The network design details the design decisions for the network segment placement, IP addressing, name resolution, and time synchronization for the VMware Live Cyber Recovery Connector appliances.
Network Segments
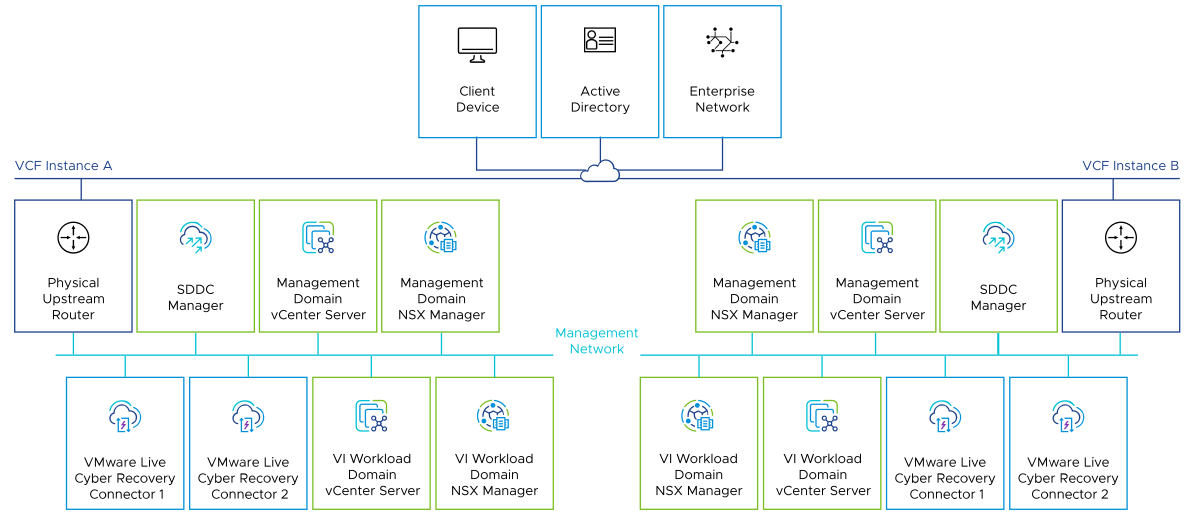
The network segment design consists of characteristics and decisions for placement of the VMware Live Cyber Recovery Connector appliances in the management domain.
This validated solution places the VMware Live Cyber Recovery Connector appliances within the management VLAN of the VMware Cloud Foundation instance. This ensures connectivity and close proximity to vCenter Server.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
CBR-CDP-NET-001 |
Place the VMware Live Cyber Recovery Connector appliances on the management VLAN. |
|
None. |
IP Addressing
Allocate statically assigned IP addresses and host names to the VMware Live Cyber Recovery Connector appliances from their corresponding network.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
CBR-CDP-NET-002 |
Allocate statically assigned IP addresses from the management VLAN to the VMware Live Cyber Recovery Connector appliances. |
Using statically assigned IP addresses ensures stability of the deployment and simplifies maintenance and tracking. |
Requires precise IP address management. |
Name Resolution
Name resolution provides the translation between an IP address and a fully qualified domain name (FQDN), which makes it easier to remember and connect to components across the SDDC. The IP address of each VMware Live Cyber Recovery Connector appliance must have a valid internal DNS forward (A) and reverse (PTR) records.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
CBR-CDP-NET-003 |
Configure forward and reverse DNS records for the VMware Live Cyber Recovery Connector appliance IP addresses. |
Ensures the appliances are accessible by using a fully qualified domain name instead of using IP addresses only. |
|
CBR-CDP-NET-004 |
Configure DNS servers on the VMware Live Cyber Recovery Connector appliances. |
Ensures the appliance has accurate name resolution. |
|
Time Synchronization
Time synchronization provided by the Network Time Protocol (NTP) ensures that all components within the SDDC are synchronized to the same time source. This section of the design consists of characteristics and decisions that support the time configuration for the VMware Live Cyber Recovery Connector appliances.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
CBR-CDP-NET-005 |
Use VMware Tools™ to synchronize time from ESXi hosts for the VMware Live Cyber Recovery Connector appliances. |
Prevents time mismatches between the the VMware Live Cyber Recovery Connector appliance and its dependencies. |
|