Adding Cisco ISE integration to VMware Edge Network Intelligence allows you to see the specific RADIUS authentication messages related to a devices network authentication. Without this integration RADIUS messages are not decoded and can only report the success or failure of an authentication request. This integration is accomplished using the syslog logging target in the ISE server.
Follow these steps to add the VMware Edge Network Intelligence crawler as a syslog collector in ISE.
Step 1: Choose Administration > System > Logging > Remote Logging Targets.

Step 2 : Click Add and configure the following fields. Then click Save.
IP Address |
IP Address of the crawler that will receive the syslogs - can be any crawler |
Port |
514 |
Facility Code |
Local6 |
Maximum Length |
8192 (Must be over 8000) |
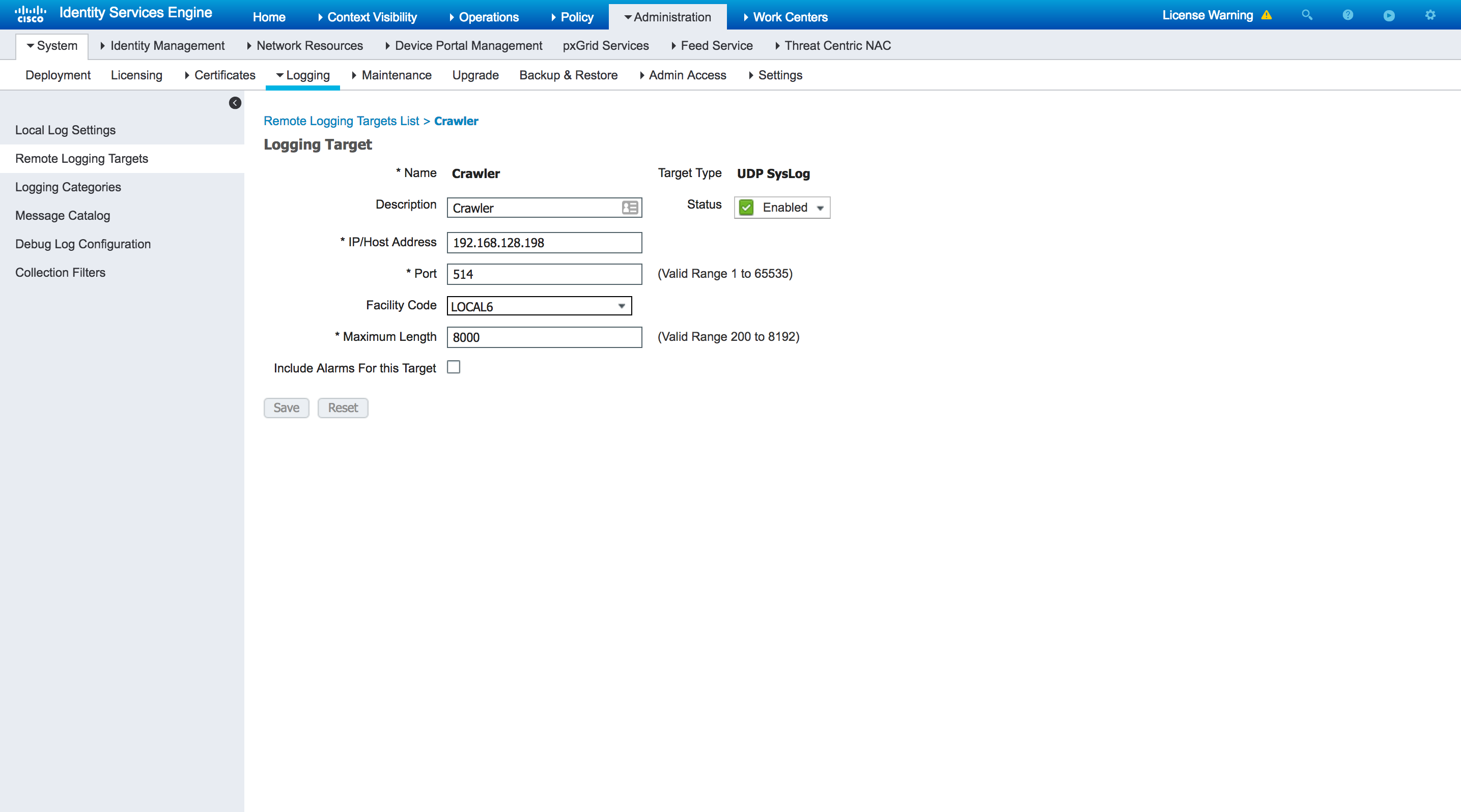
Step 3 : Verify the creation of the new target under the Remote Logging Targets page
Step 4 : After you have created the syslog storage location, in the Logging Target page, you need to map the storage location to the required logging categories, to receive the logs.
