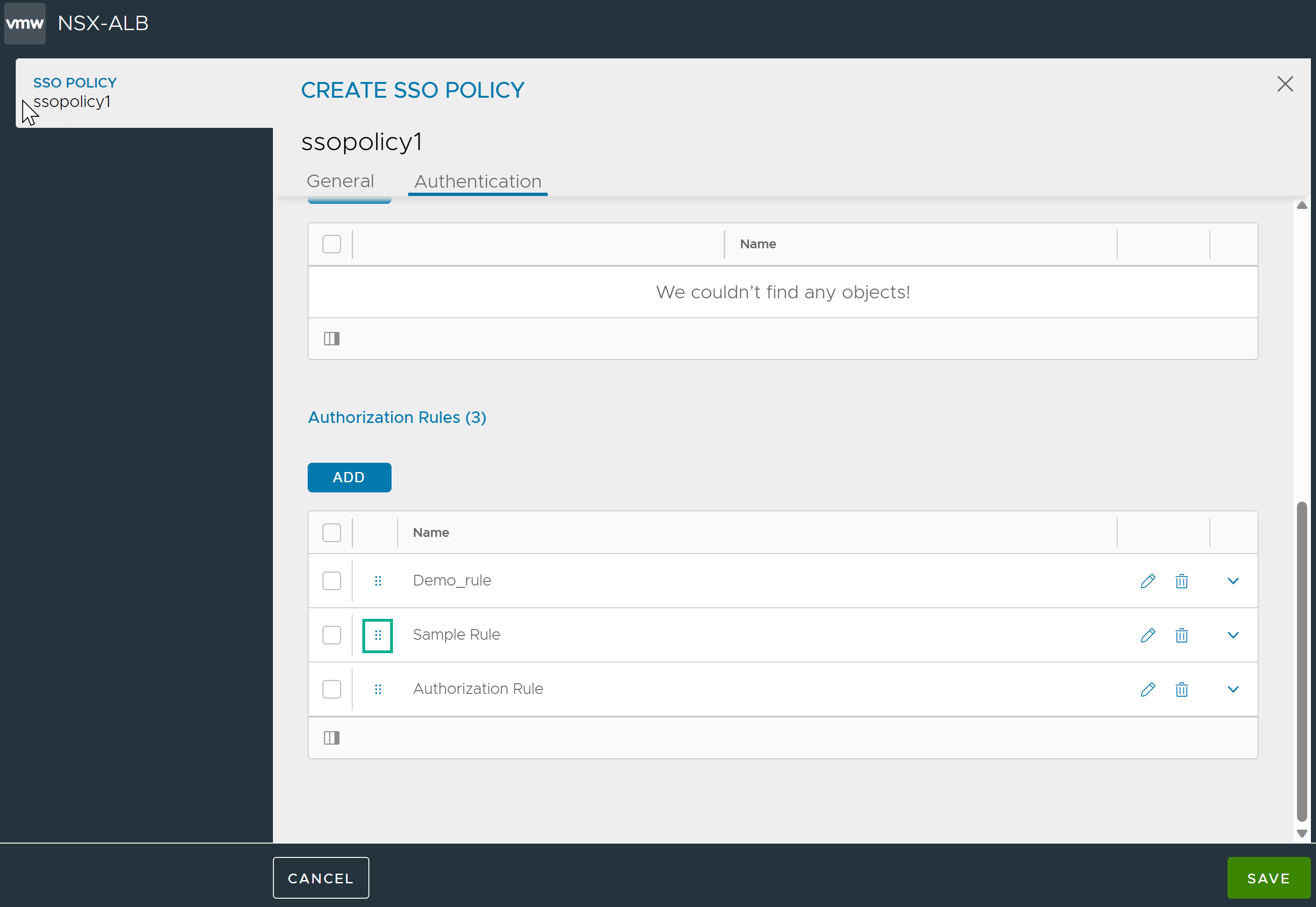
Authorization is the process of managing and controlling the access provided to the users. Authorization policies determine if the authenticated user is permitted to have access to a resource or not.
Authorization Rules
To identify if an authorization rule must be applied, match conditions are applied:
NSX Advanced Load Balancer supports the following match conditions:
Match Condition |
Description |
Attribute |
Match based on the attributes that are part of the responses |
Path |
Match based on the URI Path |
Host Header |
Match based on the host header that is present in incoming request |
Method |
Match based on the HTTP request method, for instance, GET, POST |
Match types based on Host header and path can be configured to identify case-sensitivity.
Action Types
You can use action types to define the consequences to a request match against an authorization rule.
