Adding Microsoft RADIUS integration to VMware Edge Network Intelligence allows you to see the specific RADIUS authentication messages related to network authentication. Without this integration RADIUS messages are not decoded and will only report success or failure. This integration is accomplished using the Solarwinds log forwarder for Windows and adding the crawler as a syslog logging target.
Download the free event log forwarder from Solarwindshttps://www.solarwinds.com/free-tools/event-log-forwarder-for-windows
Make sure you have the event logger activated on your Microsoft radius server.
Step 1: Install the log forwarder and then open it to begin configuration
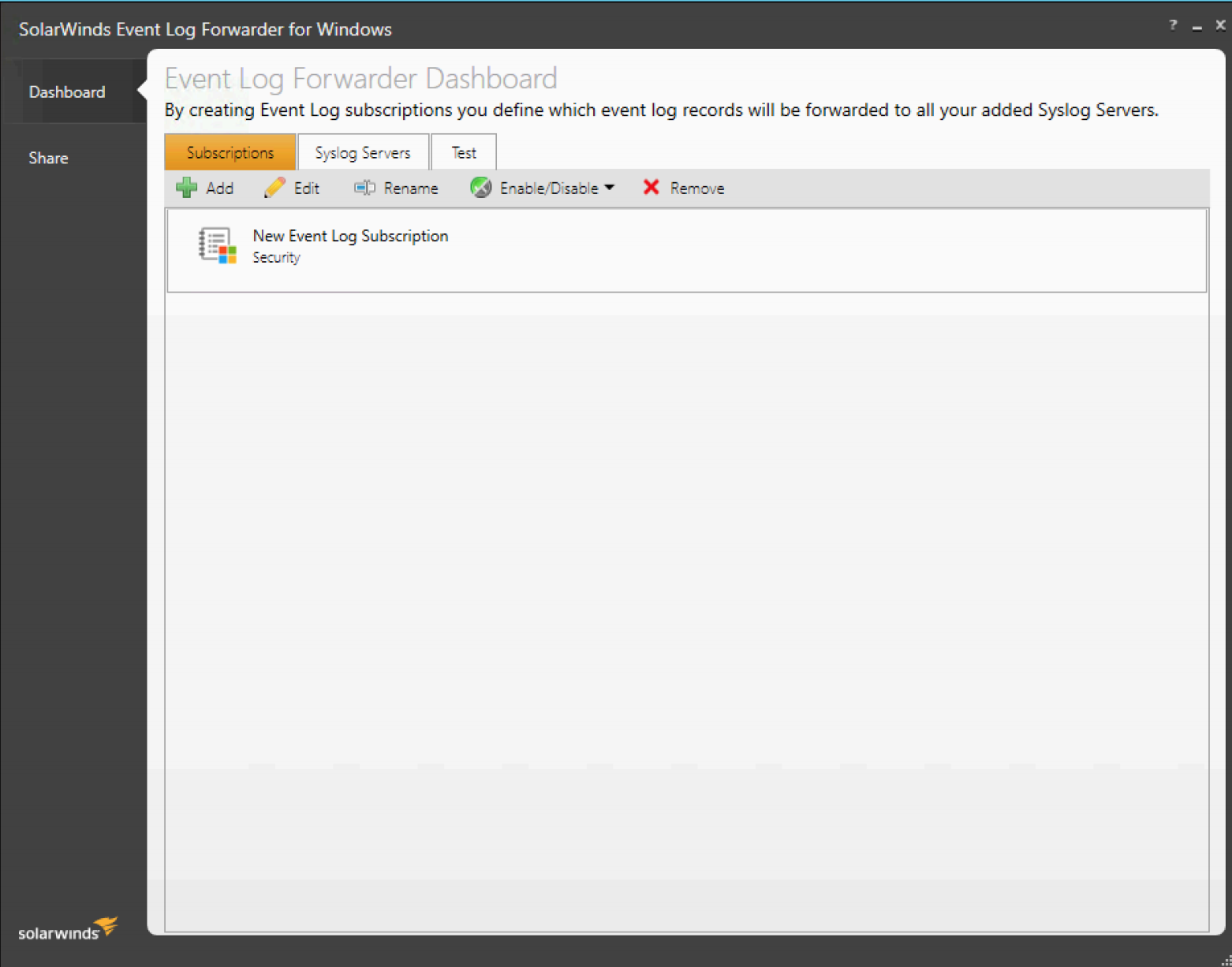
Step 2: Add a subscription to the event logs to forward to the Crawler. From the Solarwinds Dashboard > Subscriptions, add a new subscription by choosing "Add"
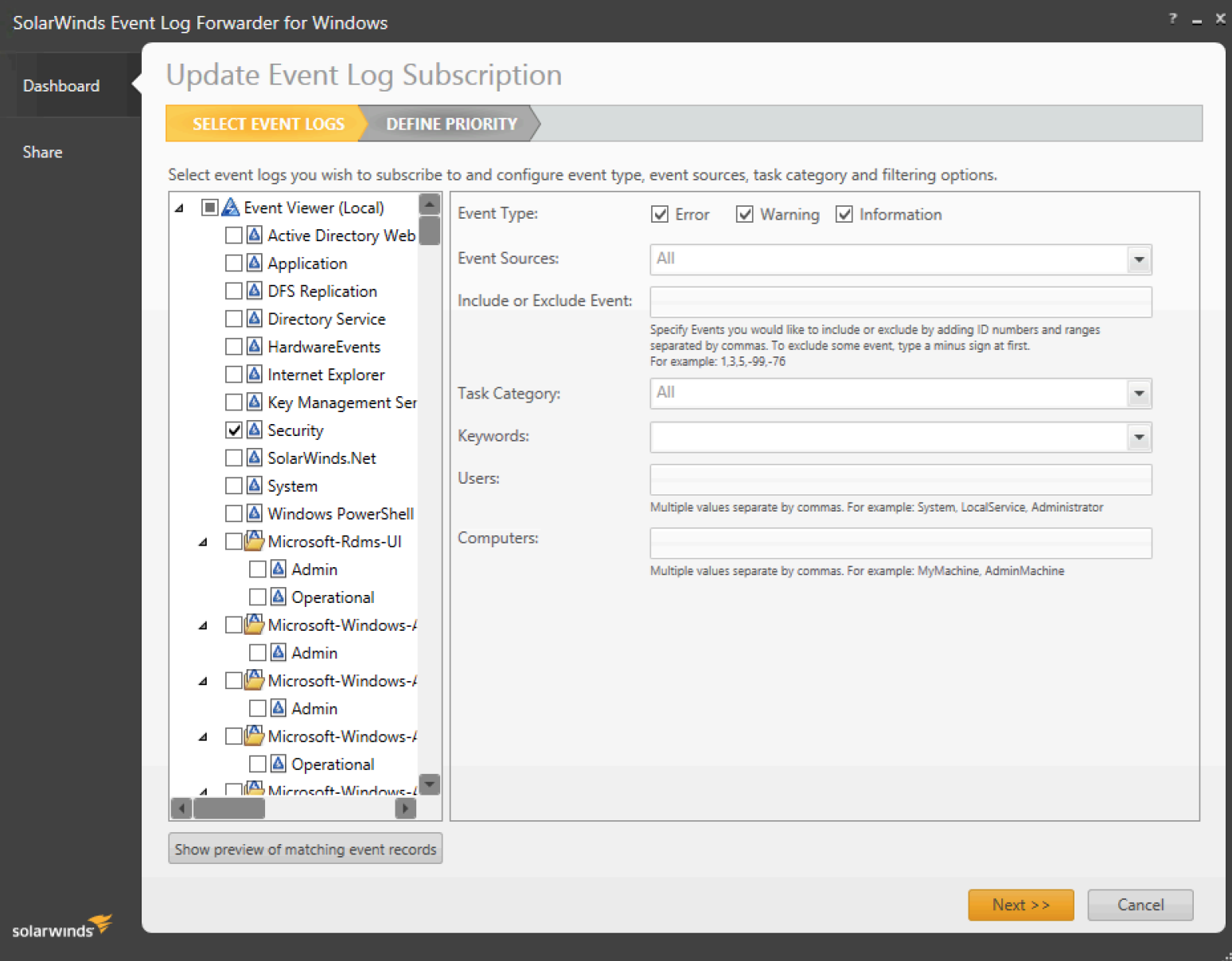
Step 2: Select the event log type "Security" to subscribe from the left column tree view control and make sure you include Error, Warning, and Information from the Event Type.
