This topic describes security when using VMware Tanzu GemFire for Tanzu Application Service.
The security measures implemented for a VMware Tanzu Application Service for VMs (Tanzu Application Service for VMs) foundation and for GemFire for Tanzu Application Service service instances within that foundation attempt to reduce harm from agents with foundation access. For general information about security in Tanzu Application Service for VMs, see Tanzu Application Service for VMs Security in the VMware Tanzu Application Service documentation.
Transport-Layer Security (TLS) encryption prevents easy access to communication between components, and role-based authentication and authorization limits access to data.
TLS Encryption for the GemFire for Tanzu Application Service Service Instance
Without TLS encryption with and within the GemFire for Tanzu Application Service service instance, the diagram below identifies via green dotted-and-dashed lines the unencrypted, plaintext communication that a bad agent with Tanzu Application Service for VMs foundation access could listen to without TLS encryption.
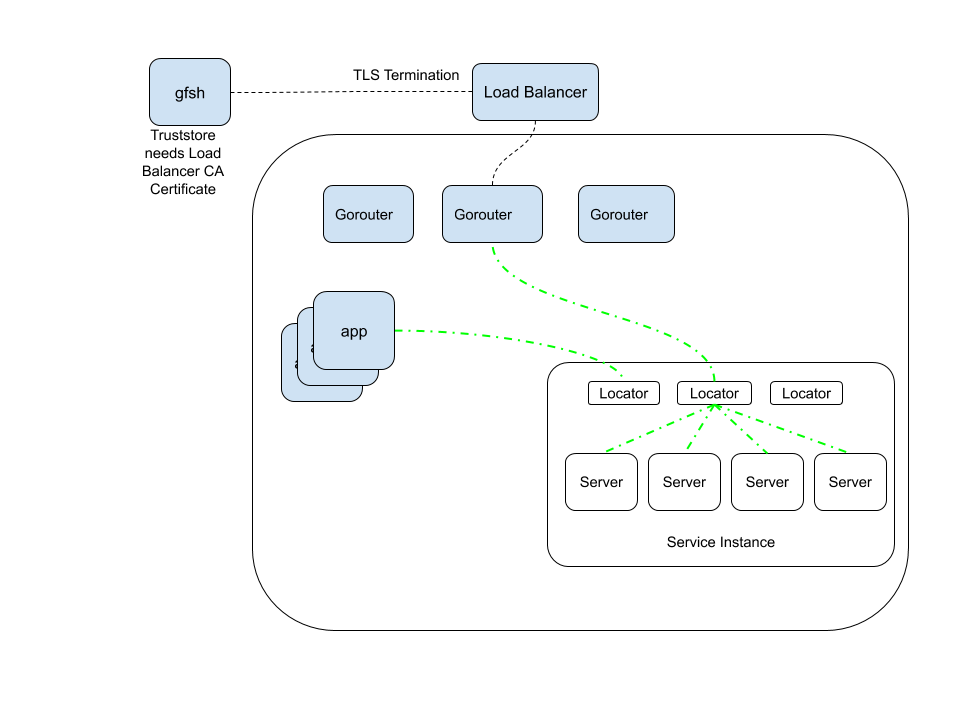
Each of these unencrypted communication paths may be TLS-encrypted. Enabling TLS encryption implements a one-way authentication of apps, verifying the identity of cluster members.
You must also secure gfsh communication. Follow directions in Connect with gfsh over HTTPS.
Networking
To allow app access to the Tanzu GemFire network, create application security groups. Allow access on the following ports:
- 1099
- 8080
- 40404
- 55221
For more information, see Restricting App Access to Internal Tanzu Application Service for VMs Components in the VMware Tanzu Application Service for VMs documentation.
GemFire for Tanzu Application Service works with the IPsec Add-on for Tanzu Application Service for VMs. For more information, see IPsec for VMware Tanzu.
Security within the Cluster
The cluster within a GemFire for Tanzu Application Service service instance implements role-based authentication and authorizes cluster operations based upon the roles.
There are two sets of roles:
-
One set has four roles for users that integrate an external authentication such as LDAP via User Account and Authentication (UAA). See Configuring UAA Roles for a description of the roles and the configuration that completes the integration.
-
The other set of roles defaults when there is no external authentication integrated during the GemFire for Tanzu Application Service tile installation. The identifiers assigned for these roles are detailed in Create Service Keys. GemFire for Tanzu Application Service service instances are created with three default user roles for interacting with clusters:
- Cluster operator: manages the Tanzu GemFire cluster and can access region data. Has the permissions
CLUSTER:MANAGE,CLUSTER:WRITE,CLUSTER:READ,DATA:MANAGE,DATA:WRITE, andDATA:READ. - Developer: can access region data. Has the permissions
CLUSTER:READ,DATA:WRITE, andDATA:READ. - Gateway sender: propagates region data to another GemFire for Tanzu Application Service service instance. Has the permission
DATA:WRITE.
- Cluster operator: manages the Tanzu GemFire cluster and can access region data. Has the permissions
Which set is used for a GemFire for Tanzu Application Service service instance depends on the options chosen during GemFire for Tanzu Application Service tile installation.
All gfsh and JMX clients must authenticate as one of these user roles to access the cluster. To authorize operations, each user role is given predefined permissions for cluster operations. To accomplish a cluster operation, the user authenticates using one of the roles. Prior to initiating the requested operation, there is a verification that the authenticated user role has permission to do the operation. For more information about these permissions, see Implementing Authorization in the VMware GemFire documentation.