Action Type |
Description |
Allow Access |
Allow access on authorization policy rule match |
Close Connection |
Close the connection on authorization policy rule match |
HTTP Local Response |
Send HTTP local response on authorization policy rule match |
Scenario
To understand how match conditions work, consider a scenario in which the request has to meet specific conditions to allow access to the path /aviadmin.
The aviadmin path must be allowed only for the user with the email address [email protected].
Only GET requests are allowed for this path.
Requests carrying host-header admin.acme.com are only allowed to access this path.
If the above conditions are met, only then the access must be allowed. Otherwise, 403 response code must be returned to the user.
For this scenario, break down of the authorization rule is as follows:
Critera |
Rule |
|---|---|
Attribute |
Match is successful if the email attribute is [email protected] |
Host Header |
Match is successful if the requests have the host header admin.acme.com |
HTTP Method |
Only HTTP GET requests are allowed for the path. |
Condition |
Action Type |
|---|---|
Request meets the defined conditions |
Allow Access |
Request fails to meet the defined conditions |
Respond with Status Code 403 |
Configuring Match Criteria and Action
The attributes or values in the responses are matched through attribute matches against the configured attributes and its values. The attributes can have zero or more values associated with each of them. You can configure multiple attributes and values as part of each rule. The rule is matched only if all the attributes are matched.
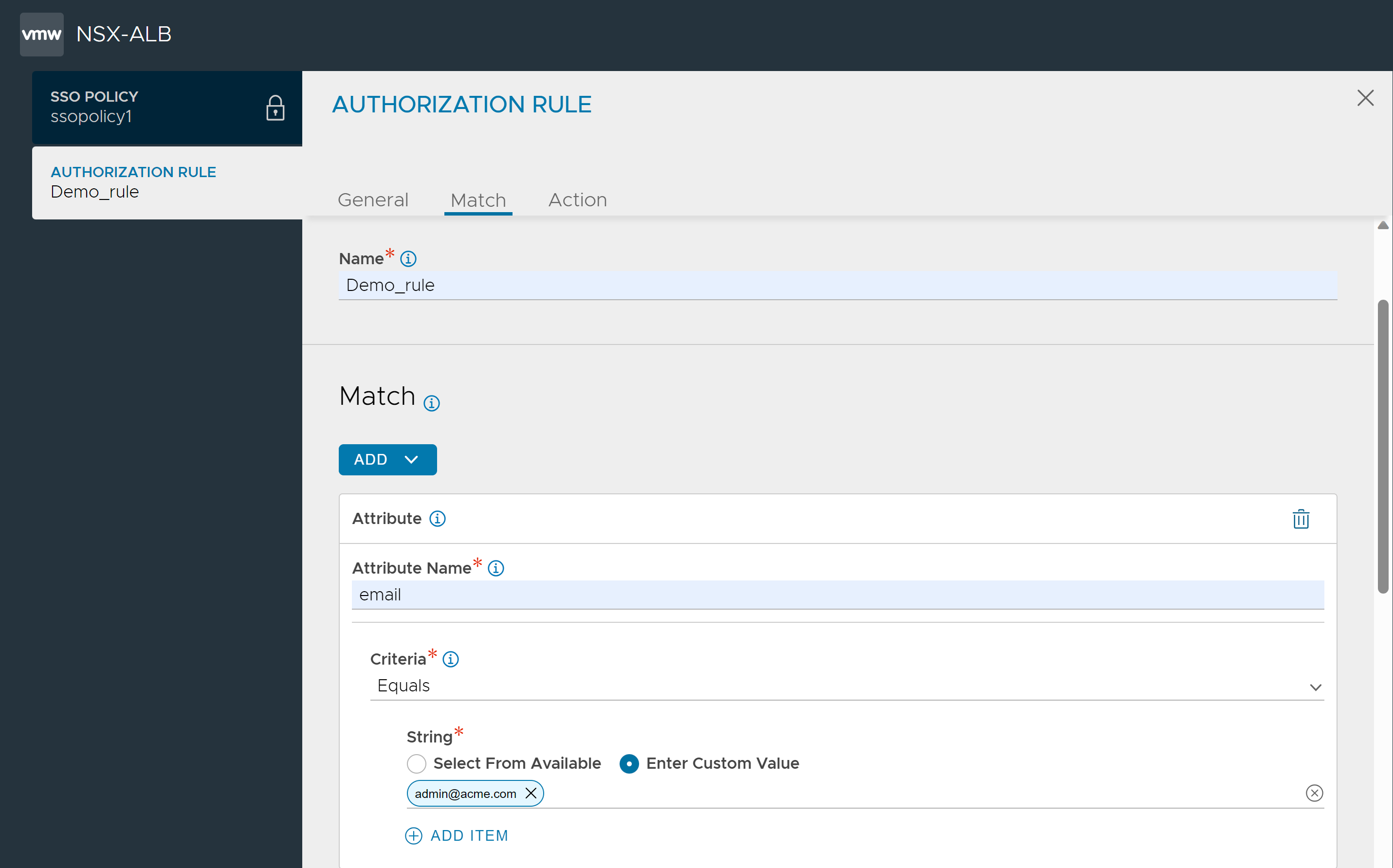
In the Authorization Rule screen, follow the steps below to define the match criteria,
Click the Add drop down menu.
