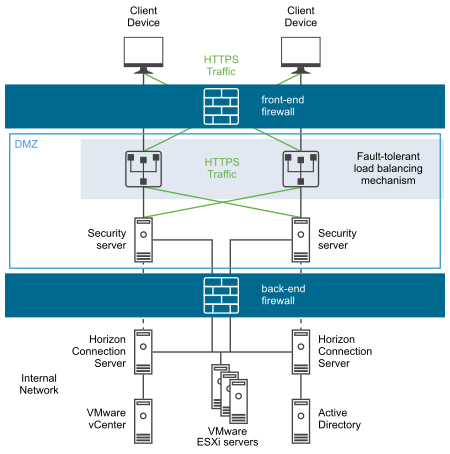
A DMZ-based security server deployment must include two firewalls.
- An external network-facing, front-end firewall is required to protect both the DMZ and the internal network. You configure this firewall to allow external network traffic to reach the DMZ.
- A back-end firewall, between the DMZ and the internal network, is required to provide a second tier of security. You configure this firewall to accept only traffic that originates from the services within the DMZ.
Firewall policy strictly controls inbound communications from DMZ services, which greatly reduces the risk of compromising your internal network. For more information about ports required to configure security servers, see the Horizon 7 Security document.
The following figure shows an example of a configuration that includes front-end and back-end firewalls.