The logical design provides a high-level overview of the Identity and Access Management for VMware Cloud Foundation solution design.
vCenter Server
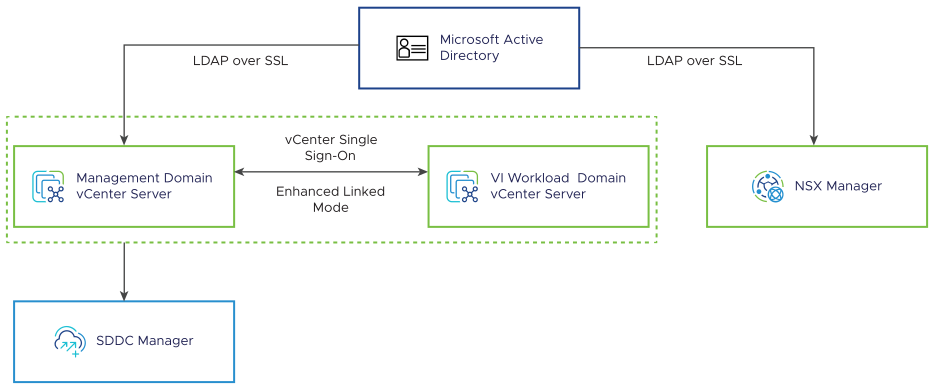
By default, the vCenter Single Sign-On built-in identity provider uses an embedded vsphere.local domain and supports local accounts. The vCenter Server instances in a VMware Cloud Foundation system are joined to the built-in identity provider and are required to participate in an enhanced linked-mode configuration. Additional VMware Cloud Foundation instances may be joined to the same vCenter Single Sign-On identity provider during bring-up or brought online with a dedicated identity provider.
vSphere configuration limits apply to linked vCenter Server instances:
-
The number of linked vCenter Servers
-
The number of hosts in linked vCenter Servers
-
The number of powered-on virtual machines in linked vCenter Servers
-
The number of registered virtual machines in linked vCenter Servers
See VMware Configuration Maximums.
The vCenter Single Sign-On built-in identity provider can be configured to use Microsoft Active Directory as its identity source using LDAP over SSL (LDAPS). The configuration is applicable to all vCenter Server instances configured in enhanced linked mode. Active Directory security groups and/or users can be assigned to default or custom roles in vSphere with the scope of provisioned and managed permissions.
ESXi
This solution does not require ESXi hosts in a VMware Cloud Foundation system to join Active Directory. SDDC Manager manages the commissioning, configuration, and life cycle of the ESXi hosts.
If supplemental storage uses NFS version 4.1 with Kerberos authentication, you must join each ESXi host to an Active Directory domain. To ensure the default security group is not used, the default esxAdminsGroup group on each ESXi host can be configured to use a custom Active Directory security group.
NSX
To provide identity management services to NSX, NSX Manager instances in a VMware Cloud Foundation system are configured to use Microsoft Active Directory as its identity source using LDAP over SSL (LDAPS). Active Directory security groups and/or users can be assigned to default or custom roles in NSX.
SDDC Manager
SDDC Manager inherits the identity provider configuration from all vCenter Server instances in enhanced linked-mode. Active Directory security groups and/or users can be assigned to default roles in SDDC Manager.