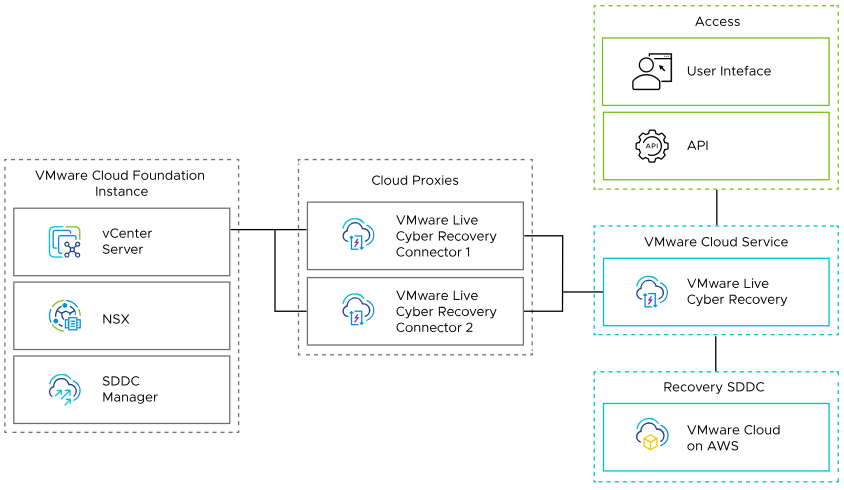
The logical design provides a high-level overview of the Cloud-Based Ransomware Recovery for VMware Cloud Foundation validated solution.
The Cloud-Based Ransomware for VMware Cloud Foundation validated solution utilizes the VMware Live Cyber Recovery service from VMware to protect business workloads from a ransomware attack and to recover them to a VMware Cloud on AWS instance.
To provide failover capabilities, this validated solution defines the following logical configuration of the SDDC management components.
| Management Component |
Logical Configuration for Ransomware Recovery |
|---|---|
| VMware Cloud Foundation (Protected Site) |
|
| VMware Cloud on AWS (Recovery Site) |
|
| VMware Live Cyber Recovery |
VMware Cloud Foundation instance:
|
| VMware Cloud Service
|
| Single VMware Cloud Foundation Instance with a Single Availability Zone |
Single VMware Cloud Foundation Instance with Multiple Availability Zones |
Multiple VMware Cloud Foundation Instances |
|---|---|---|
|
|
|