VMware Greenplum on vSphere supports two encryption options: Virtual Machine (VM) encryption and vSAN encryption. This topic compares the two methods and provides the prerequisites and instructions to set up an end-to-end encrypted Greenplum cluster.
VMware recommends enabling AES-NI in the host BIOS to improve encryption performance. Enabling encryption has 2% CPU overhead and 0.5% memory overhead, and it causes no impact on IOPS and throughput.
Virtual Machine Encryption versus vSAN Encryption
vSAN datastore encryption and VM encryption vary in several key areas. You can find more details in the VMware Knowledge Base.
A key consideration is data-in transit encryption across hosts in your vSAN cluster, and data-at-rest encryption in your vSAN datastore. Data-in-transit encryption protects data and metadata as they move around the vSAN cluster, while Data-at-rest encryption protects data on storage devices, in case a device is removed from the cluster. You can read more about encryption types here.
The following table shows a quick feature comparison:
| Feature/Function | vSAN Encryption | VM Encryption |
|---|---|---|
| Uses an external key-management server (KMS) | √ | √ |
| Per-VM Encryption | X | √ |
| Whole-datastore encryption | √ | X |
| Data-at-Rest encryption | √ | √ |
| End-to-end encryption | X | √ |
| VMs encrypted by | Placement on datastore | Storage Policy |
| Encryption occurs | After deduplication | Before deduplication |
Based on the above:
- If your objective is end-to-end encryption, use VM encryption.
- If you prefer to have policy-controlled encryption (a mix of encrypted and unencrypted clusters), use VM encryption.
- If your objective is data-at-rest encryption, use vSAN encryption.
- If you prefer to enforce having all the virtual machines within a given vSAN datastore with data-at-rest encryption, use vSAN encryption.
