You design authentication access, controls, certificate management, and firewall for vSphere with Tanzu according to industry standards and the requirements of your organization.
vSphere with Tanzu Authentication and Access Control
You integrate vSphere with Tanzu with vCenter Single Sign-On for authentication. You can use the configured identity sources for vCenter Single Sign-On, such as Active Directory, in the Supervisor. You can assign permissions to users on a given Supervisor object, such as a namespace.
You must configure vCenter Server to be able to use Active Directory as an identity source. The in-depth design and configuration guidance for Active Directory over LDAP as an identity provider for vCenter Server is part of the Identity and Access Management for VMware Cloud Foundation validated solution. It is not mandatory to implement the entire solution, but you must complete the minimum applicable design and implementation sections for vCenter Server.
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
AIR-TZU-SEC-001 |
Create a security group in Active Directory for DevOps administrators. Add users who need edit permissions within a namespace to the group and grant Can Edit permissions to the namespace for that group. If you require different permissions per namespace, create additional groups. |
Necessary for auditable role-based access control within the Supervisor and Tanzu Kubernetes Grid clusters. |
You must define and manage security groups, group membership, and security controls in Active Directory. |
AIR-TZU-SEC-002 |
Create a security group in Active Directory for DevOps administrators. Add users who need read-only permissions in a namespace to the group, and grant Can View permissions to the namespace for that group. If you require different permissions per namespace, create additional groups. |
Necessary for auditable role-based access control within the Supervisor and Tanzu Kubernetes Grid clusters. |
You must define and manage security groups, group membership, and security controls in Active Directory. |
Certificate Management
By default, vSphere with Tanzu uses a self-signed Secure Sockets Layer (SSL) certificate. This certificate is not trusted by end-user devices or Web browsers.
As a best practice, replace self-signed certificates with certificates that are signed by a third-party or enterprise Certificate Authority (CA).
Decision ID |
Design Decision |
Design Justification |
Design Implication |
|---|---|---|---|
AIR-TZU-SEC-003 |
Replace the default self-signed certificate for the Supervisor management interface with a PEM-encoded, CA-signed certificate. |
Ensures that the communication between administrators and the Supervisor management interface is encrypted by using a trusted certificate. |
You must replace and manager certificates manually, outside certificate management automation of SDDC Manager. |
AIR-TZU-SEC-004 |
Use a SHA-2 or higher algorithm when signing certificates. |
The SHA-1 algorithm is considered less secure and has been deprecated. |
Not all certificate authorities support SHA-2. |
Network Segmentation with NSX
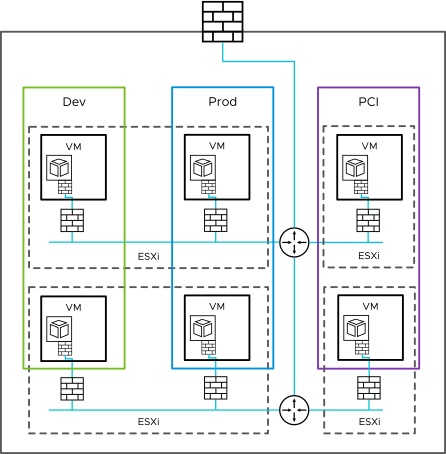
NSX has two main firewall services.
- A gateway firewall serves as a centralized stateful firewall service for north-south traffic. It is implemented per Tier-0 gateway or Tier-1 gateway. Gateway firewalls are independent from NSX distributed firewalls from policy configuration and enforcement perspective, providing a means for defining perimeter security control in addition to distributed security control.
- A distributed firewall, embedded in the hypervisor kernel, provides visibility and control for virtualized workloads and networks for east-west traffic. Because the data plane of a distributed firewall runs at the vNIC level of each virtual machine, it can enforce access controls and inspect every flow for threats without traffic hair-pinning to a gateway firewall.
Distributed Firewall for Antrea-Based Kubernetes Clusters
NSX distributed firewall works with Antrea to secure traffic within an Antrea-based Kubernetes cluster. Antrea is a Container Network Interface (CNI) plug-in for Kubernetes that supports networking for container workloads. Tanzu Kubernetes Grid clusters use Antrea as the default CNI.
You must register Antrea-based Kubernetes clusters in NSX Manager to connect the NSX Manager control plane to the Antrea Central Control Plane Adapter. You can then create distributed firewall policies (security policies) in NSX and apply them to one or more Antrea-based Kubernetes clusters. The Antrea network plug-in creates an Antrea cluster network policy (ACNP) for each security policy that is applied to the Antrea-based Kubernetes clusters. If the rules contain sources, corresponding ingress rules are created in the ACNP. If the rules contain destinations, corresponding egress rules are created in the ACNP.
While you can update and delete the Antrea cluster network policies from the kubectl command line tool, keep in mind that such changes are not displayed in NSX Manager.
For more information on how to integrate Antrea with NSX distributed firewall, see Integration of Kubernetes Clusters with Antrea CNI in the VMware NSX Administration Guide.