This section describes the examples for bot management logs.
Example 1
In the example below, NSX Advanced Load Balancer logs displays all the important data points like classification, client type, identifier and confidence level.
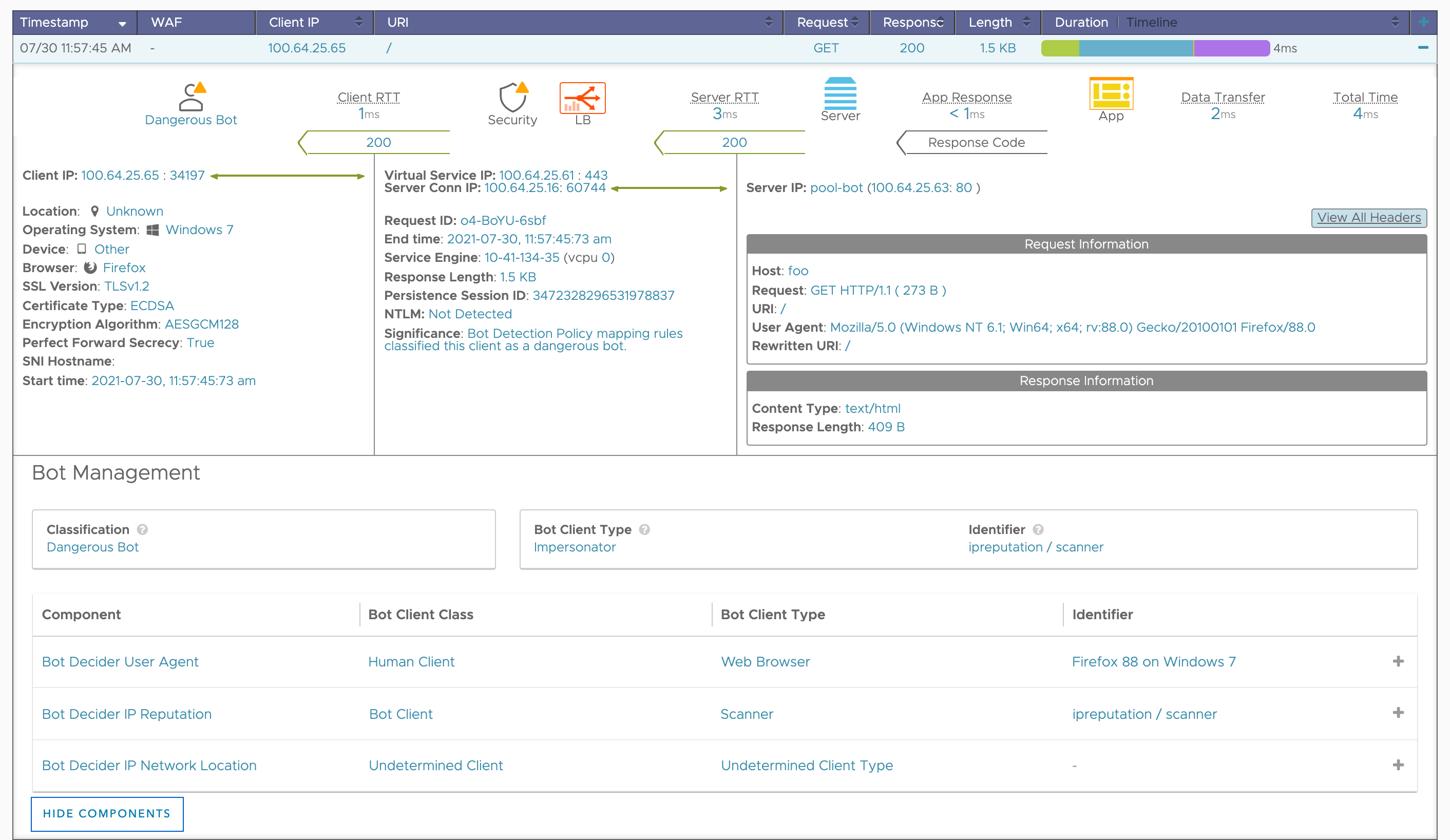
Example 2
On the right side of the UI screen under logs, you can view the consolidated logs. Under summary, you can view Bot analytics. The Bot analytics displays the different types of Bot that is detected in the given period of time.