Enabling Encryption on Greenplum
VMware recommends using virtual machine encryption to avoid the associated overhead when encrypting and unencrypting the vSAN. However, you may choose to use vSAN encryption instead, based on your environment requirements.
Prerequisites
Regardless of the encryption method, these prerequisites must be met:
Set up and enable the Native Key Provider (NKP) in vCenter. VMware vSphere 7.0U2 introduces the Native Key Provider (NKP) which simplifies the key creation process. Use NKP unless there is already an existing Standard Key Provider in the environment. You can read more about key providers here. For configuration details, see Configure a VMware vSphere Native Key Provider
Also ensure the NKP is backed up. For details, see Back Up a VMware vSphere Native Key Provider.
Enable Host Encryption Mode. For more details see Enable Host Encryption Mode Explicitly. To verify the results, on each ESXi host, view the Security Profile.
Option 1: Enabling Virtual Machine Encryption
Enable encryption at the virtual machine level by creating a VMware vSphere storage policy using the steps below:
Select Home → Policies and Profiles → VM Storage Policies.
Click Create.
Enter a Storage Policy name and optional description and click Next. This example uses vSAN Greenplum FTT1 RAID1 Stripe4 Thick VM Encryption as the policy name.
Under Policy structure, check the Enable host based rules box and the Enable rules for vSAN storage box.
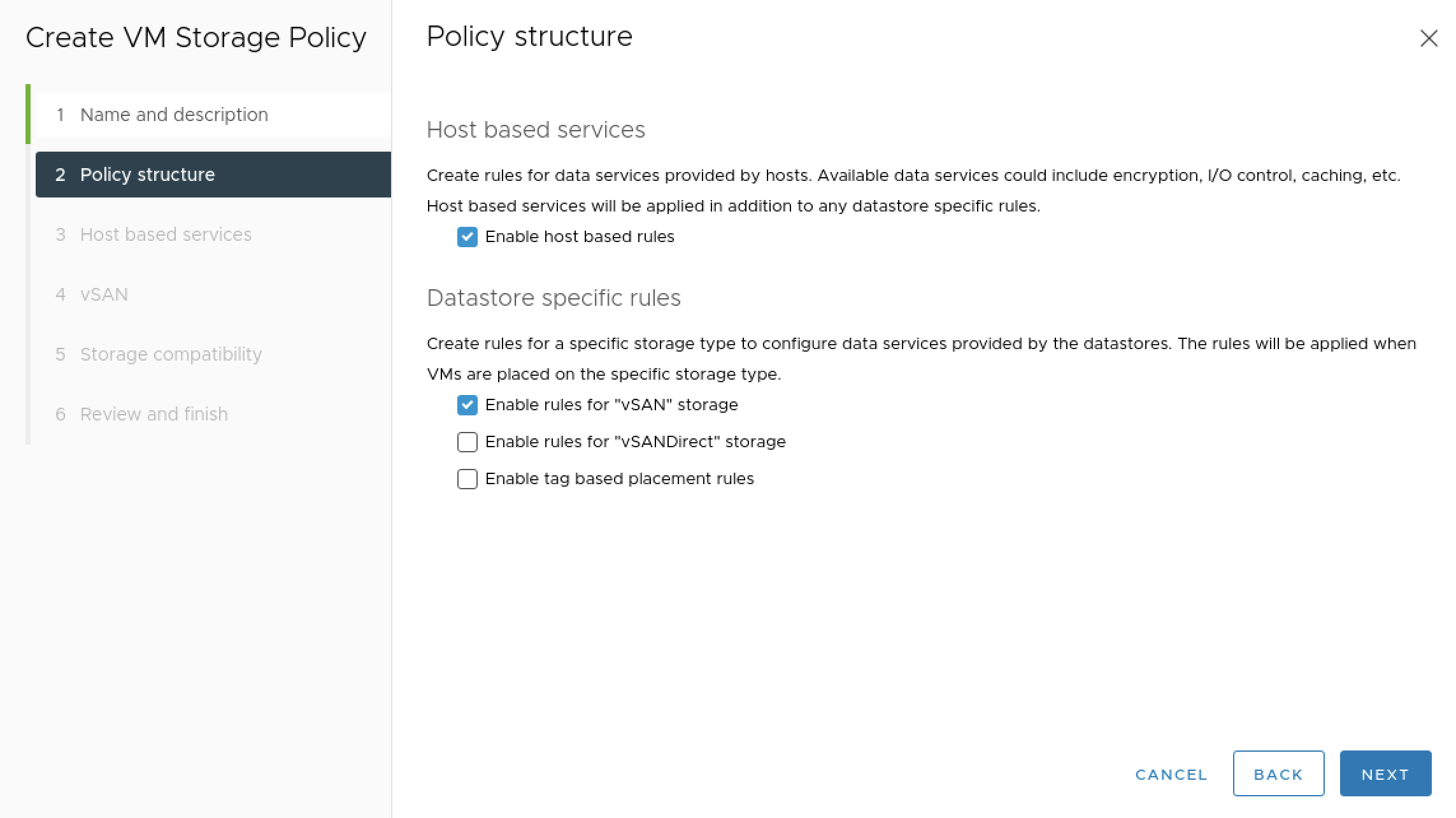
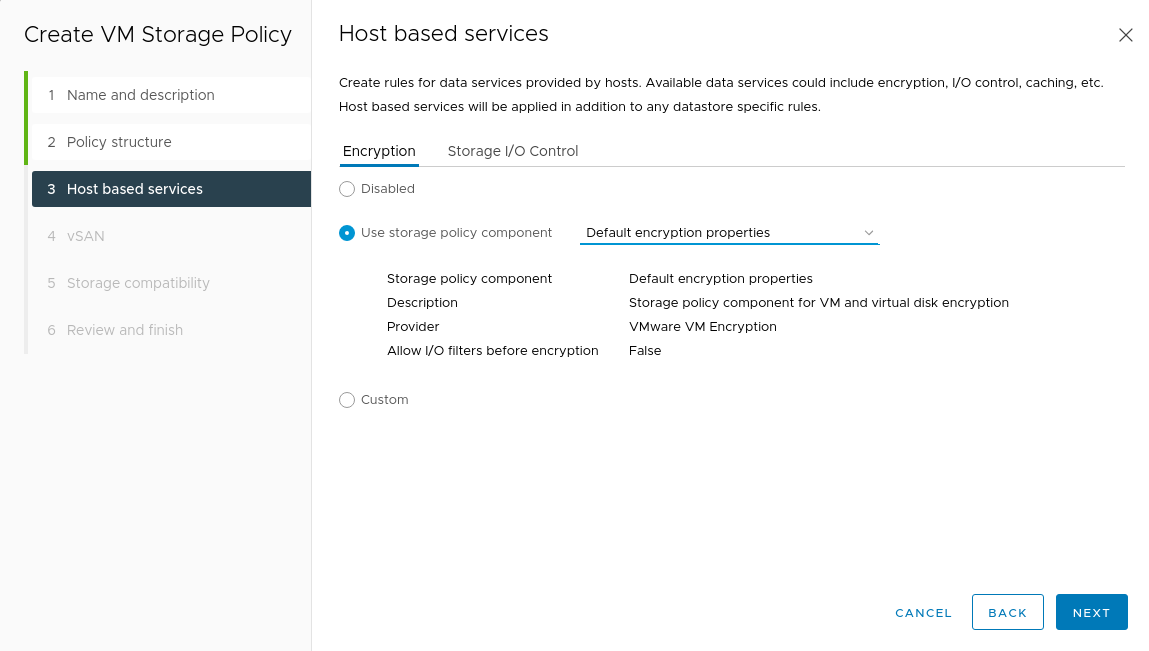
Under Host based services, select Default encryption properties to enable VM encryption.
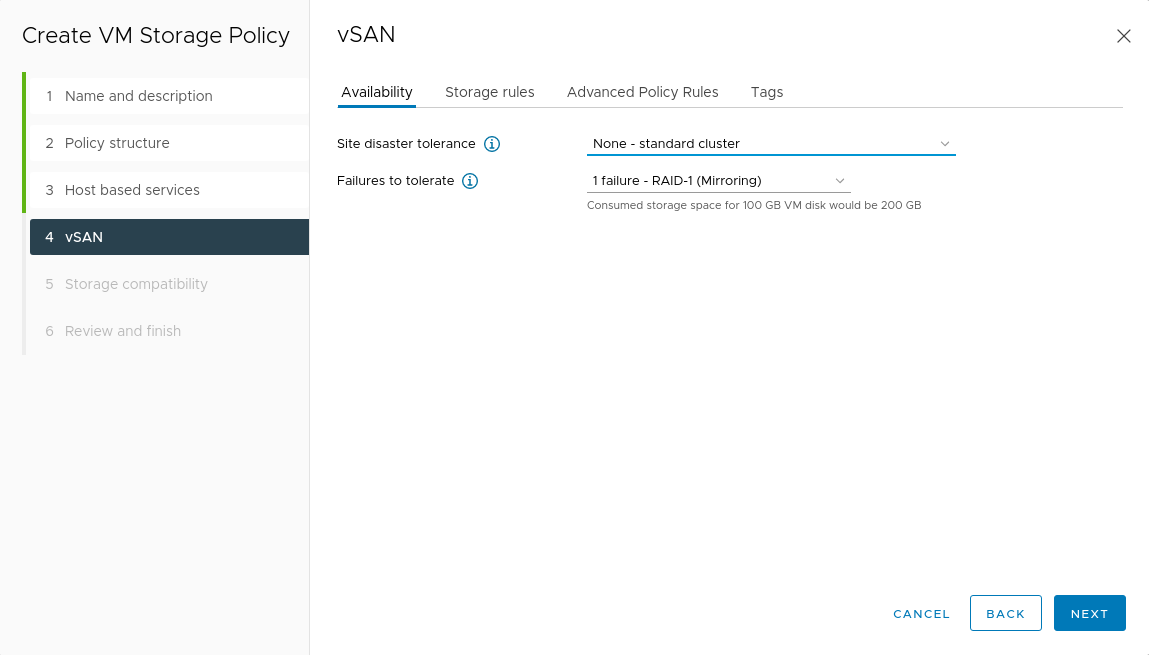
Under vSAN - Availability, select the RAID-1 mirroring vSAN policy. If you are using a different configuration, adjust this parameter accordingly.
