NSX-T is the networking and security platform used in VMware Cloud on Dell to create and manage internal SDDC networks.
NSX-T provides a full set of logical network and security services decoupled from the underlying physical infrastructure. Distributed functions such as switching, routing, and firewalling not only provide L2 extension capabilities but also enhanced distributed networking and security functions.
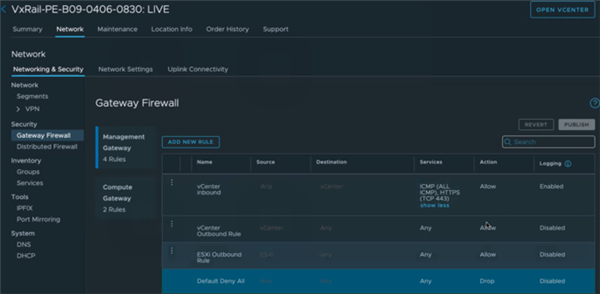
For security purpose, the logical network is separated into management network and workload network. All the management components, such as vCenter and VMware NSX® Manager™ reside on networks connected to the Management Gateway (MGW) and VMware manages these components. You are not allowed to deploy workloads on the management network through MGW. You must create NSX network segments that are automatically connected to the Compute Gateway (CGW) and deploy your workloads on these network segments.
For more information on NSX-T networking, see the VMware Cloud on AWS Networking and Security document.
Reserved Network Addresses
Certain CIDR ranges are unavailable for use in SDDC compute networks. Several are used internally by SDDC network components. Most are reserved by convention on other networks as well.
- 10.0.0.0/16
- 10.1.0.0/16
- 10.30.0.0/16
- 10.35.0.0/16
- 10.250.0.0/16
- 10.251.0.0/16
- 10.252.0.0/16
- 10.253.0.0/16
- 10.254.0.0/16
- 10.255.0.0/16
- 10.170.0.0/18
- 10.170.64.0/18
- 10.170.128.0/18
- 192.168.1.0/24