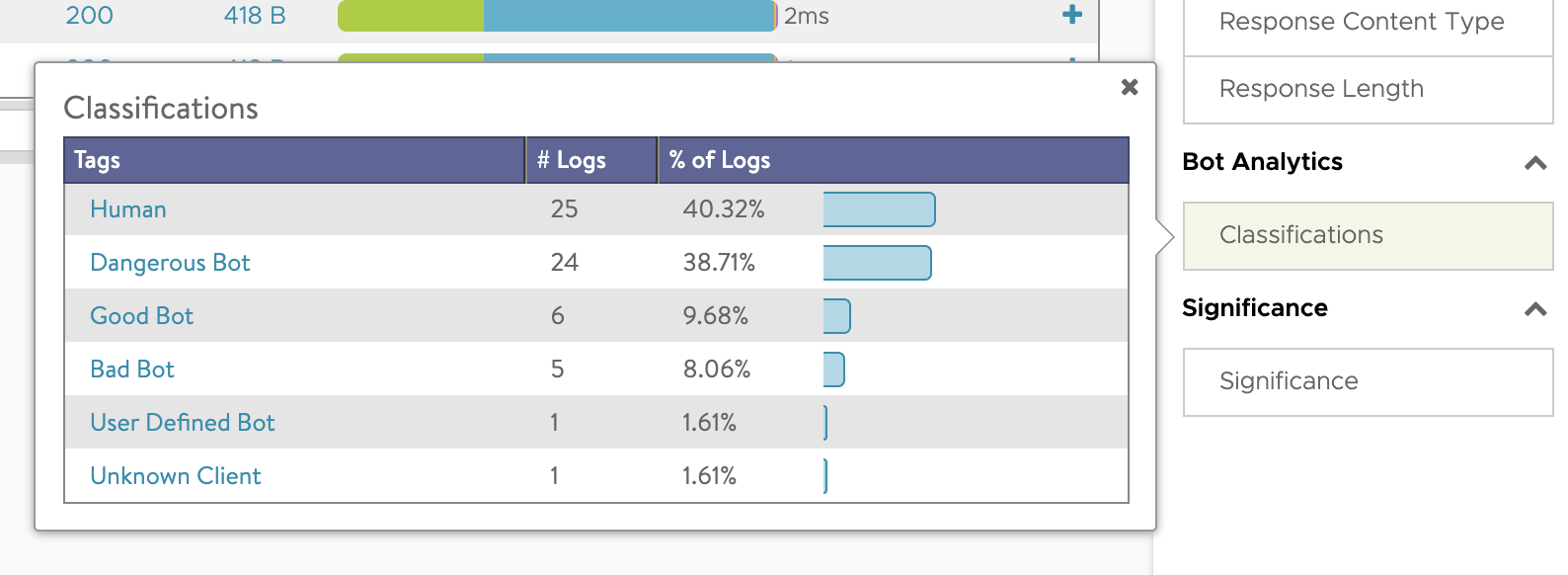
Special Cases
If the requirement is to skip Bot detection on certain requests, for instance, for requests coming from certain client IPs can be done by creating allow list in Bot policy.
The following are the configuration steps:
[admin:ctrl]: > configure botdetectionpolicy System-BotDetectionPolicy [admin:ctrl]: botdetectionpolicy> allow_list [admin:ctrl]: botdetectionpolicy:allow_list> [admin:ctrl]: botdetectionpolicy:allow_list> rules New object being created [admin:ctrl]: botdetectionpolicy:allow_list:rules> name rule1 [admin:ctrl]: botdetectionpolicy:allow_list:rules> condition [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition> [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition> client_ip [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition:client_ip> match_criteria is_in [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition:client_ip> [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition:client_ip> addrs 1.1.1.1 [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition:client_ip> save [admin:ctrl]: botdetectionpolicy:allow_list:rules:condition> save [admin:ctrl]: botdetectionpolicy:allow_list:rules> [admin:ctrl]: botdetectionpolicy:allow_list:rules> action bot_action_ bot_action_bypass Bypass BOT detection. bot_action_continue Stop allow-list processing and move on to BOT detection. [admin:ctrl]: botdetectionpolicy:allow_list:rules> action bot_action_ bot_action_bypass Bypass BOT detection. bot_action_continue Stop allow-list processing and move on to BOT detection. [admin:ctrl]: botdetectionpolicy:allow_list:rules> action bot_action_bypass [admin:ctrl]: botdetectionpolicy:allow_list:rules> save [admin:ctrl]: botdetectionpolicy:allow_list> save [admin:ctrl]: botdetectionpolicy> save
Similarly, you can create more rules to match on other criteria like path, host header, cookie, headers, protocol etc.
allow_listis a list of rules consisting of conditions mapped to the actions. In each rule, the condition can contain properties of the request likeclient_ip, host header etc. The actions can be “bypass” (skip all further bot detection) or “continue” (Stop allow-list processing and move on to BOT detection).You need to disable one of the three decision components, for instance, you can disable IP location check component.
[admin:ctrl]:> configure botdetectionpolicy System-BotDetectionPolicy [admin:ctrl]:botdetectionpolicy> ip_location_detector [admin:ctrl]:botdetectionpolicy:ip_location_detector> no enabled +--------------------------------+-------------------------------+ | Field | Value | +--------------------------------+-------------------------------+ | enabled | False | | ip_location_db_ref | System-GeoDB | | system_cloud_providers_ref | System-BotCloudProviders | | system_search_engines_ref | System-BotSearchEngines | +--------------------------------+-------------------------------+ [admin:ctrl]:botdetectionpolicy:ip_location_detector> save [admin:ctrl]:botdetectionpolicy>save
Note:The name of individual BotMappingRule objects in a BotMapping object is mandatory. Hence, you will not be able to create any new objects without a name. Existing objects are assigned an auto-generated name during the upgrade, following the pattern ‘Mapping Rule 0’, ‘Mapping Rule 1’ and so on, where the number in the name is the index of the rule.