Select Attribute.
Enter the Attribute Name.
Select Equals as the Criteria.
Under String, select Enter Custom Value.
Enter [email protected] as custom string value.
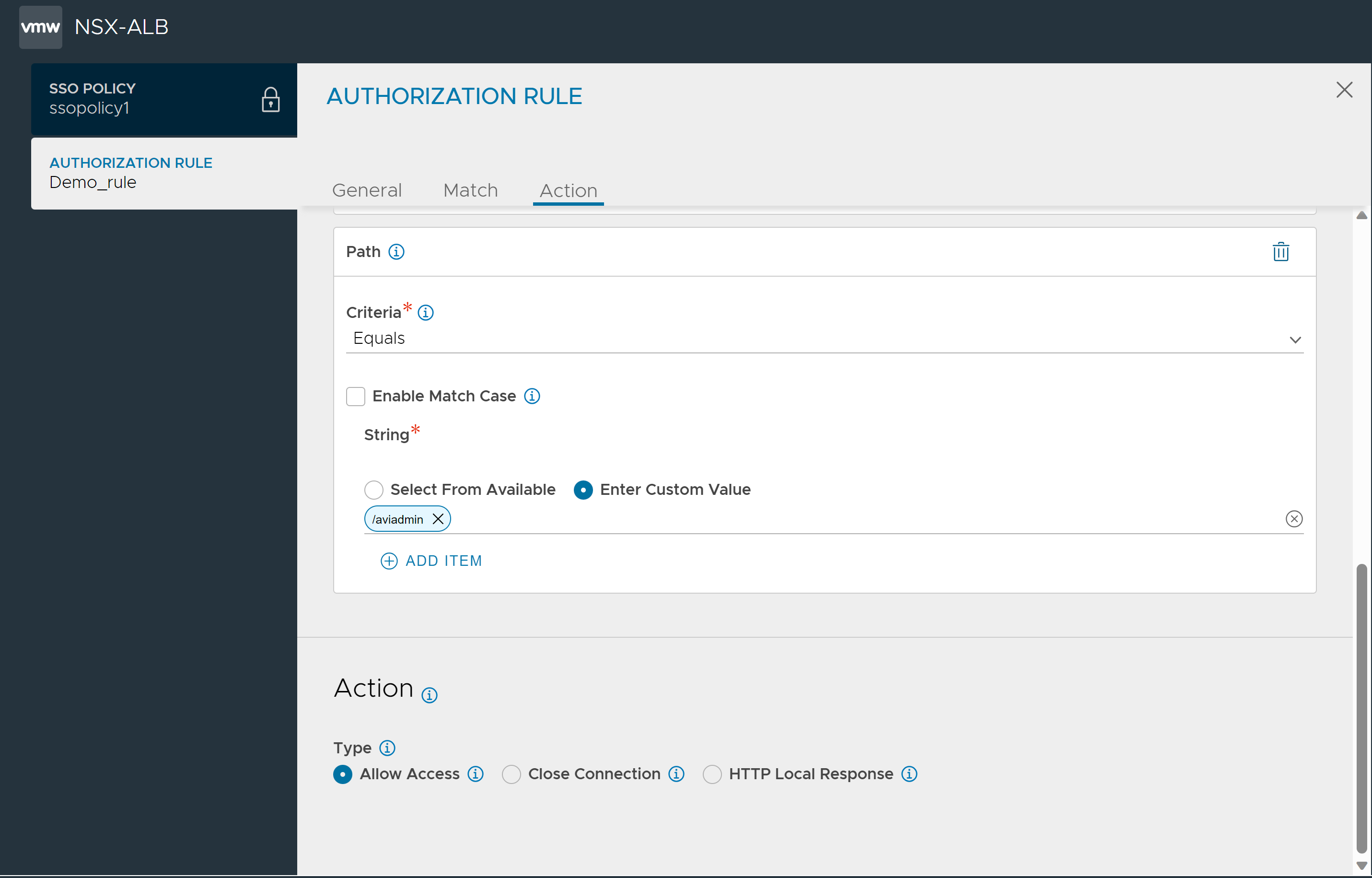
To add match criteria, click the Add drop down menu.