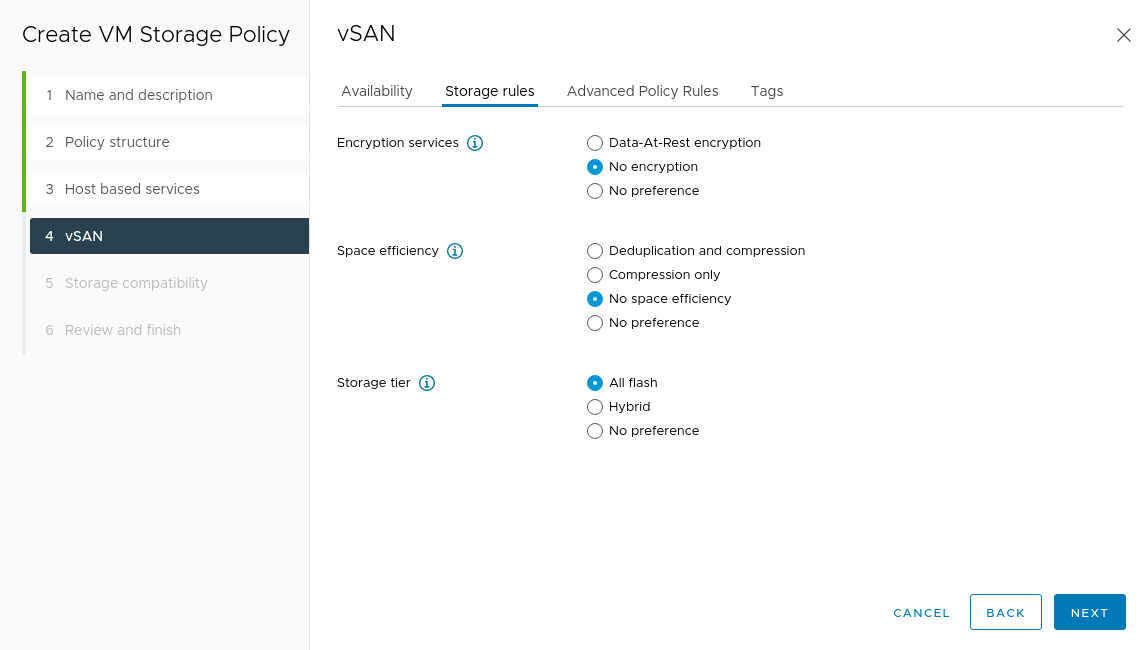
Under vSAN - Storage Rules, select No Encryption, No space efficiency, and All flash.
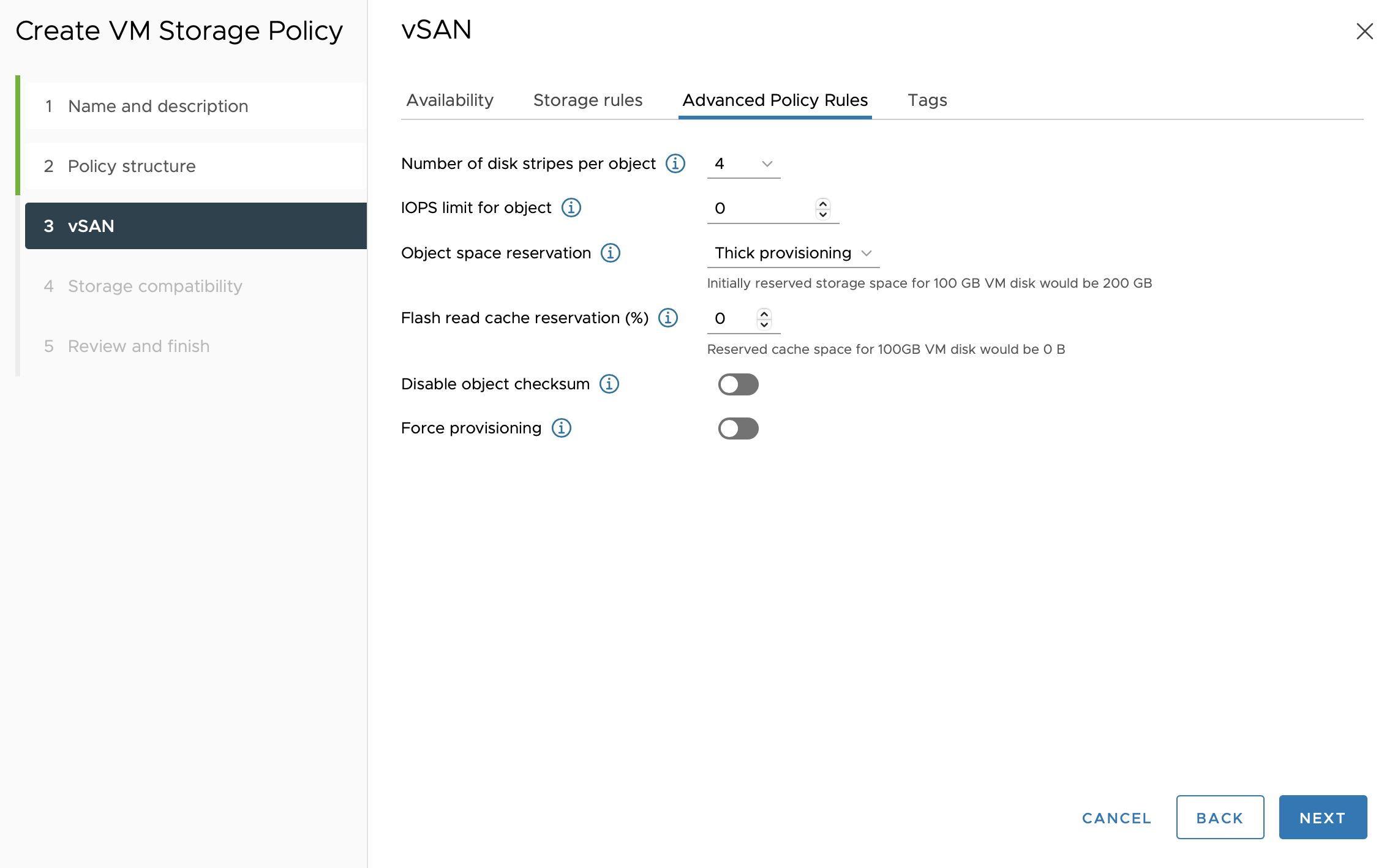
Under vSAN - Advanced Policy Rules, specify 4 for Number of disk stripes per object, and Thick provisioning.
