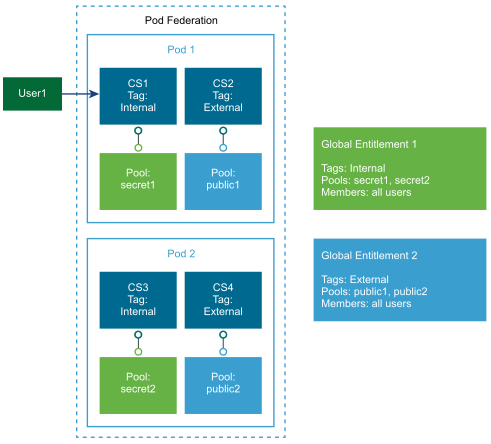
This example shows a Cloud Pod Architecture environment that includes two pods. Both pods contain two Connection Server instances. The first Connection Server instance supports internal users and the second Connection Server instance is paired with a Unified Access Gateway appliance and supports external users.
To prevent external users from accessing certain desktop and application pools, you could assign tags as follows:
- Assign the tag "Internal" to the Connection Server instance that support your internal users.
- Assign the tag "External" to the Connection Server instances that support your external users.
- Assign the "Internal" tag to the global entitlements that should be accessible only to internal users.
- Assign the "External" tag to the global entitlements that should be accessible only to external users.
External users cannot see the global entitlements that are tagged as Internal because they log in through the Connection Server instances that are tagged as External. Internal users cannot see the global entitlements that are tagged as External because they log in through the Connection Server instances that are tagged as Internal.
In the following diagram, User1 connects to the Connection Server instance called CS1. Because CS1 is tagged Internal and Global Entitlement 1 is also tagged internal, User1 can only see Global Entitlement 1. Because Global Entitlement 1 contains pools secret1 and secret2, User1 can only receive desktops or applications from the secret1 and secret2 pools.