NSX Advanced Load Balancer supports user authentication using Lightweight Directory Access Protocol (LDAP). LDAP is a commonly used protocol for accessing a directory service. A directory service is a hierarchical object oriented database view of an authentication system. LDAP settings can be configured in an authentication profile.
Creating an LDAP Auth Profile
To create an LDAP Auth Profile, perform the following steps.
1. Navigate to .
2. Under the General tab, enter the Name of the profile and select the Type of the Auth Profile as LDAP.
3. Configure the LDAP settings.
4. Configure the HTTP Authentication settings.
5. Click Save.
Configuring LDAP Settings
1. Under the LDAP tab, click Add to enter the LDAP server IPs.
For Controller authentication, multiple LDAP servers are supported only if they belong to the same cluster. Otherwise, the Controller tries to authenticate with the first reachable server.
2. Select the LDAP Connection Security Mode, if required.
3. Enter the Port on which NSX Advanced Load Balancer queries the LDAP servers. Use port 389 for LDAP and 636 for LDAPS (SSL).
Just configuring the port does not determine if the LDAP security mode is LDAPS. Hence, explicitly select LDAPS as the LDAP Connection Security Mode to ensure secure LDAP is in use.
4. In the Base DN field, enter the top level path in the directory server object hierarchy.
Using a specific base DN expedites all queries to the LDAP server in contrary to a generic, high level base DN which makes the queries reach out to more parts of the directory's hierarchy. The base DN must be set to the topmost (most general) path to which the account has access.

5. Select the LDAP Bind Settings.
- Administrator Bind
-
The administrator account provided will be used to search for users and user group memberships across the LDAP server.
Note:Admin Bind is the recommended LDAP Bind option.
Enter the Admin Bind DN and Admin Bind Password. The account used must have access to search the directory tree for both users and user groups.
NSX Advanced Load Balancer uses the configuration to search for users or groups. An LDAP search typically requires:
