networks is dynamic and is based on the Border Gateway Protocol (BGP).

Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-001 |
Place the Workspace ONE Access appliances on an overlay-backed or VLAN-backed NSX network segment. |
Provides a consistent deployment model for management applications in an environment with a single or multiple VMware Cloud Foundation instances. |
You must use an implementation in NSX-T Data Center to support this network configuration. |
IP Addressing Scheme
Allocate a statically assigned IP address and a host name from the cross-instance NSX segment to the components required for Workspace ONE Access.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-002 |
Allocate statically assigned IP addresses for the following:
|
Using statically assigned IP addresses ensures stability across the SDDC and makes it simpler to maintain and easier to track. |
Requires precise IP address management. |
Name Resolution
The IP address of each component required for Workspace ONE Access is associated with a fully qualified name whose suffix aligns with your domain name and must have valid DNS forward (A) and reverse (PTR) records.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-003 |
Configure forward and reverse DNS records for the following components:
|
Workspace ONE Access is accessible by using a set of fully qualified domain names instead of by using only IP address. |
|
VCF-VRS-WSA-NET-004 |
Configure the DNS settings for Workspace ONE Access to use DNS servers in the first VMware Cloud Foundation instance. |
Workspace ONE Access requires DNS resolution to connect to SDDC Components. |
None. |
Name Resolution for Workspace ONE Access for Multiple VMware Cloud Foundation Instances
In an environment with multiple VMware Cloud Foundation instances, multiple DNS servers are available across the instances, providing higher DNS availability and resilience.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-005 |
Configure the DNS settings for Workspace ONE Access to use DNS servers in each VMware Cloud Foundation instance. |
Improves resiliency if an outage of a DNS server occurs. |
None. |
Time Synchronization
Workspace ONE Access depends on time synchronization.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-006 |
Configure the NTP settings on Workspace ONE Access to use NTP servers in the first VMware Cloud Foundation instance. |
Workspace ONE Access depends on time synchronization for all cluster nodes. |
None. |
Time Synchronization for Workspace ONE Access for Multiple VMware Cloud Foundation Instances
In an environment with multiple VMware Cloud Foundation instances, multiple NTP servers are available across the instances, providing higher NTP availability and resilience.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-007 |
Configure the NTP settings on Workspace ONE Access cluster nodes to use NTP servers in each VMware Cloud Foundation instance. |
Improves resiliency in the event of an outage of an NTP server. |
If you scale from a deployment with a single VMware Cloud Foundation instance to one with multiple VMware Cloud Foundation instances, the NTP settings on Workspace ONE Access must be updated. |
Load Balancing
A Workspace ONE Access cluster deployment requires a load balancer to manage connections to the Workspace ONE Access services.
Load-balancing services are provided by NSX-T Data Center. During the deployment of the Workspace ONE Access cluster or scale-out of a standard deployment, vRealize Suite Lifecycle Manager and SDDC Manager coordinate to automate the configuration of the NSX load balancer. The load balancer is configured with the settings outlined in the table below.
Load Balancer Element |
Settings |
|---|---|
Service Monitor |
|
Server Pool |
|
HTTP Application Profile |
|
Cookie Persistence Profile |
|
Virtual Server |
|
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
VCF-VRS-WSA-NET-008 |
Use the NSX load balancer that is configured by SDDC Manager on a dedicated Tier-1 gateway to load balance connections across the Workspace ONE Access cluster nodes. |
|
You must use the load balancer that is configured by SDDC Manager and the integration with vRealize Suite Lifecycle Manager. |