To create or edit an SSL profile follow the below:
Click Create to see a window (as shown in the below screenshots). In this, TLS1.3 is not added to the list of Accepted Versions.
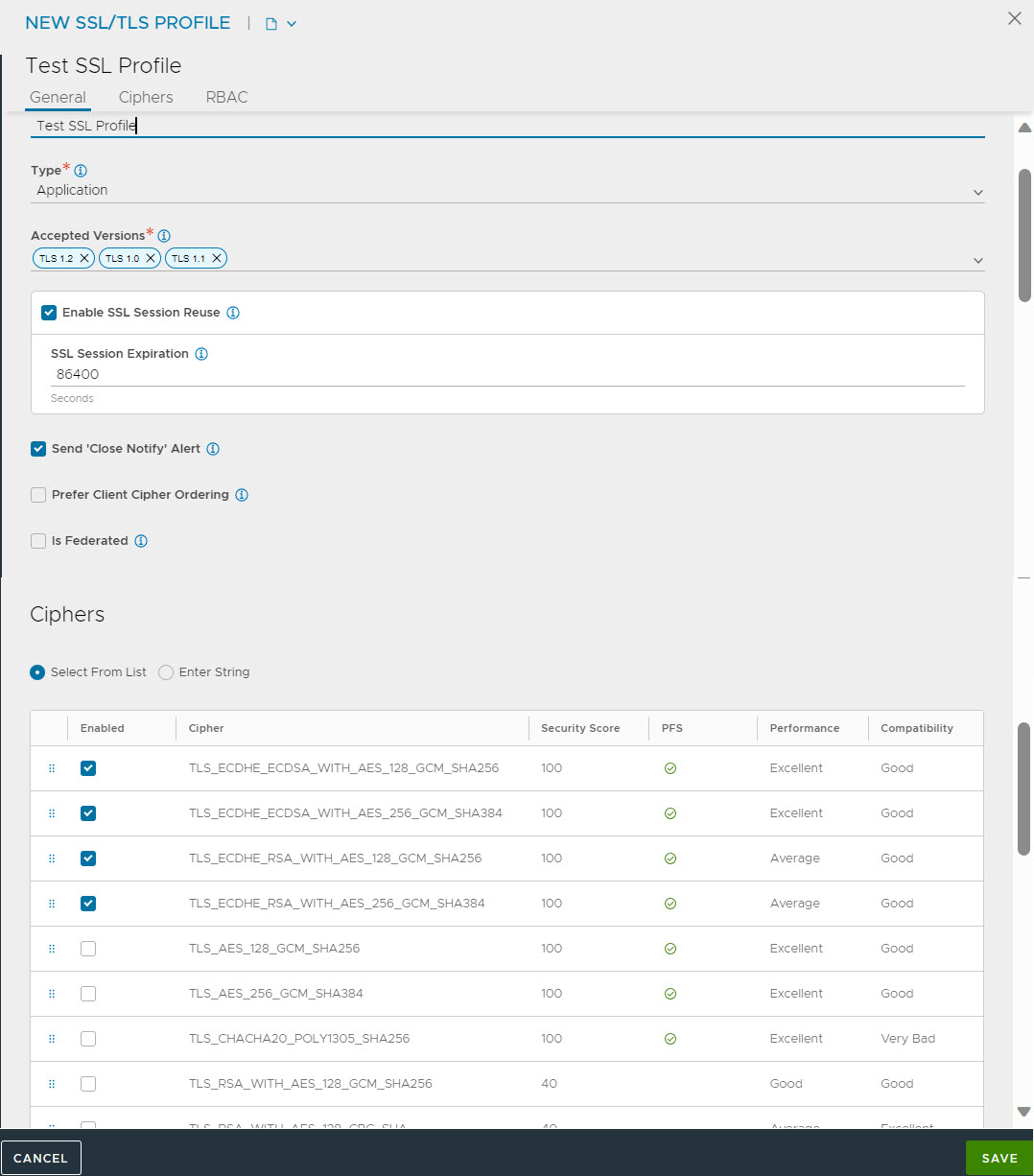
Adding the TLS 1.3 option causes the Early Data option to appear.

Selecting the TLS 1.2 option, the following ciphers are enabled.
All cipher listed in both System-Standard and System-Standard-PFS SSL profiles are supported in both FIPS and non-FIPS modes of operation. The only exception is 3DES and TLS1.3 ciphers, since the FIPS stack does not support the TLS1.3 protocol.
UI Fields
SSL/TLS Name: Specify a unique name for the SSL/ TLS profile.
Type: Choose Application if the profile is to be associated with a virtual service, System if the profile is to be associated with the Controller.
Ciphers: Ciphers may be chosen from the default List view or a String. The String view is for compatibility with OpenSSL-formatted cipher strings. When using String view, NSX Advanced Load Balancer does not provide an SSL rating, nor a score for the selected ciphers.
SSL Rating: This is a simple rollup of the security, compatibility, and performance of the ciphers chosen from the list. Often ciphers may have great performance but very low security. The SSL rating attempts to provide some insight into the outcome of the selected ciphers. NSX Advanced Load Balancer Networks may change the score of certain ciphers from time to time, as new vulnerabilities are discovered. This does not impact or change an existing NSX Advanced Load Balancer deployment, but it does mean the score for the profile, and potentially the security penalty of a virtual service, may change to reflect the new information.
Version: NSX Advanced Load Balancer supports versions SSL 3.0, TLS 1.0 and newer. The older SSL 2.0 protocol is no longer supported. TLS 1.3 protocol is supported. Users must select one or more of the three supported TLS 1.3 ciphers in the list of ciphers or configure them in the Ciphersuites option under the String view.
Send “close notify” alert: Gracefully inform the client of the closure of an SSL session. This is similar to TCP doing a FIN/ACK rather than an RST.
Prefer client cipher ordering: Off by default, set this to On if you prefer the client’s ordering.
Enable SSL Session Reuse: On by default, this option persists a client’s SSL session across TCP connections after the first occurs.
SSL Session Expiration: Set the length of time in seconds before an SSL session expires.
Ciphers: When negotiating ciphers with the client, NSX Advanced Load Balancer will give preference to ciphers in the order listed. The default cipher list prioritizes elliptic curve with PFS, followed by less secure, non-PFS and slow RSA-based ciphers. Enable, deactivate, and reorder the ciphers through the List view. In the String view, manually enter the cipher strings through the OpenSSL format, which is documented on the OpenSSl.org website. You may use an SSL/ TLS profile with both an RSA and an elliptic curve certificate. These two types of certificates can use different types of ciphers, so it is important to incorporate ciphers for both types in the profile if both types of certs may be used. As with all security, NSX Advanced Load Balancer Networks recommends diligence to understand the dynamic nature of security and to ensure that NSX Advanced Load Balancer is always up to date.
Ciphersuites: This option exclusively configures TLS 1.3 protocol ciphers. Currently, NSX Advanced Load Balancer supports the below:
TLS_AES_128_GCM_SHA256
TLS_AES_256_GCM_SHA384
TLS_CHACHA20_POLY1305_SHA256
These ciphers will only work with the TLS 1.3 protocol. The old cipher suites cannot be used with the TLS 1.3 protocol.
Early Data: This option enables TLS-v1.3-terminated applications to send application data (referred to here as early data or 0-RTT data) without having to first wait for the TLS handshake to complete. This saves one full round-trip time between the client and server before the client requests can be processed. SSL session reuse must be enabled to use the Early Data option.
NSX Advanced Load Balancer supports configuring Elliptic Curve Cryptography(ECC) Cipher Suites in SSL profile.