Top-level directory hierarchy (search DN) to start the search.
The scope value limits the search to one of the following: base (one-level deep) or entire subtree.
Filter to match only on entries of a given class or category
Note:If the LDAP admin bind password is changed, the user must restart the NSX Advanced Load Balancer portal for the authentication to work due to a limitation in the uwsgi server.
- Anonymous Bind
-
Anonymous bind is useful when you do not have access to an administrator account on the LDAP server(s). Anonymous bind can only be used to authenticate the user and cannot be used to authorize the user.
To configure Anonymous Bind, enter the following:
User DN Pattern used to bind an LDAP user after replacing the user token with the real user name. The pattern must match the user record path in the LDAP server.
User Token which is replaced with the real user name in the user DN pattern.
User ID Attribute is the unique property that identifies a single user record. This value must match with the user name used at the login prompt.
Note:Authentication profiles that use anonymous bind cannot be used for role or tenant mapping.
An LDAP profile configured with Anonymous Bind is as shown below:
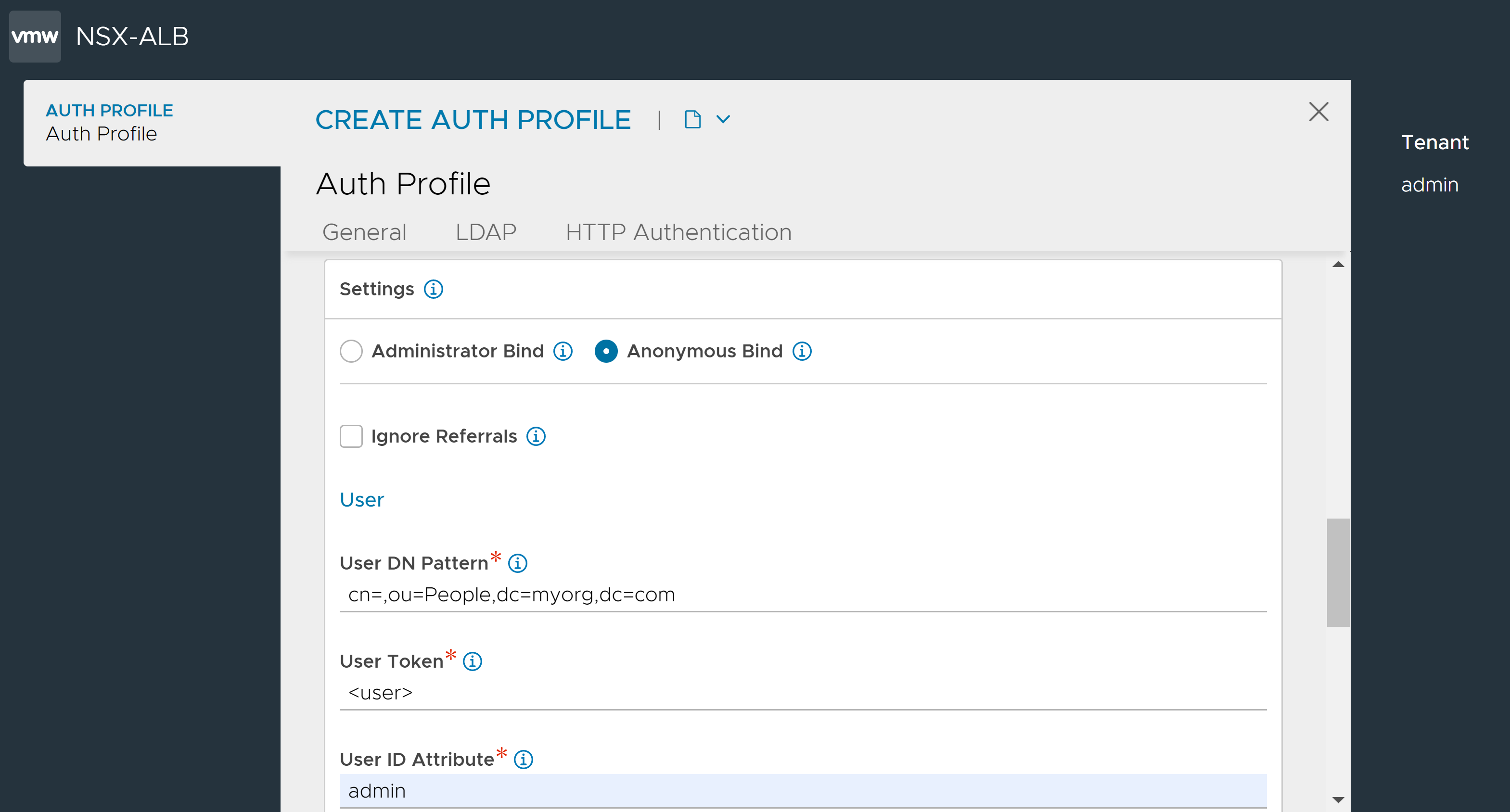
6. Enable Ignore Referrals for the group search to skip referrals links that connect to another LDAP server.
Enabling the option Ignore Referrals can quicken the group searches by preventing delay in LDAP group search due to unnecessary referral searches.
7. Under User, define the scope of search for users who log into NSX Advanced Load Balancer.
- User Search DN
-
LDAP user search DN is the root of search for a given user in the LDAP directory. Only user records present in this LDAP directory sub-tree are allowed for authentication. Base DN value is used if this value is not configured.
- User Search Scope
-
LDAP user search scope defines how deep to search for the user starting from user search DN.
- User ID Attribute
-
LDAP user ID attribute is the login attribute that uniquely identifies a single user record. The value of this attribute must match the user name used at the login prompt.