Under Storage Compatibility, check that your vSAN storage is compatible with the storage policy.
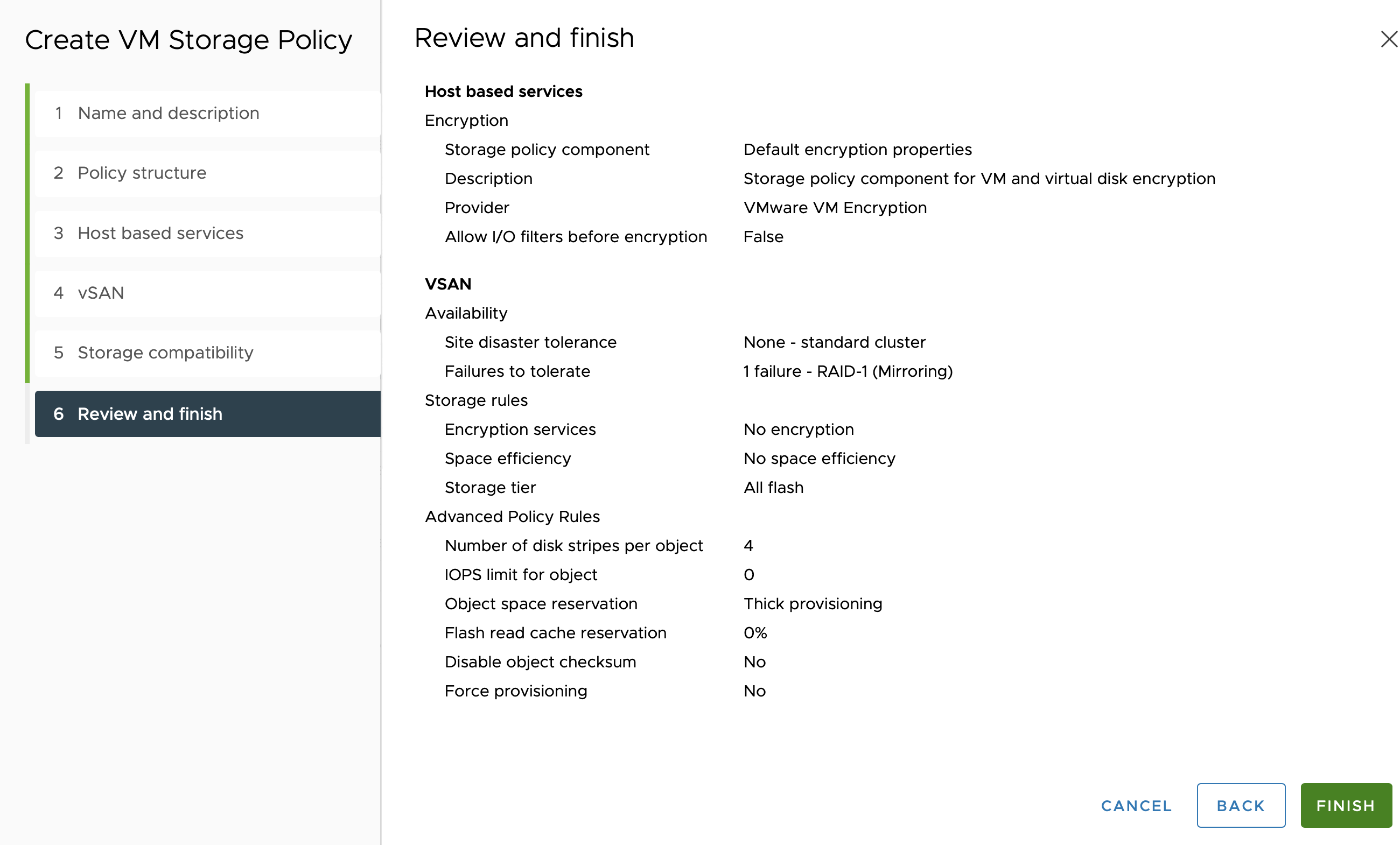
Review the Summary page. It should look similar to this:
Option 2: Enabling vSAN Encryption
In order to enable encryption at the vSAN level, you must first enable vSAN encryption and then create the VMware vSphere storage policy.
