Workspace ONE Access in VMware Cloud Foundation mode provides identity and access management services to specific components in the SDDC, such as VMware Aria Suite.
Workspace ONE Access provides the following capabilities:
Directory integration to authenticate users against an identity provider (IdP), such as Active Directory or LDAP.
Multiple authentication methods.
Access policies that consist of rules to specify criteria that users must meet to authenticate.
The Workspace ONE Access instance that is integrated with VMware Aria Suite Lifecycle provides identity and access management services to VMware Aria Suite solutions that either run in a VMware Cloud Foundation instance or must be available across VMware Cloud Foundation instances.
For identity management design for a VMware Aria Suite product, see VMware Cloud Foundation Validated Solutions .
For identity and access management for components other than VMware Aria Suite, such as NSX, you can deploy a standalone Workspace ONE Access instance. See Identity and Access Management for VMware Cloud Foundation.
Logical Design for Workspace ONE Access
To provide identity and access management services to supported SDDC components, such as VMware Aria Suite components, this design uses a Workspace ONE Access instance that is deployed on an NSX network segment.
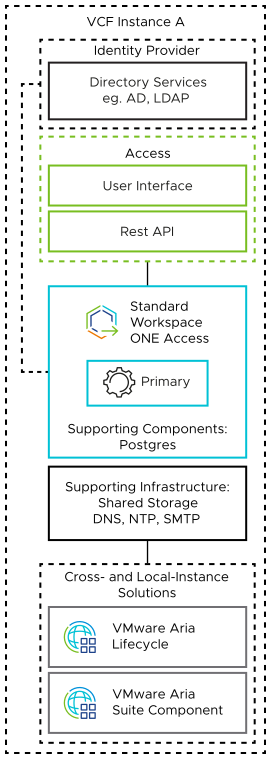
VMware Cloud Foundation Instances with a Single Availability Zone |
VMware Cloud Foundation Instances with Multiple Availability Zones |
|---|---|
|
|
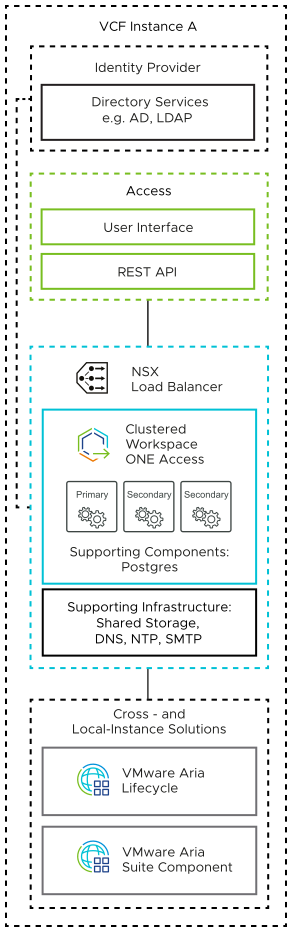
VMware Cloud Foundation Instances with a Single Availability Zone |
VMware Cloud Foundation Instances with Multiple Availability Zones |
|---|---|
|
|
Sizing Considerations for Workspace ONE Access for VMware Cloud Foundation
When you deploy Workspace ONE Access, you select to deploy the appliance with a size that is suitable for the scale of your environment. The option that you select determines the number of CPUs and the amount of memory of the appliance.
For detailed sizing based on the overall profile of the VMware Cloud Foundation instance you plan to deploy, see VMware Cloud Foundation Planning and Preparation Workbook.
| Workspace ONE Access Appliance Size |
Supported Limits |
|---|---|
| Extra Small |
|
| Small |
|
| Medium |
A minimum requirement for VMware Aria Automation |
| Large |
|
| Extra Large |
|
| Extra Extra Large |
|
Network Design for Workspace ONE Access
For secure access to the UI and API of Workspace ONE Access, you deploy the nodes on an overlay-backed or VLAN-backed NSX network segment.
Network Segment
This network design has the following features:
All Workspace ONE Access components have routed access to the management VLAN through the Tier-0 gateway in the NSX instance for the management domain.
Routing to the management network and other external networks is dynamic and is based on the Border Gateway Protocol (BGP).
