Virtual machines are the logical containers in which applications and guest operating systems run. By design, all VMware VMs are isolated from one another. This isolation enables multiple VMs to run securely while sharing hardware, and provides both their ability to access hardware and their uninterrupted performance.
Even a user with system administrator privileges on a VM's guest operating system cannot breach this layer of isolation to access another VM without privileges explicitly granted by the ESXi system administrator. As a result of VM isolation, if a guest operating system running in a VM fails, other VMs on the same host continue to run. Users can still access other VMs, and the performance of other VMs is not affected.
Each VM is isolated from other VMs running on the same hardware. Although VMs share physical resources such as CPU, memory, and I/O devices, a guest operating system on an individual VM can only detect the virtual devices that are made available to it.
Virtual Machine Isolation
The VMkernel mediates all physical resources. All physical hardware access takes place through the VMkernel and VMs cannot circumvent this level of isolation.
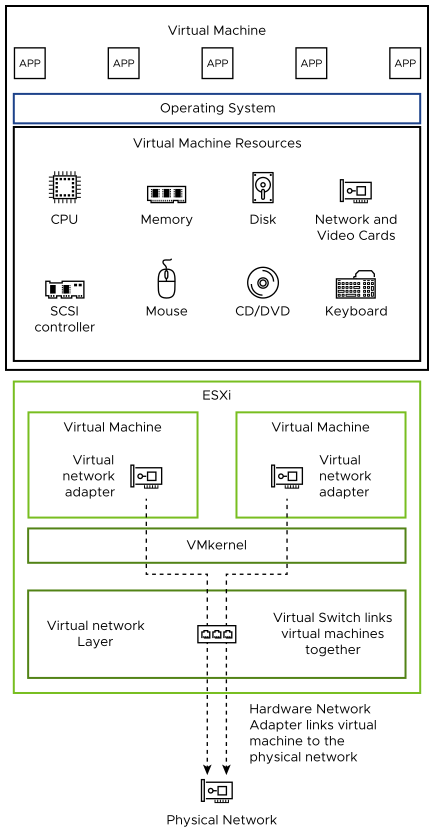
Just as a physical machine communicates with other machines in a network through a network card, a VM communicates with other VMs running on the same host through a virtual switch. Further, a VM communicates with the physical network, including VMs on other ESXi hosts, through a physical network adapter.
Virtual Networking Through Virtual Switches
Virtual networking is also affected by VM isolation.
If a VM does not share a virtual switch with any other VM, it is completely isolated from VMs within the host.
If no physical network adapter is configured for a VM, the VM is completely isolated. This includes isolation from any physical or virtual networks.
VMs are as secure as physical machines if protected from the network by firewalls and antivirus software.
VMs can be further protected by setting up resource reservations and limits on the host. For example, resource allocation allows configuration of a VM so that it always receives at least 10 percent of the host's CPU resources, but never more than 20 percent.
Resource reservations and limits protect VMs from performance degradation that might result if another VM consumed excessive shared hardware resources. For example, if one of the VMs on a host is incapacitated by a Denial-of-Service (DoS) attack, a resource limit on that machine prevents the attack from taking up so much of the hardware resources that the other VMs are also affected. Similarly, a resource reservation on each of the VMs ensures that in the event of high resource demands by the VM targeted by the DoS attack, all the other VMs have enough resources to operate.
By default, ESXi imposes a form of resource reservation by applying a distribution algorithm that divides the available host resources equally among the VMs while keeping a certain percentage of resources for use by other system components. This default behavior provides a degree of natural protection from DoS and Distributed Denial-of-Service (DDoS) attacks. Specific resource reservations and limits are set on an individual basis to customize the default behavior so that the distribution is not equal across the VM configuration.
Security and Virtual Networks
If an ESXi host is accessed through vCenter Server, it is typical to protect vCenter Server using one or more firewalls to provide basic protection for the network.
Networks configured with vCenter Server can receive communications through the vSphere Client or third-party network management clients. vCenter Server listens for data from its managed hosts and clients on designated ports. vCenter Server also assumes that its managed hosts listen for data from vCenter Server on designated ports. Firewalls between ESXi, vCenter Server, and other vSphere components must have open ports to support data transfer.
Firewalls might also be included at a variety of other access points in the network, depending on how the network is planned to be used and the level of security various devices require. Select the locations for firewalls based on the security risks that have been identified for a specific network configuration.