Step 1: Enabling vSAN encryption
Navigate to your cluster and click the Configure tab.
Under vSAN, select Services.
Click the vSAN Services Edit button.
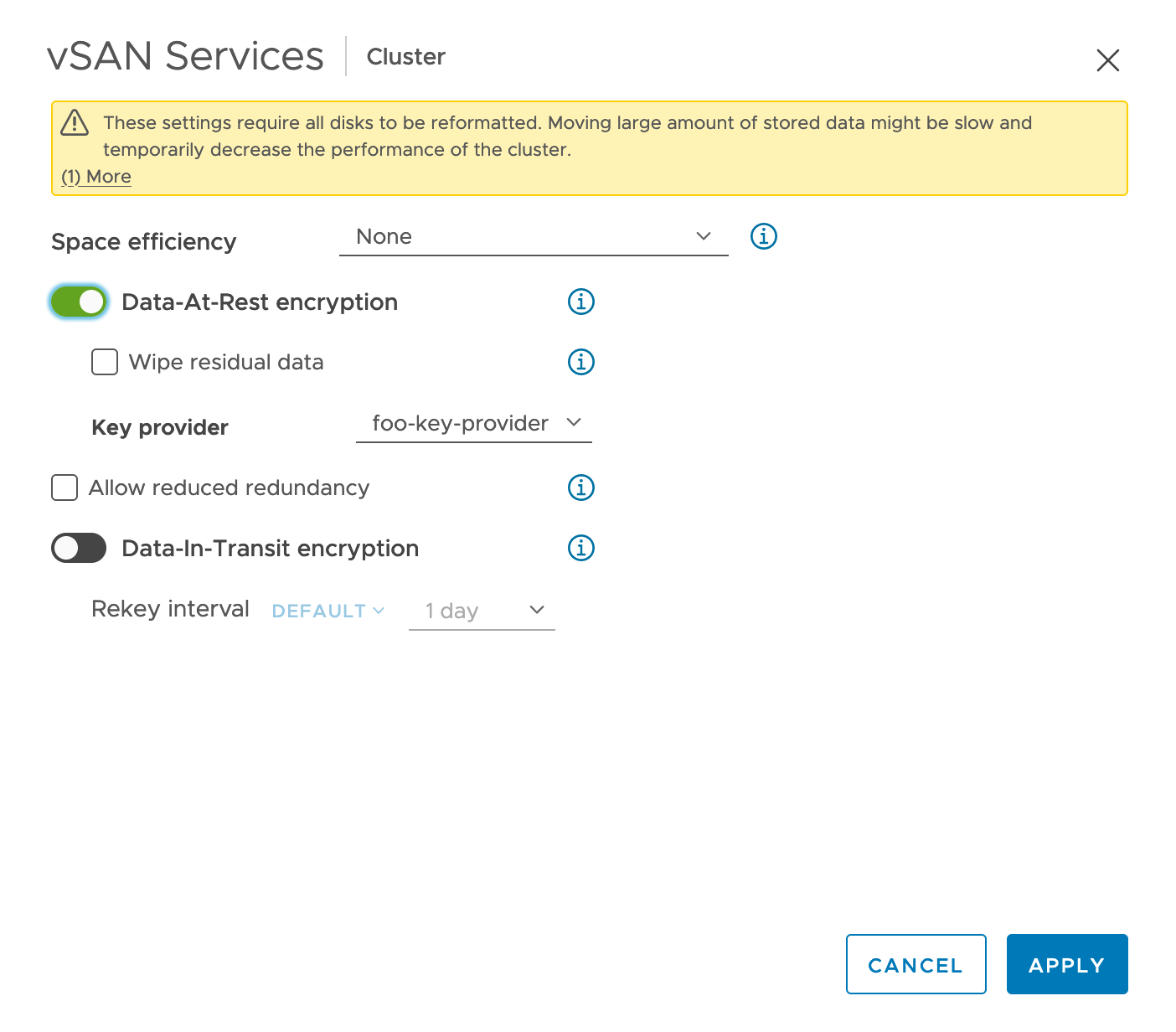
Ensure that space efficiency is set to None.
Ensure that Data-At-Rest encryption is enabled.
Note: There is a Data-in-Transit encryption option, which is for the vSAN to ensure that the data is encrypted when transferring data between hosts. However, if you are looking for that level of encryption, we recommend that you use VM encryption instead, which will provide the entire end-to-end encryption, including the encryption-in-transit and encryption-at-rest.Select a key provider and click Apply.
From this point, the vSAN will start to provision the disk groups with a new encryption format. Note that this could take several hours, depending on the size of your vSAN storage.
Step 2: Creating the VMware vSphere storage policy
Select Home, click Policies and Profiles, and click VM Storage Policies.
Click Create.
Enter a Storage Policy name and optional description and click Next. This example uses vSAN Greenplum FTT1 RAID1 Stripe4 Thick vSAN Encryption as the policy name.
