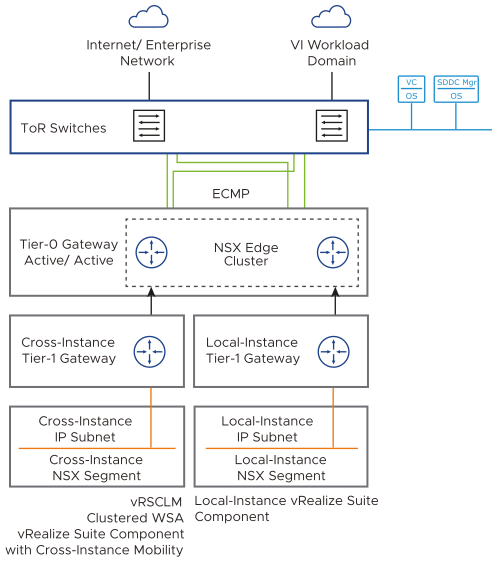
In VMware Cloud Foundation, you place vRealize Suite components on a pre-defined configuration of NSX segments (known as application virtual networks or AVNs) for dynamic routing and load balancing.
Logical Application Virtual Network Design VMware Cloud Foundation
NSX segments provide flexibility for workload placement by removing the dependence on traditional physical data center networks. This approach also improves security and mobility of the management applications, and reduces the integration effort with existing customer network.
Design Component |
Overlay-Based NSX Segments |
VLAN-Backed NSX Segments |
|---|---|---|
Benefits |
|
Uses the data center fabric for the network segment and the next-hop gateway. |
Requirement |
Requires routing between the data center fabric and the NSX Edge nodes. |
|
For the design for specific vRealize Suite components, see this design and VMware Validated Solutions. For identity and access management design for NSX, see Identity and Access Management for VMware Cloud Foundation.
If you plan to use NSX Federation in the management domain, create the AVNs before you enable the federation. Creating AVNs in an environment where NSX Federation is already active is not supported.
With NSX Federation, an NSX segment can span multiple instances of NSX and VMware Cloud Foundation. A single network segment can be available in different physical locations over the NSX SDN. In an environment with multiple VMware Cloud Foundation instances, the cross-instance NSX network in the management domain is extended between the first two instances. This configuration provides IP mobility for management components which fail over from the first to the second instance.
Application Virtual Network Design Requirements and Recommendations forVMware Cloud Foundation
Consider the requirements and best practices for the configuration of the NSX segments for using the Application Virtual Networks in VMware Cloud Foundation for a single VMware Cloud Foundation or multiple VMware Cloud Foundation instances.
Application Virtual Network Design Requirements
You must meet the following design requirements in your Application Virtual Network design for a single VMware Cloud Foundation instance and for multiple VMware Cloud Foundation instances.
Requirement ID |
Design Requirement |
Justification |
Implication |
|---|---|---|---|
VCF-NSX-AVN-REQD-CFG-001 |
Create one cross-instance NSX segment for the components of a vRealize Suite application or another solution that requires mobility between VMware Cloud Foundation instances. |
Prepares the environment for the deployment of solutions on top of VMware Cloud Foundation, such as vRealize Suite, without a complex physical network configuration. The components of the vRealize Suite application must be easily portable between VMware Cloud Foundation instances without requiring reconfiguration. |
Each NSX segment requires a unique IP address space. |
VCF-NSX-AVN-REQD-CFG-002 |
Create one or more local-instance NSX segments for the components of a vRealize Suite application or another solution that are assigned to a specific VMware Cloud Foundation instance. |
Prepares the environment for the deployment of solutions on top of VMware Cloud Foundation, such as vRealize Suite, without a complex physical network configuration. |
Each NSX segment requires a unique IP address space. |
Requirement ID |
Design Requirement |
Justification |
Implication |
|---|---|---|---|
VCF-NSX-AVN-REQD-CFG-003 |
Extend the cross-instance NSX segment to the second VMware Cloud Foundation instance. |
Enables workload mobility without a complex physical network configuration. The components of a vRealize Suite application must be easily portable between VMware Cloud Foundation instances without requiring reconfiguration. |
Each NSX segment requires a unique IP address space. |
VCF-NSX-AVN-REQD-CFG-004 |
In each VMware Cloud Foundation instance, create additional local-instance NSX segments. |
Enables workload mobility within a VMware Cloud Foundation instance without complex physical network configuration. Each VMware Cloud Foundation instance should have network segments to support workloads which are isolated to that VMware Cloud Foundation instance. |
Each NSX segment requires a unique IP address space. |
VCF-NSX-AVN-REQD-CFG-005 |
In each VMware Cloud Foundation instance, connect or migrate the local-instance NSX segments to the corresponding local-instance Tier-1 gateway. |
Configures local-instance NSX segments at required sites only. |
Requires an individual Tier-1 gateway for local-instance segments. |
Application Virtual Network Design Recommendations
In your Application Virual Network design for VMware Cloud Foundation, you can apply certain best practices.
Recommendation ID |
Design Recommendation |
Justification |
Implication |
|---|---|---|---|
VCF-NSX-AVN-RCMD-CFG-001 |
Use overlay-backed NSX segments. |
|
Using overlay-backed NSX segments requires routing, eBGP recommended, between the data center fabric and edge nodes. |