Step 5: Select Administration > System > Logging > Logging Categories.
Under Failed Attempts, click Edit and select the Crawler that you just created.
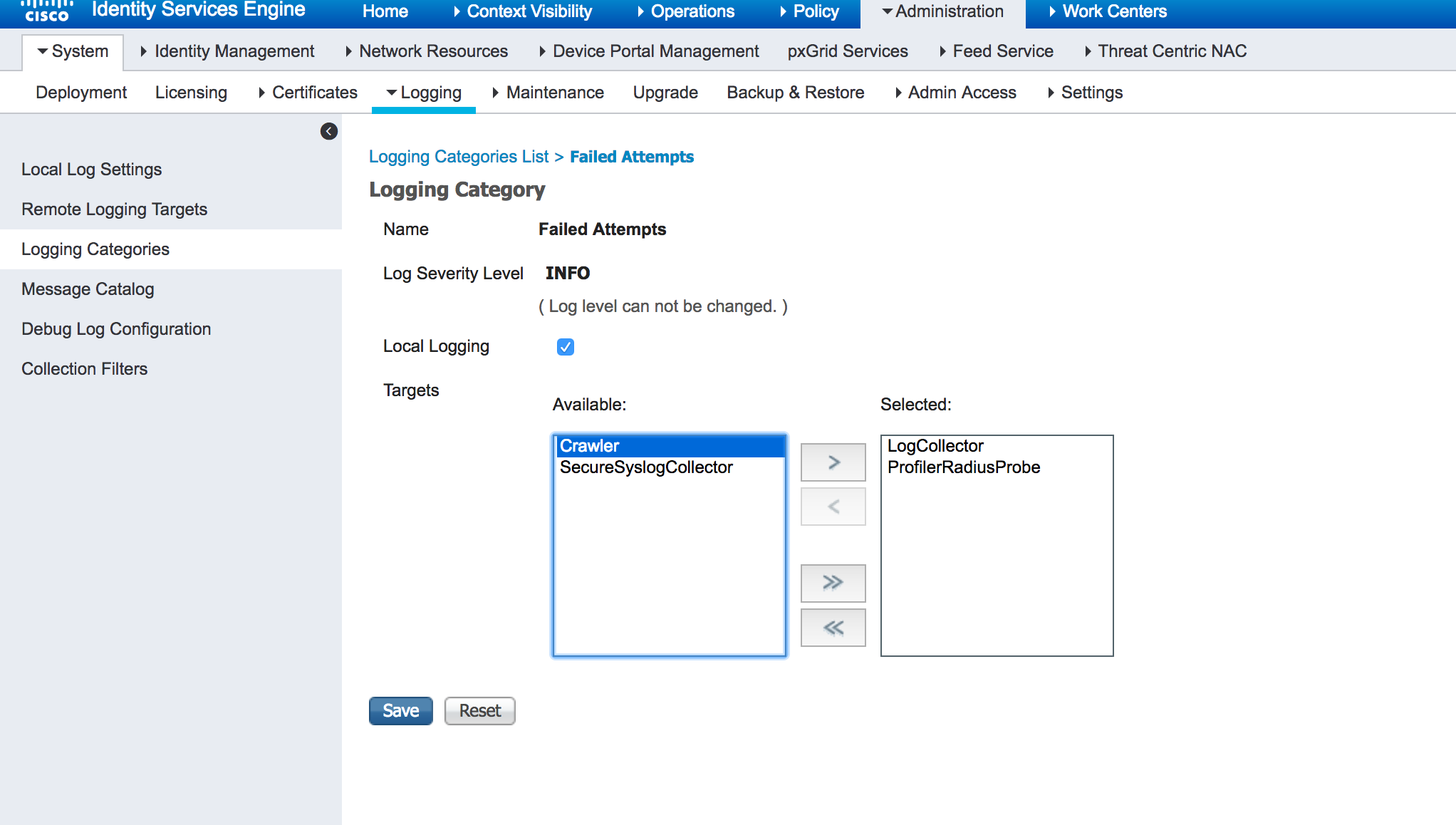
Step 6: Add the crawler to the passed authentications logging category.