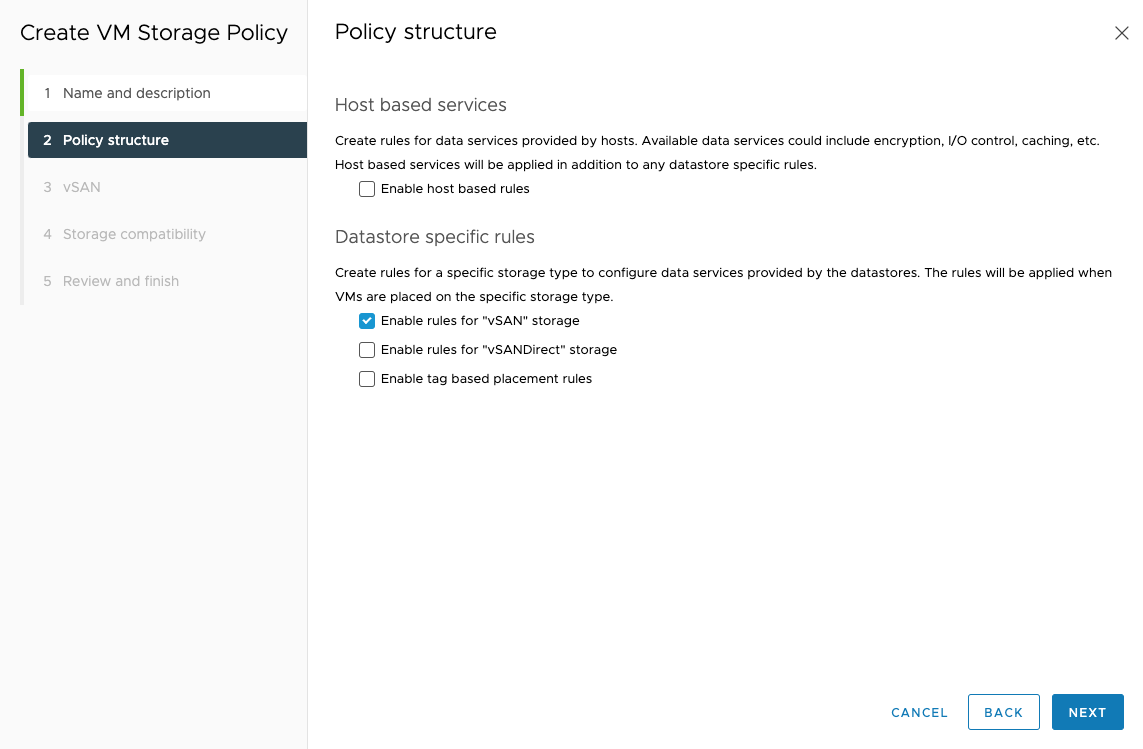
Under Policy structure, check the Enable rules for vSAN storage box.
Under vSAN - Availability, select the RAID-1 mirroring vSAN policy. If you are using a different configuration, adjust this parameter accordingly.
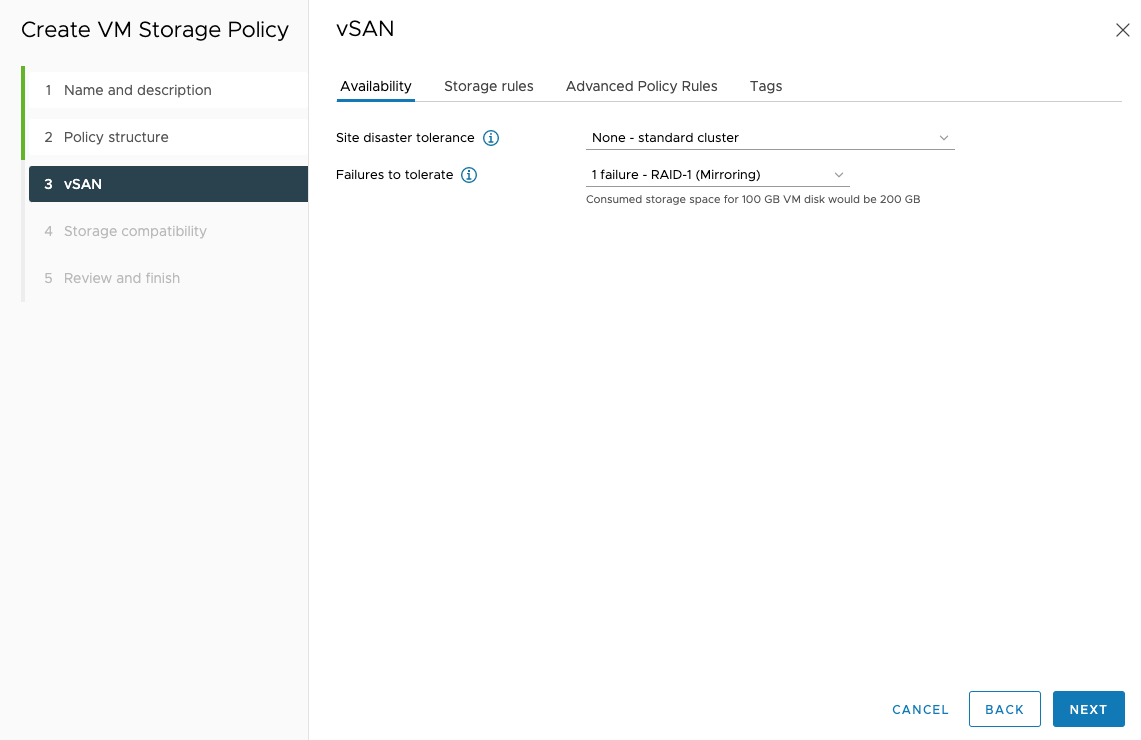
Under vSAN - Storage Rules, select Data-At-Rest Encryption, No space efficiency, and All flash.
