This section explains how to Configure Stronger SSL Cipher.
Strength
SSL ciphers are defined by the Profile. Within a profile, List view and string view are the two modes for configuring ciphers.
For more information, see Apple’s App Transport Security topic in the VMware NSX Advanced Load BalancerConfiguration Guide.
SSL Rating
Modifying or reordering the list will alter the associated SSL rating in the top-right corner of the SSL/ TLS Profile edit window. This provides insight into the encryption performance, security, and client compatibility of the selected ciphers. This ranking is only made against the validated ciphers from the List View mode.
List View
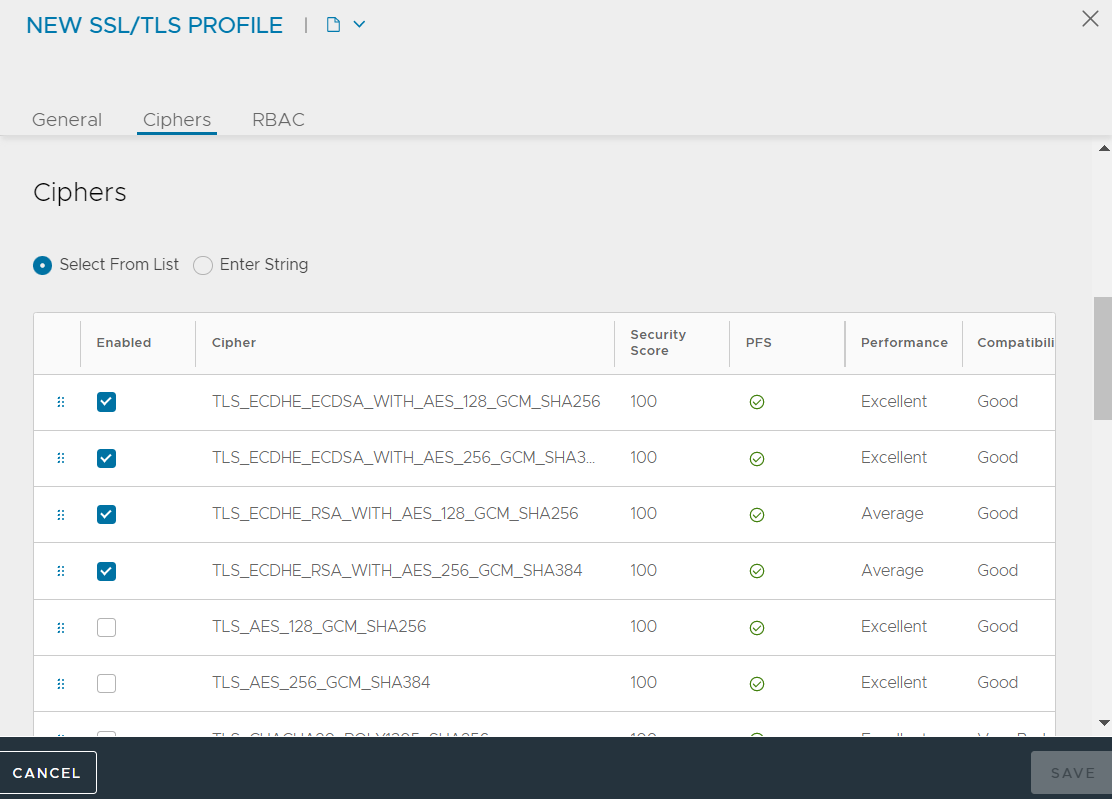
String View
The second cipher configuration mode allows accepted ciphers to be added as a string, similar to the OpenSSL syntax for viewing and setting ciphers. For this mode, NSX Advanced Load Balancer accepts all TLS 1.0 - 1.2, and Elliptic Curve ciphers from https://www.openssl.org/docs/man1.0.2/apps/ciphers.html. In this mode, the administrator must determine if the enabled ciphers are secure. You can set strong security by employing a known cipher suite, such as HIGH.
ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA:ECDHE-ECDSA-AES256