Under Logging categories, verify whether the crawler is under the Failed attempts or Pass authentication targets.
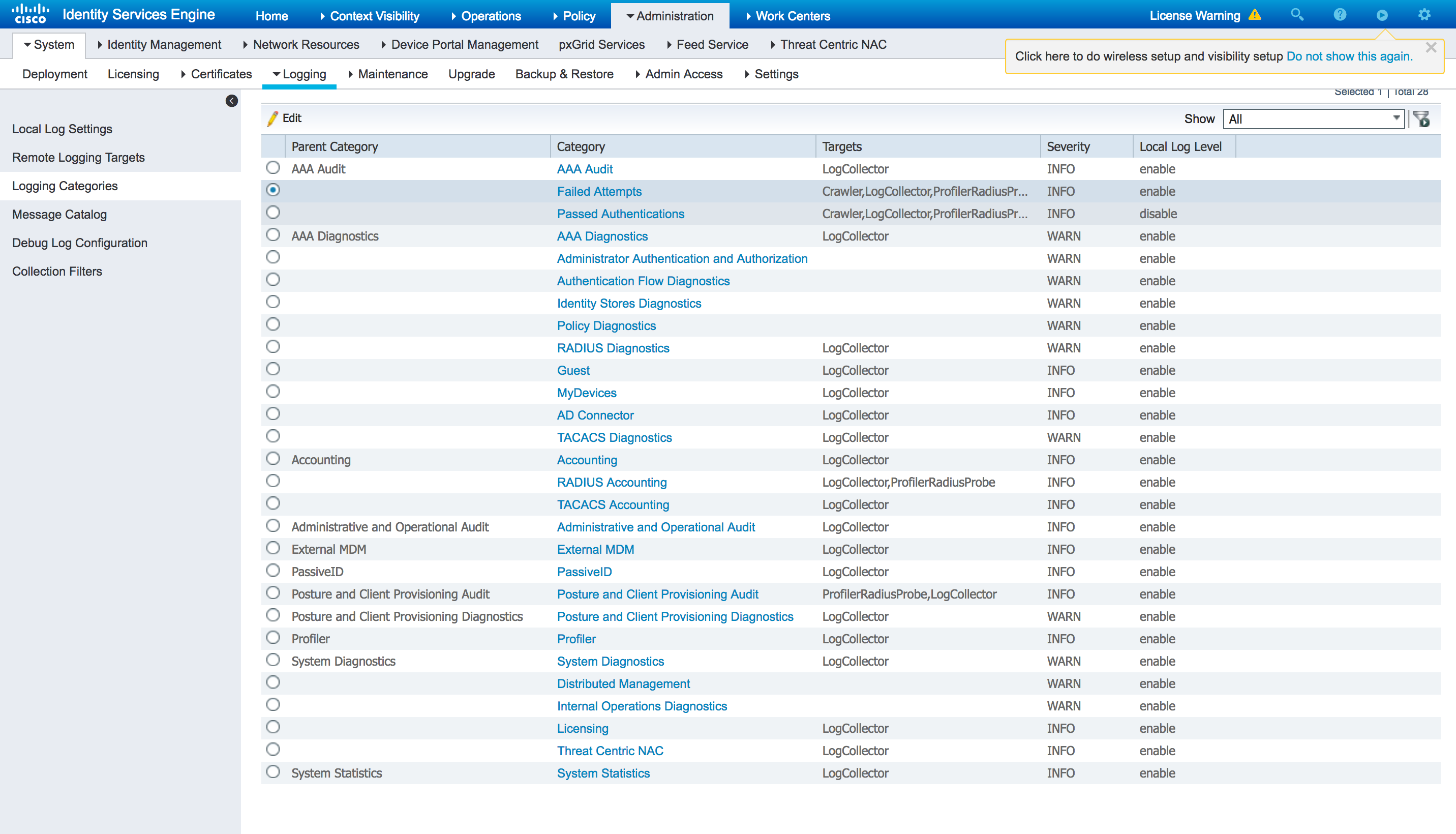
Anytime the maximum length is changed you must remove and re-add the crawler target.