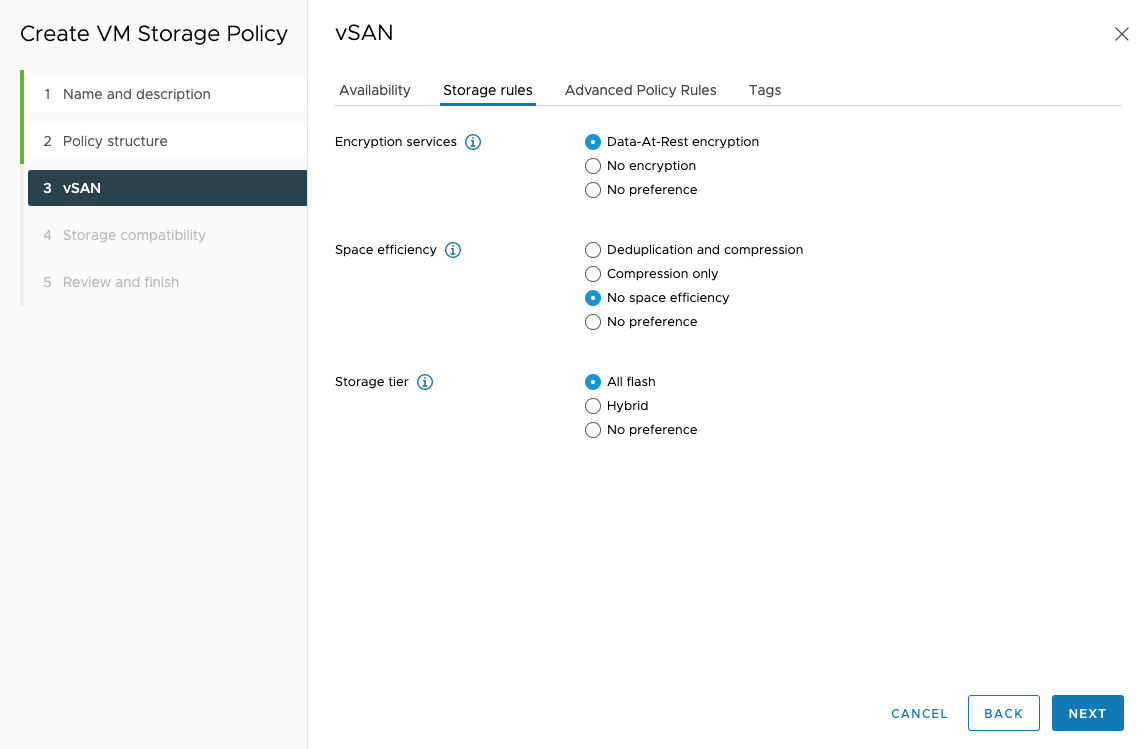
Under vSAN - Advanced Policy Rules, specify 4 for Number of disk stripes per object, and Thick provisioning.
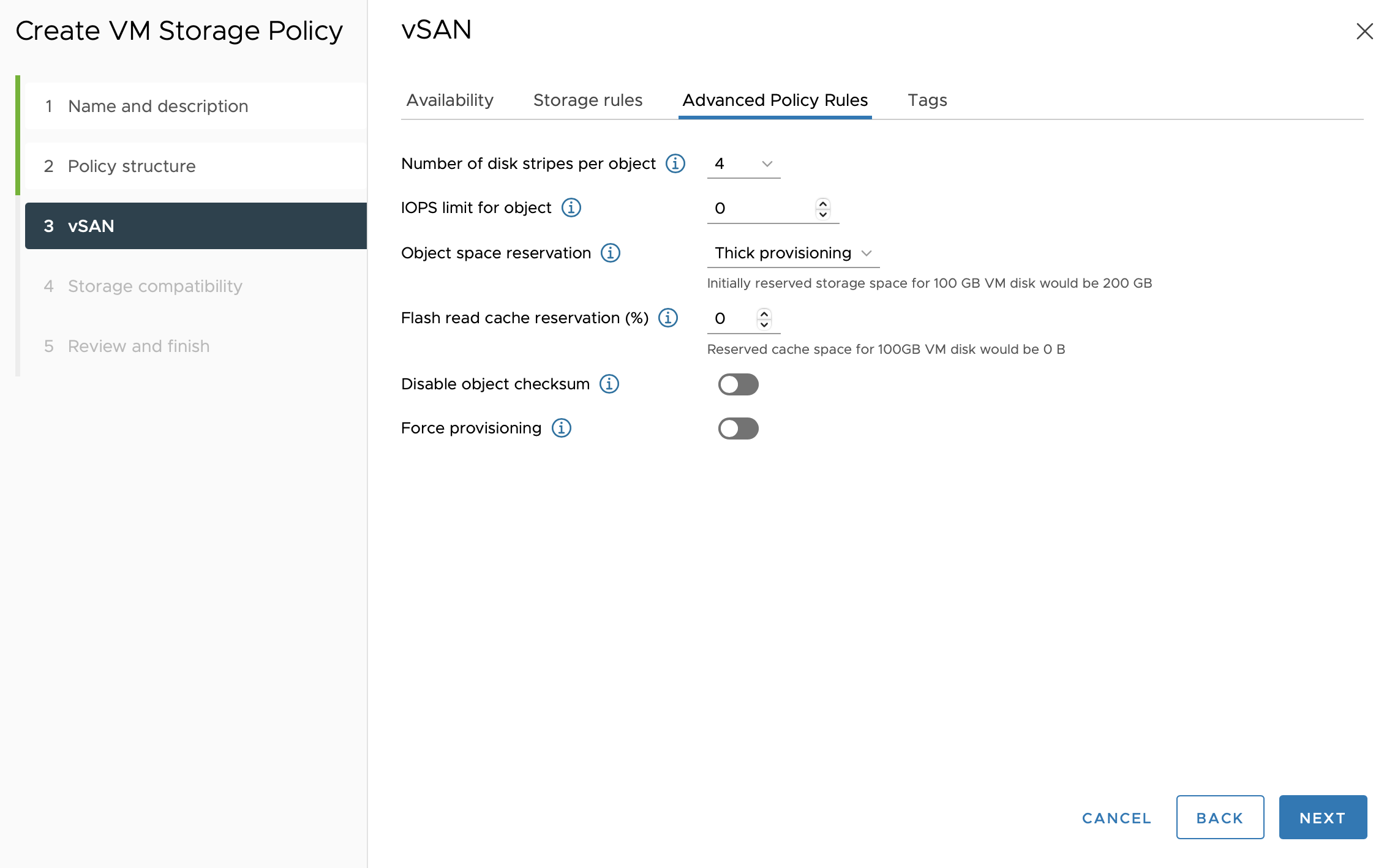
Under Storage Compatibility, check that your vSAN storage is compatible with the storage policy.