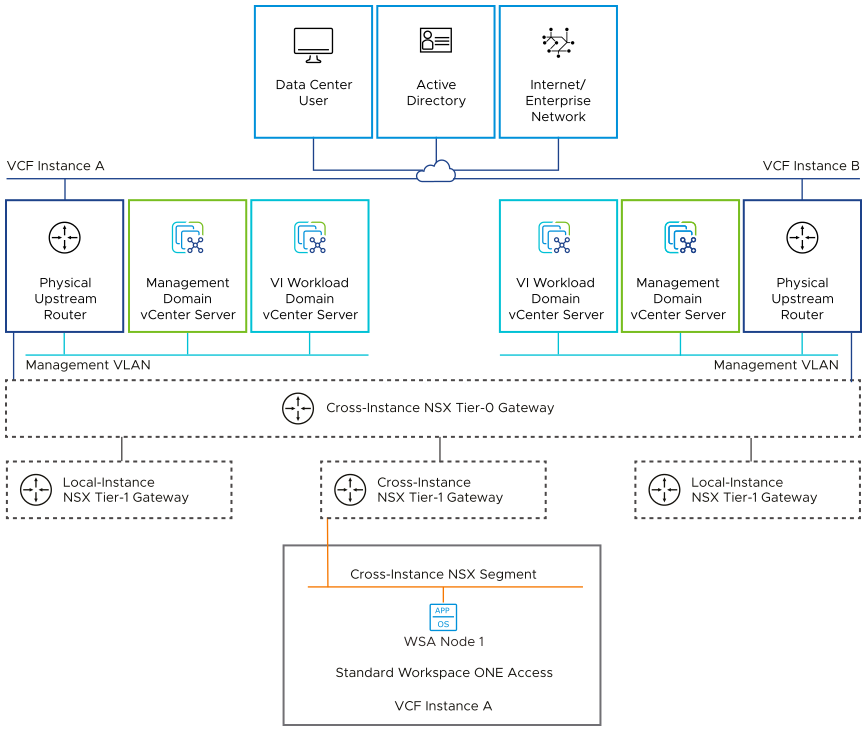
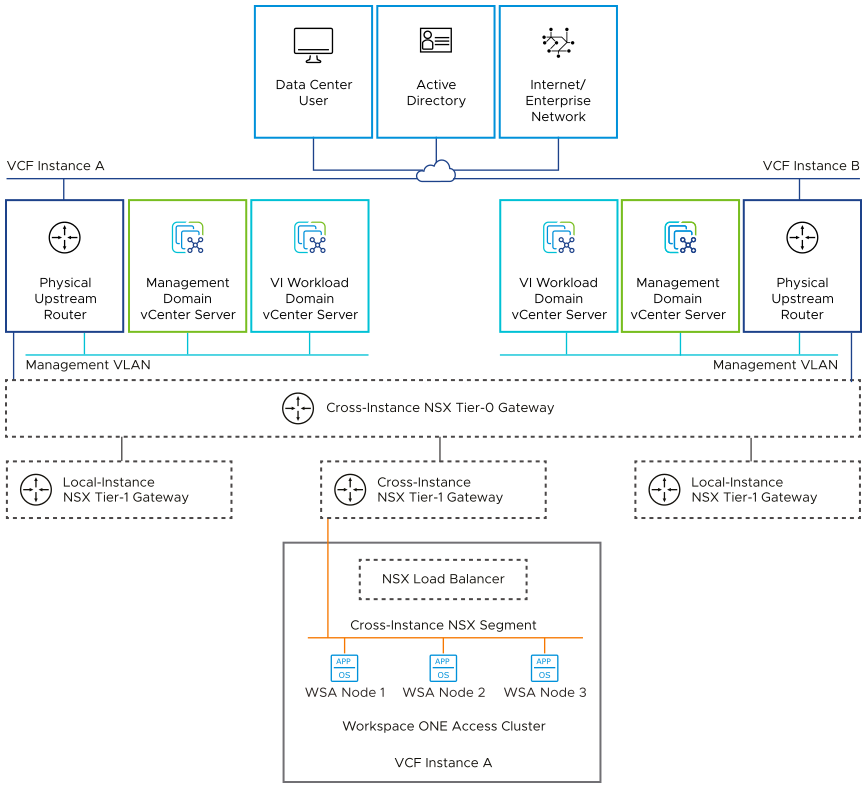
Load Balancing
A Workspace ONE Access cluster deployment requires a load balancer to manage connections to the Workspace ONE Access services.
Load-balancing services are provided by NSX. During the deployment of the Workspace ONE Access cluster or scale-out of a standard deployment, VMware Aria Suite Lifecycle and SDDC Manager coordinate to automate the configuration of the NSX load balancer. The load balancer is configured with the following settings:
Load Balancer Element |
Settings |
|---|---|
Service Monitor |
|
Server Pool |
|
HTTP Application Profile |
|
Cookie Persistence Profile |
|
Virtual Server |
|
Integration Design for Workspace ONE Access with VMware Cloud Foundation
You integrate supported SDDC components with the Workspace ONE Access cluster to enable authentication through the identity and access management services.
After the integration, information security and access control configurations for the integrated SDDC products can be configured.