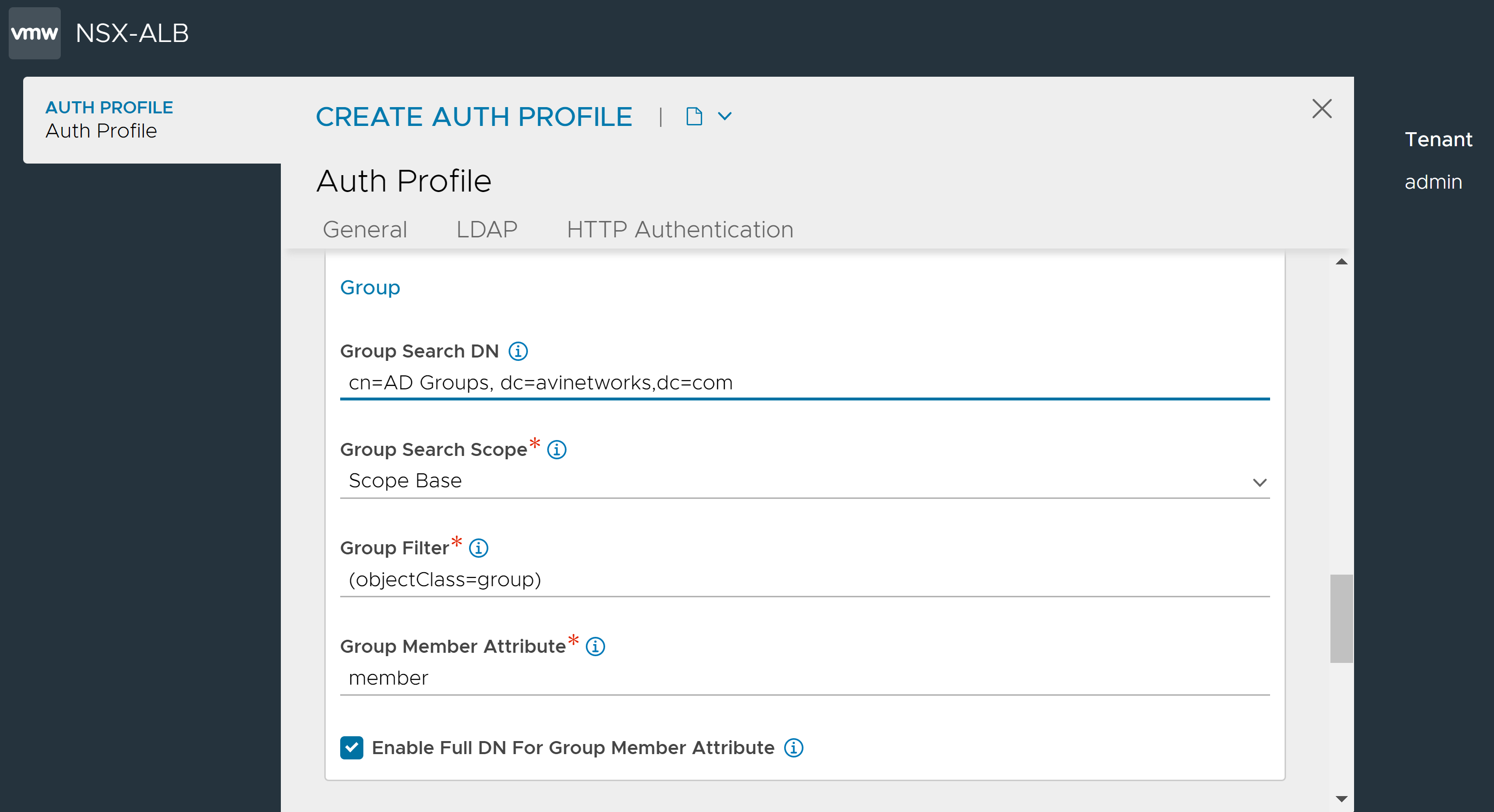
8. Under Group, define the parameters to search for a user's group membership.
- Group Search DN
-
LDAP group search DN is the root of search for a given group in the LDAP directory. Only matching groups present in this LDAP directory sub-tree will be checked for user membership.
If this value is not defined, the base DN value is used.
- Group Search Scope
-
Define the LDAP group search scope using filters for the group starting from the group search DN.
The different levels of group search available are:
Scope Base
Scope One Level
Scope Subtree
- Group Filter
-
A search can find many different types of objects under the search DN. Specify the Group Filter to pick up objects specific to the group only.
NSX Advanced Load Balancer appends a user-specific group membership filter to the configured group filter to check a specific user’s group membership.
- Group Member Attribute
-
Enter the LDAP group attribute that identifies each of the group members.
For example, member and memberUid are commonly used attributes.
- Enable Full DN For Group Member Attribute
-
Enable this option if the group member entries have full DNs instead of just user ID attributes.
For example, a configured group filter (objectClass=group) is extended by NSX Advanced Load Balancer to a full filter when user “bob” logs in to something such as the following: (&(objectClass=group)(member=bob))
After configuring the LDAP settings, configure the settings under the HTTP Authentication tab.
Configuring HTTP Authentication
Enter the Client User ID Header Name to insert an HTTP header into the client request before it is sent to the destination server. This field is used to name the header. The value will be the client’s User ID. This same User ID value will be used to populate the User ID field in the Virtual Service’s logs.