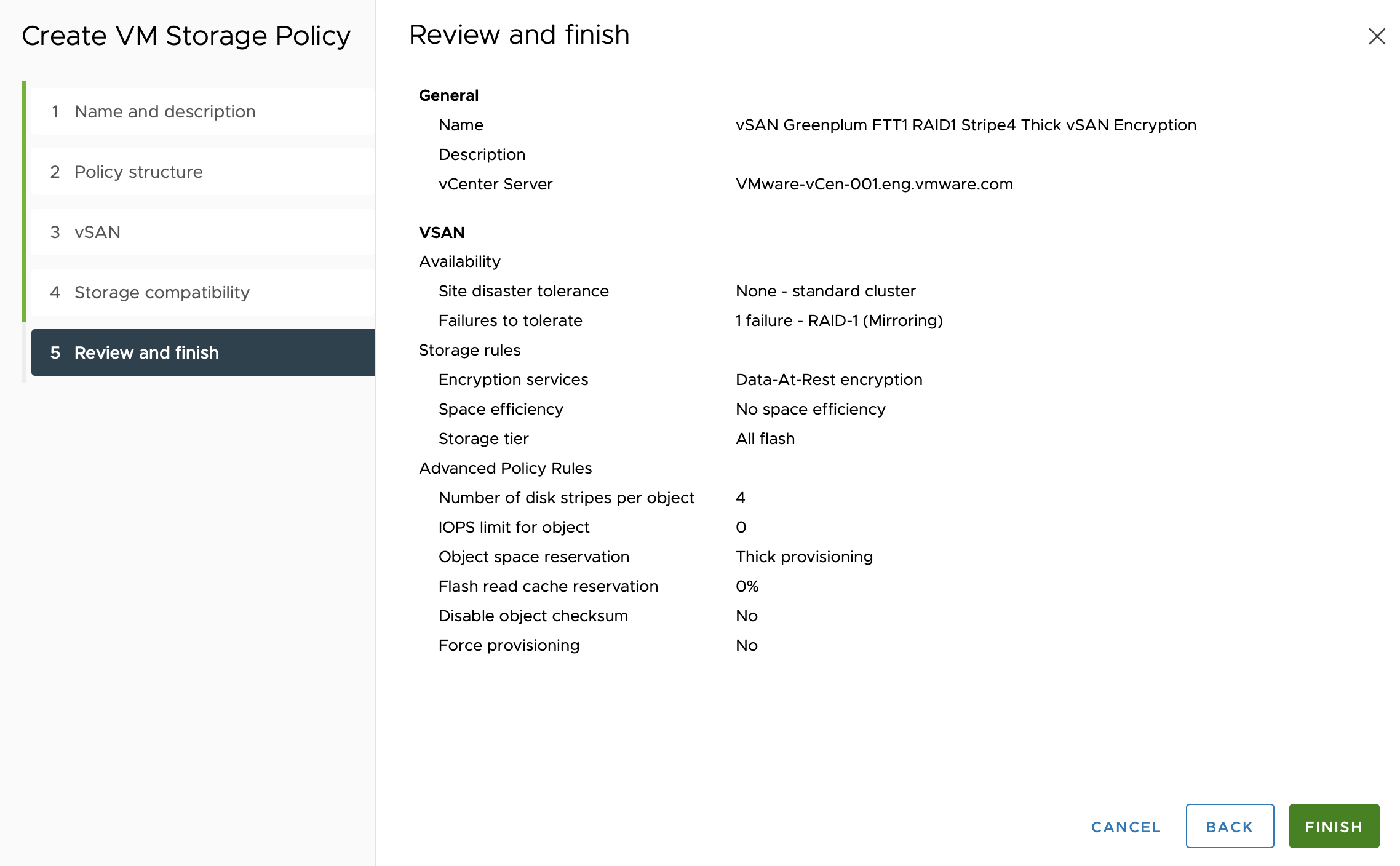
Review the Summary page. It should look similar to this:
Next Steps
You have completed setting up Dell EMC VxRail with VMware vSphere. Proceed to Validating Dell EMC VxRail Setup Performance in order to verify network connectivity and test vSAN performance with HCIBench.