LDAP connectivity health check can check for all the LDAP connections configured in Keystone domains.
Symptoms
Health check reports detect ldap connection issue of certain domains.
Solution
Check the Connection Manually
- Find LDAP login credentials with the following commands:
#viocli get keystone --spec
- Collect the following LDAP related values.
spec: conf: ks_domains: ${reporetd_domain} ldap: url: ${ldap_url} user: ${ldap_user} password: ${ldap_encrypted_pwd} user_tree_dn: ${user_tree_dn} user_filter: ${user_filter}
Decrypt Password
- Copy file from VMware Integrated OpenStack management to one of
keystone-apipod.# osctl get pod |grep keystone-api | tail -n 1 keystone-api-58b4d7dc48-np7jk 1/1 Running 0 6d18h #osctl cp /opt/vmware/data/health-check/fernet_decrypt.py keystone-api-58b4d7dc48-np7jk:tmp/ -c keystone-api
- To get the plaintext vCenter password, run the following command:
#osctl exec -it keystone-api-58b4d7dc48-np7jk -- bash -c "python /tmp/fernet_decrypt.py ${ldap_encrypted_pwd}" - The last line of the output is the plaintext password,
${ldap_pwd}.
Test the Connection
- Run
ldapsearchin akeystone-apipod.For example:#osctl exec -it keystone-api-58b4d7dc48-np7jk -- bash -c "ldapsearch -o nettimeout=5 -x -w ${ldap_pwd} -D ${ldap_user} -H ${ldap_url} -b ${user_tree_dn} ${user_filter}"Note: Replace the parameter with the corresponding values.If the
ldapsearchcommand fails, then check the LDAP user information in LDAP server and update it in VMware Integrated OpenStack.
Update LDAP Login Confidential
From management UI https://xxxxxxxx/ui/#/os/${your_os_deployment}/manage/setting/identity, check the LDAP login credentials and ensure it can login to LDAP server.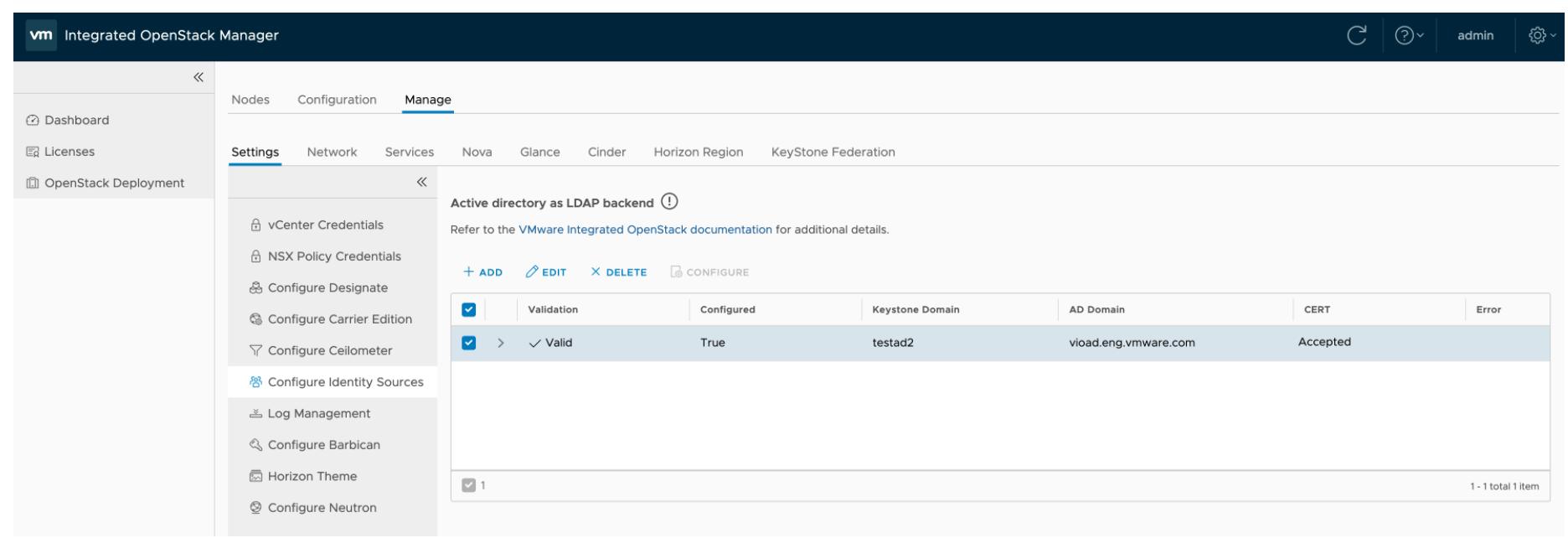
For more information on vCenter and NSX connection check, see vCenter Connection Check and NSX Connection Check.