SDDC Component |
Integration |
Considerations |
|---|---|---|
vCenter Server |
Not Supported |
For directory services you must connect vCenter Server directly to Active Directory. See Identity and Access Management for VMware Cloud Foundation. |
SDDC Manager |
Not Supported |
SDDC Manager uses vCenter Single Sign-On. For directory services, you must connect vCenter Server directly to Active Directory |
NSX |
Supported |
If you intend to scale out to an environment with multiple VMware Cloud Foundation instances, for example, for disaster recovery, you must deploy an additional standard instance of Workspace ONE Access in each VMware Cloud Foundation instance. The Workspace ONE Access instance that is leveraged by components protected across VMware Cloud Foundation instances might fail over between physical locations which will impact the authentication to NSX in the first VMware Cloud Foundation instance. See Identity and Access Management for VMware Cloud Foundation. |
VMware Aria Suite Lifecycle |
Supported |
None. |
See VMware Cloud Foundation Validated Solutions for the design for specific VMware Aria Suite components including identity management.
Deployment Model for Workspace ONE Access
Workspace ONE Access is distributed as a virtual appliance in OVA format that you can deploy and manage from VMware Aria Suite Lifecycle together with other VMware Aria Suite products. The Workspace ONE Access appliance includes identity and access management services.
Deployment Type
You consider the deployment type, standard or cluster, according to the design objectives for the availability and number of users that the system and integrated SDDC solutions must support. You deploy Workspace ONE Access on the default management vSphere cluster.
Deployment Type |
Description |
Benefit |
Drawbacks |
|---|---|---|---|
Standard |
|
|
|
Cluster |
|
|
|
Workspace ONE Access Design Requirements and Recommendations for VMware Cloud Foundation
Consider the placement, networking, sizing and high availability requirements for using Workspace ONE Access for identity and access management of SDDC solutions on a standard or stretched management cluster in VMware Cloud Foundation. Apply similar best practices for having Workspace ONE Access operate in an optimal way.
Workspace ONE Access Design Requirements
You must meet the following design requirements in your Workspace ONE Access design for VMware Cloud Foundation, considering standard or stretched clusters. For NSX Federation, additional requirements exist.
Requirement ID |
Design Requirement |
Justification |
Implication |
|---|---|---|---|
VCF-WSA-REQD-ENV-001 |
Create a global environment in VMware Aria Suite Lifecycle to support the deployment of Workspace ONE Access. |
A global environment is required by VMware Aria Suite Lifecycle to deploy Workspace ONE Access. |
None. |
VCF-WSA-REQD-SEC-001 |
Import certificate authority-signed certificates to the Locker repository for Workspace ONE Access product life cycle operations. |
|
When using the API, you must specify the Locker ID for the certificate to be used in the JSON payload. |
VCF-WSA-REQD-CFG-001 |
Deploy an appropriately sized
Workspace ONE Access instance according to the deployment model you have selected by using
VMware Aria Suite Lifecycle in
VMware Cloud Foundation mode.
|
The Workspace ONE Access instance is managed by VMware Aria Suite Lifecycle and imported into the SDDC Manager inventory. |
None. |
VCF-WSA-REQD-CFG-002 |
Place the Workspace ONE Access appliances on an overlay-backed or VLAN-backed NSX network segment. |
Provides a consistent deployment model for management applications in an environment with a single or multiple VMware Cloud Foundation instances. |
You must use an implementation in NSX to support this network configuration. |
VCF-WSA-REQD-CFG-003 |
Use the embedded PostgreSQL database with Workspace ONE Access. |
Removes the need for external database services. |
None. |
VCF-WSA-REQD-CFG-004 |
Add a VM group for Workspace ONE Access and set VM rules to restart the Workspace ONE Access VM group before any of the VMs that depend on it for authentication. |
You can define the startup order of virtual machines regarding the service dependency. The startup order ensures that vSphere HA powers on the Workspace ONE Access virtual machines in an order that respects product dependencies. |
None. |
VCF-WSA-REQD-CFG-005 |
Connect the Workspace ONE Access instance to a supported upstream Identity Provider. |
You can integrate your enterprise directory with Workspace ONE Access to synchronize users and groups to the Workspace ONE Access identity and access management services. |
None. |
VCF-WSA-REQD-CFG-006 |
If using clustered Workspace ONE Access, configure second and third native connectors that correspond to the second and third Workspace ONE Access cluster nodes to support the high availability of directory services access. |
Adding the additional native connectors provides redundancy and improves performance by load-balancing authentication requests. |
Each of the Workspace ONE Access cluster nodes must be joined to the Active Directory domain to use Active Directory with Integrated Windows Authentication with the native connector. |
VCF-WSA-REQD-CFG-007 |
If using clustered Workspace ONE Access, use the NSX load balancer that is configured by SDDC Manager on a dedicated Tier-1 gateway. |
|
You must use the load balancer that is configured by SDDC Manager and the integration with VMware Aria Suite Lifecycle. |
Requirement ID |
Design Requirement |
Justification |
Implication |
|---|---|---|---|
VCF-WSA-REQD-CFG-008 |
Add the Workspace ONE Access appliances to the VM group for the first availability zone. |
Ensures that, by default, the Workspace ONE Access cluster nodes are powered on a host in the first availability zone. |
|
Requirement ID |
Design Requirement |
Justification |
Implication |
|---|---|---|---|
VCF-WSA-REQD-CFG-009 |
Configure the DNS settings for Workspace ONE Access to use DNS servers in each VMware Cloud Foundation instance. |
Improves resiliency if an outage of external services for a VMware Cloud Foundation instance occurs. |
None. |
VCF-WSA-REQD-CFG-010 |
Configure the NTP settings on Workspace ONE Access cluster nodes to use NTP servers in each VMware Cloud Foundation instance. |
Improves resiliency if an outage of external services for a VMware Cloud Foundation instance occurs. |
If you scale from a deployment with a single VMware Cloud Foundation instance to one with multiple VMware Cloud Foundation instances, the NTP settings on Workspace ONE Access must be updated. |
Workspace ONE Access Design Recommendations
In your Workspace ONE Access design for VMware Cloud Foundation, you can apply certain best practices.