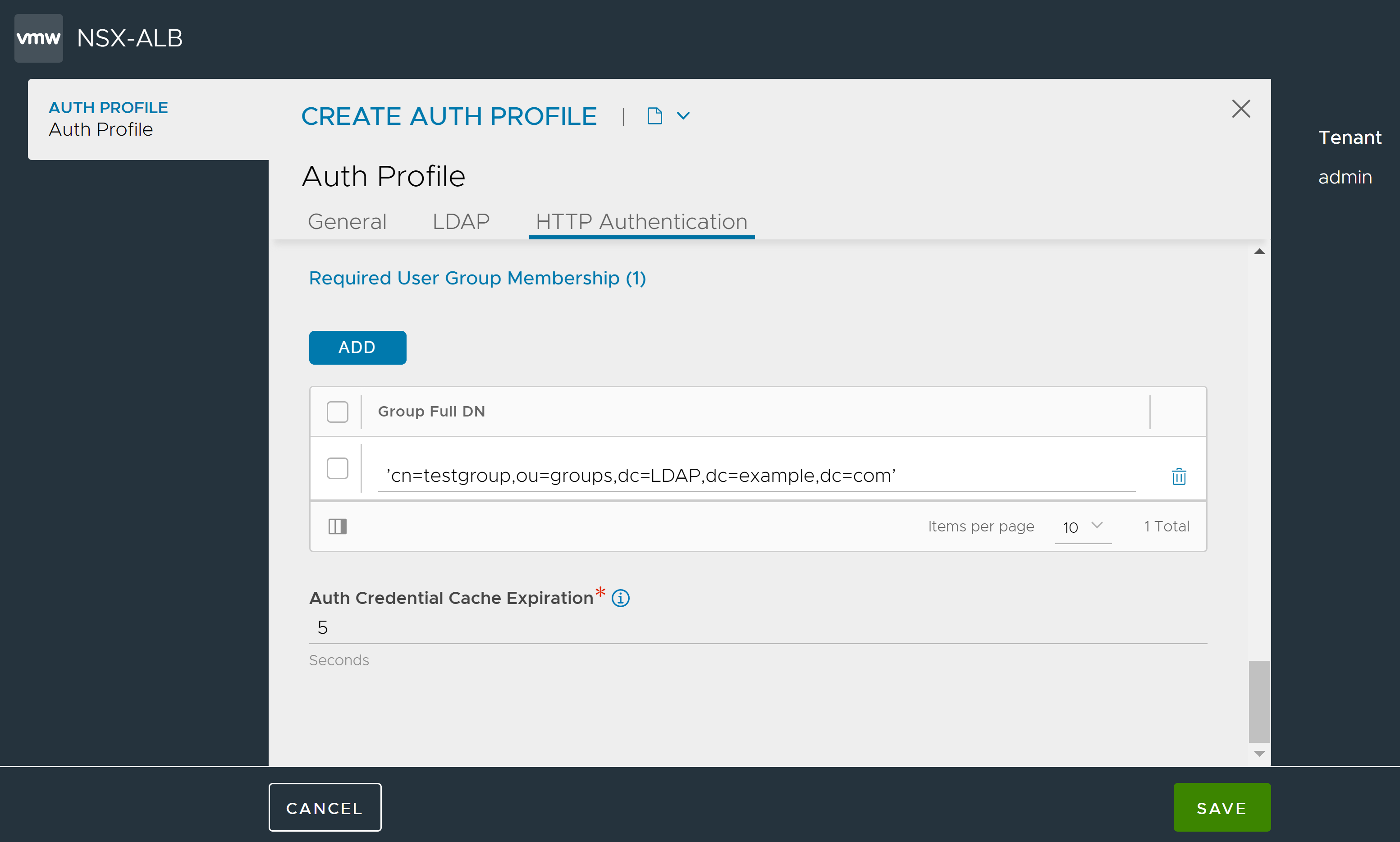
Under Required User Group Membership, click Add to identify the groups which the user must be a member of. Each group is identified by the DN, for example, ’cn=testgroup,ou=groups,dc=LDAP,dc=example,dc=com’.
In the field Auth Credential Cache Expiration, specify the maximum allowed length of time for which a client’s authentication is cached.
Click Save to complete the LDAP Auth profile creation.