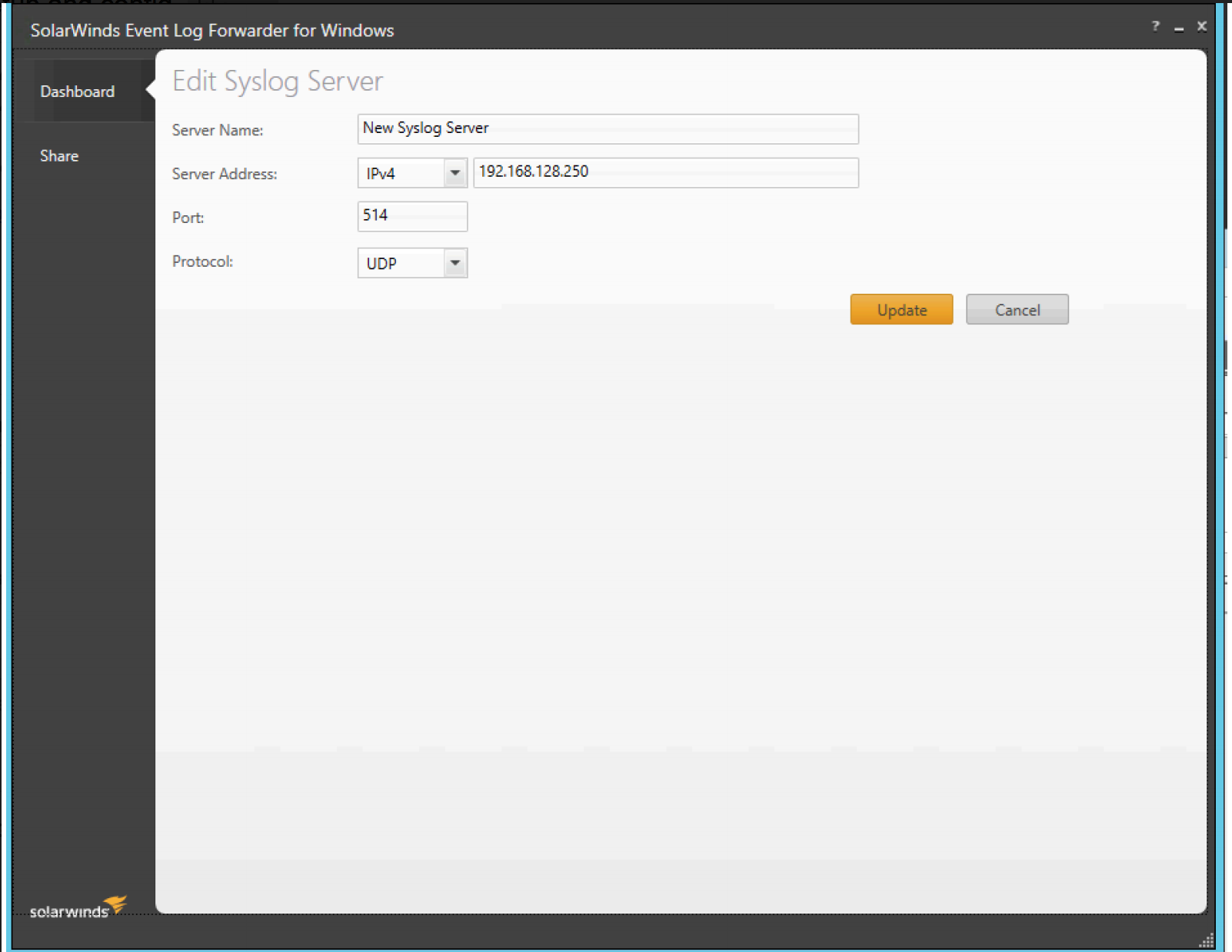
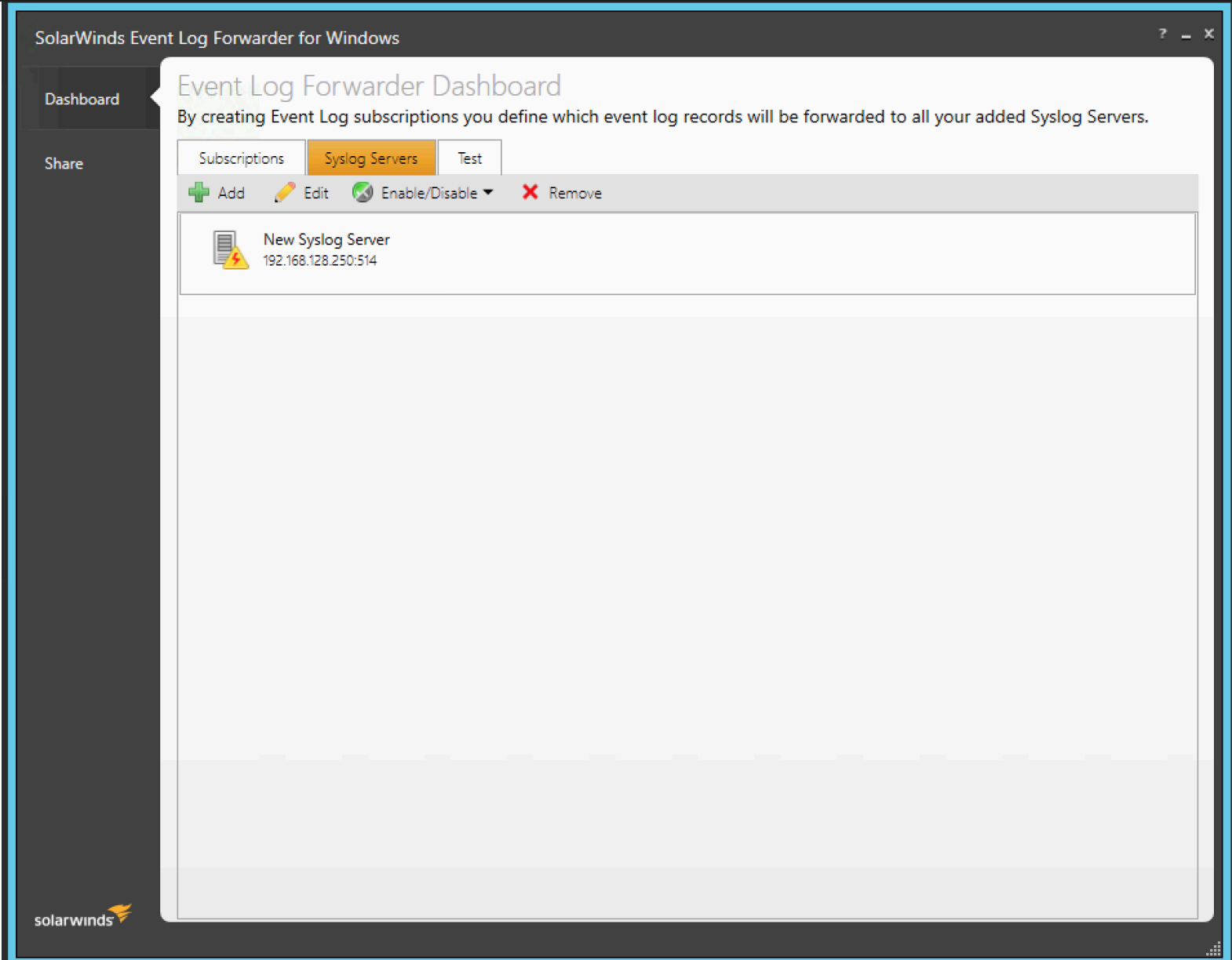
Step 3: Under SolarWinds, From the Dashboard > Syslog Servers, add a new Syslog server by choosing "Add".
Server name |
Crawler Name |
Server address |
<IP of the crawler> |
Port |
514 |
Protocol |
UDP |