The Cyber Recovery connector has several system and network requirements you need to be aware of before you deploy one.
vSphere and VMware Cloud on AWS Compatibility
For the most current information on vSphere and VMware Cloud on AWS compatibility with the service, see the VMware Product Interoperability Matrix.
For configuration limits of the service, see VMware Live Cyber Recovery Configuration Maximums.
Cyber Recovery connector System Requirements
| Site Resources | Value |
|---|---|
| VMware vCenter Server | See the VMware Product Interoperability Matrix for the latest supported versions. |
| CPU | 8 GHz (reserved) |
| RAM | 12 GiB (reserved) |
| Disk | 100 GiB virtual disk |
| Network connectivity | Required |
VMware Live Cyber Recovery strongly recommends that you configure NTP on all hosts in the cluster where you plan to deploy the Cyber Recovery connector. For more information, see Configuring Network Time Protocol (NTP) on an ESXi host using the vSphere Client.
Cyber Recovery connector Deployment Considerations
- Deploy one Cyber Recovery connector for every 250 VMs total in the protected site’s vCenter Server inventory, counting all VMs in vCenter Server, protected or not. If you have 1000 VMs, you do not have to deploy more than four Cyber Recovery connectors (although there is no harm in deploying additional Cyber Recovery connectors). You can add connectors as needed. You need not commit to a particular number of connectors up front.
- Deploy only one Cyber Recovery connector on a single host.
- Deploy at least two connectors per-protected site, for redundancy. VMware Live Cyber Recovery handles connector redundancy automatically. You do not need to register vCenter for additional connectors on the same protected site.
- Sites with more than 10,000 VMs might exhibit some responsiveness issues with the VMware Live Cyber Recovery UI, such as slow loading of pages or windows when previewing protection group VM membership, creating and editing recovery plans, and during plan compliance checking.
- VMware Live Cyber Recovery supports protecting up to 6000 VMs on a site with a single vCenter Server. To protect up to 6000 VMs in a single vCenter Server, you need four separate protected sites, each with its own cloud file system (four cloud file systems).
Cyber Recovery connector Networking Requirements
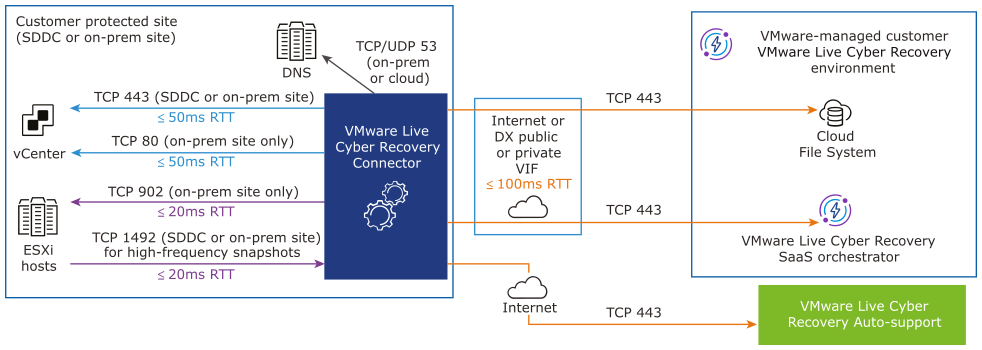
| Protocol | Port | Source | Destination | Service Description | Classification |
|---|---|---|---|---|---|
| Protected site | |||||
| TCP | 443 | Cyber Recovery connector | vCenter Server (on-premises site or SDDC) |
vCenter Server web service | Outbound |
| TCP | 80 | Cyber Recovery connector | vCenter Server (on-premises site only) |
vCenter Server web service | Outbound |
| TCP | 902 | Cyber Recovery connector | ESXi Management IP address (on-premises site only) |
Reading/writing vdisks | Outbound |
| TCP | 1492 | ESXi hosts | Cyber Recovery connector (For on-premises sites. For VMware Cloud on AWS SDDCs, this outbound rule for ESXi hosts is already configured.) |
For high-frequency snapshots, reading/writing vdisks. | Inbound |
| VMware Live Cyber Recovery Components | |||||
| TCP | 443 | Cyber Recovery connector | Cloud file system |
Encrypted tunnel for data transfers and metadata operations | Outbound |
| TCP | 443 | Cyber Recovery connector | Orchestrator | Management service | Outbound |
| TCP | 443 | Cyber Recovery connector | VMware auto-support server | Support service | Outbound |