vSphere with Tanzu requires multiple networks. This section discusses networking design not covered in the NSX detailed design.
You deploy all vSphere with Tanzu workloads to overlay-backed NSX segments. NSX Edge nodes in the shared edge and workload vSphere cluster are deployed to VLAN-backed portgroups.
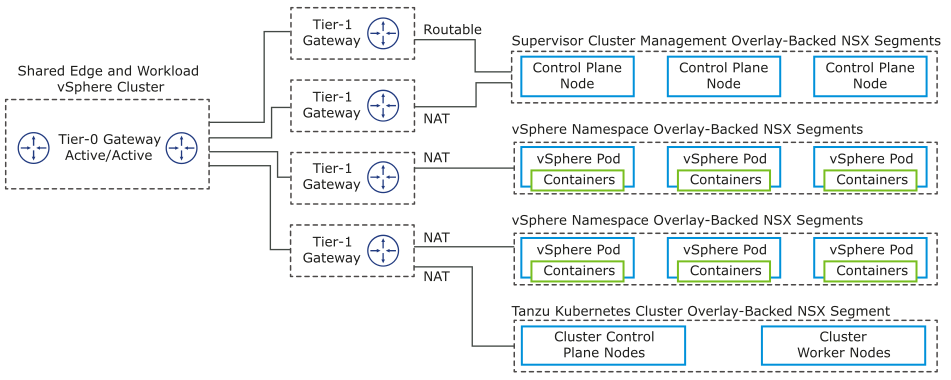
| Network |
Routable / NAT |
Usage |
|---|---|---|
| Supervisor Cluster Management Network |
Routable |
Used by the Supervisor control plane nodes. |
| Namespace Networks |
NAT |
When you create a namespace, a /28 overlay-backed NSX segment and corresponding IP pool is instantiated to service pods in that namespace. If that IP space runs out, an additional /28 overlay-backed NSX segment and IP pool are instantiated. |
| Service IP Pool Network |
NAT |
Used by Kubernetes applications that need a service IP address. |
| Ingress IP Pool Network |
Routable |
Used by NSX to create an IP pool for load balancing. |
| Egress IP Pool Network |
Routable |
Used by NSX to create an IP pool for NAT endpoint use. |
| Pod Networks |
NAT |
Used by Kubernetes pods that run in the cluster. Any Tanzu Kubernetes Clusters instantiated in the Supervisor also use this pool. |
| Tanzu Kubernetes Cluster Service Pool Network |
NAT |
When you create a Tanzu Kubernetes cluster, an NSX Tier-1 Gateway is instantiated in NSX. On that NSX Tier-1 Gateway, a /28 overlay-backed NSX segment and IP pool is also instantiated. |
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
DRI-TZU-NET-001 |
Add a /24 overlay-backed NSX segment for use by the Supervisor control plane nodes. |
Supports the Supervisor control plane nodes. |
You must create the overlay-backed NSX segment. |
DRI-TZU-NET-002 |
Use a dedicated /20 subnet for pod networking. |
A single /20 subnet is sufficient to meet the design requirement of 2000 pods. |
Private IP space behind a NAT that you can use in multiple Supervisors. |
DRI-TZU-NET-003 |
Use a dedicated /22 subnet for services. |
A single /22 subnet is sufficient to meet the design requirement of 2000 pods. |
Private IP space behind a NAT that you can use in multiple Supervisors. |
DRI-TZU-NET-004 |
Use a dedicated /24 or larger subnet on your corporate network for ingress endpoints. |
A /24 subnet is sufficient to meet the design requirement of 2000 pods in most cases. |
This subnet must be routable to the rest of the corporate network. A /24 subnet will suffice for most use cases, but you should evaluate your ingress needs prior to deployment |
DRI-TZU-NET-005 |
Use a dedicated /24 or larger subnet on your corporate network for egress endpoints. |
A /24 subnet is sufficient to meet the design requirement of 2000 pods in most cases. |
This subnet must be routable to the rest of the corporate network. A /24 subnet will suffice for most use cases, but you should evaluate your egress needs prior to deployment |