Recommendation ID |
Design Recommendation |
Justification |
Implication |
|---|---|---|---|
VCF-WSA-RCMD-CFG-001 |
Protect all Workspace ONE Access nodes using vSphere HA. |
Supports high availability for Workspace ONE Access. |
None for standard deployments. Clustered Workspace ONE Access deployments might require intervention if an ESXi host failure occurs. |
VCF-WSA-RCMD-CFG-002 |
When using Active Directory as an Identity Provider, use Active Directory over LDAP as the Directory Service connection option. |
The native (embedded) Workspace ONE Access connector binds to Active Directory over LDAP using a standard bind authentication. |
|
VCF-WSA-RCMD-CFG-003 |
When using Active Directory as an Identity Provider, use an Active Directory user account with a minimum of read-only access to Base DNs for users and groups as the service account for the Active Directory bind. |
Provides the following access control features:
|
|
VCF-WSA-RCMD-CFG-004 |
Configure the directory synchronization to synchronize only groups required for the integrated SDDC solutions. |
|
You must manage the groups from your enterprise directory selected for synchronization to Workspace ONE Access. |
VCF-WSA-RCMD-CFG-005 |
Activate the synchronization of enterprise directory group members when a group is added to the Workspace ONE Access directory. |
When activated, members of the enterprise directory groups are synchronized to the Workspace ONE Access directory when groups are added. When deactivated, group names are synchronized to the directory, but members of the group are not synchronized until the group is entitled to an application or the group name is added to an access policy. |
None. |
VCF-WSA-RCMD-CFG-006 |
Enable Workspace ONE Access to synchronize nested group members by default. |
Allows Workspace ONE Access to update and cache the membership of groups without querying your enterprise directory. |
Changes to group membership are not reflected until the next synchronization event. |
VCF-WSA-RCMD-CFG-007 |
Add a filter to the Workspace ONE Access directory settings to exclude users from the directory replication. |
Limits the number of replicated users for Workspace ONE Access within the maximum scale. |
To ensure that replicated user accounts are managed within the maximums, you must define a filtering schema that works for your organization based on your directory attributes. |
VCF-WSA-RCMD-CFG-008 |
Configure the mapped attributes included when a user is added to the Workspace ONE Access directory. |
You can configure the minimum required and extended user attributes to synchronize directory user accounts for the Workspace ONE Access to be used as an authentication source for cross-instance VMware Aria Suite solutions. |
User accounts in your organization's enterprise directory must have the following required attributes mapped:
|
VCF-WSA-RCMD-CFG-009 |
Configure the Workspace ONE Access directory synchronization frequency to a reoccurring schedule, for example, 15 minutes. |
Ensures that any changes to group memberships in the corporate directory are available for integrated solutions in a timely manner. |
Schedule the synchronization interval to be longer than the time to synchronize from the enterprise directory. If users and groups are being synchronized to Workspace ONE Access when the next synchronization is scheduled, the new synchronization starts immediately after the end of the previous iteration. With this schedule, the process is continuous. |
VCF-WSA-RCMD-SEC-001 |
Create corresponding security groups in your corporate directory services for these Workspace ONE Access roles:
|
Streamlines the management of Workspace ONE Access roles to users. |
|
VCF-WSA-RCMD-SEC-002 |
Configure a password policy for Workspace ONE Access local directory users, admin and configadmin. |
You can set a policy for Workspace ONE Access local directory users that addresses your corporate policies and regulatory standards. The password policy is applicable only to the local directory users and does not impact your organization directory. |
You must set the policy in accordance with your organization policies and regulatory standards, as applicable. You must apply the password policy on the Workspace ONE Access cluster nodes. |