Select Path and similarly configure the path as shown below:
Add match criteria, select Host Header and configure as shown below:
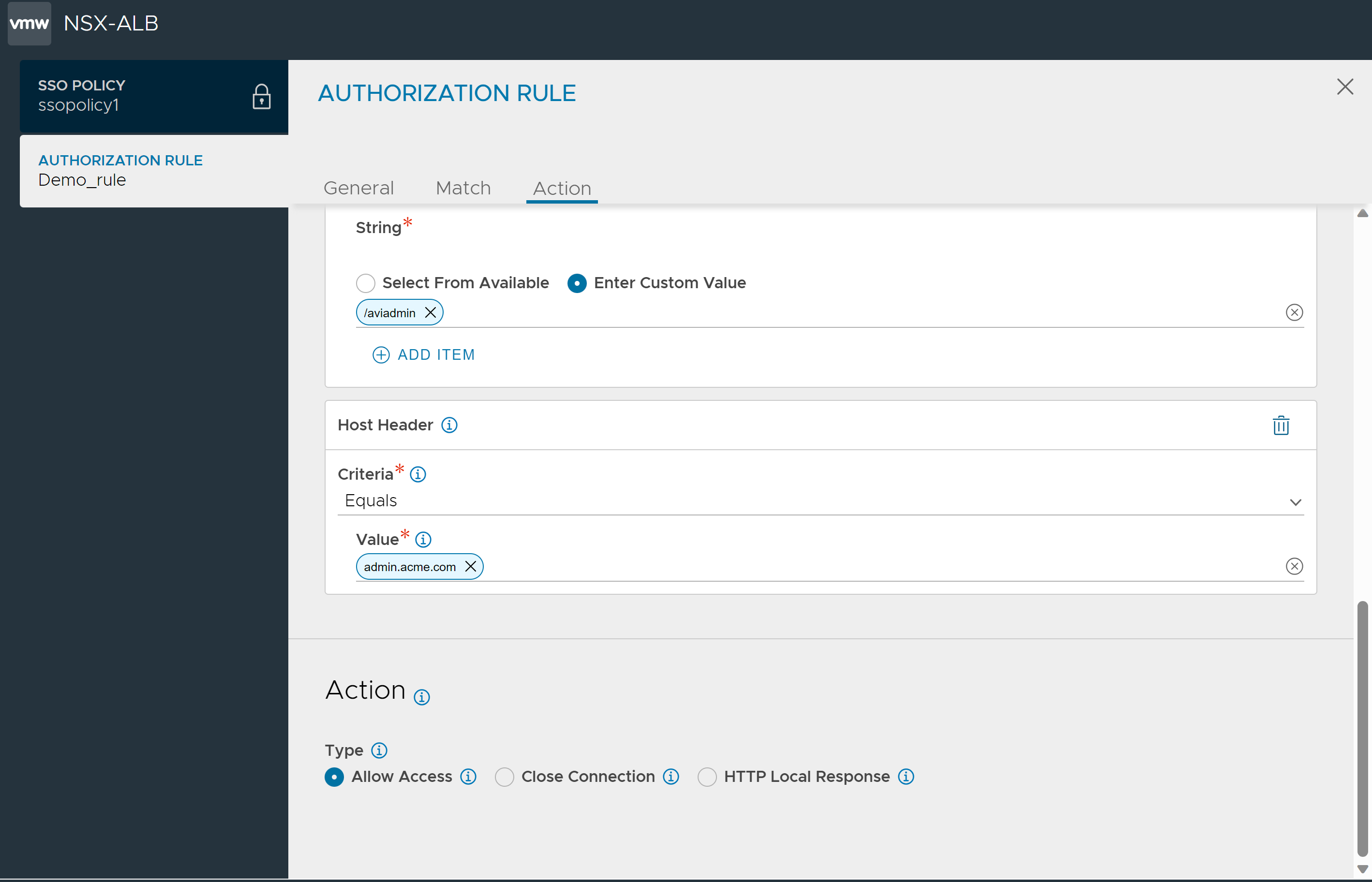
Add match criteria, select HTTP Method, and configure as shown below:
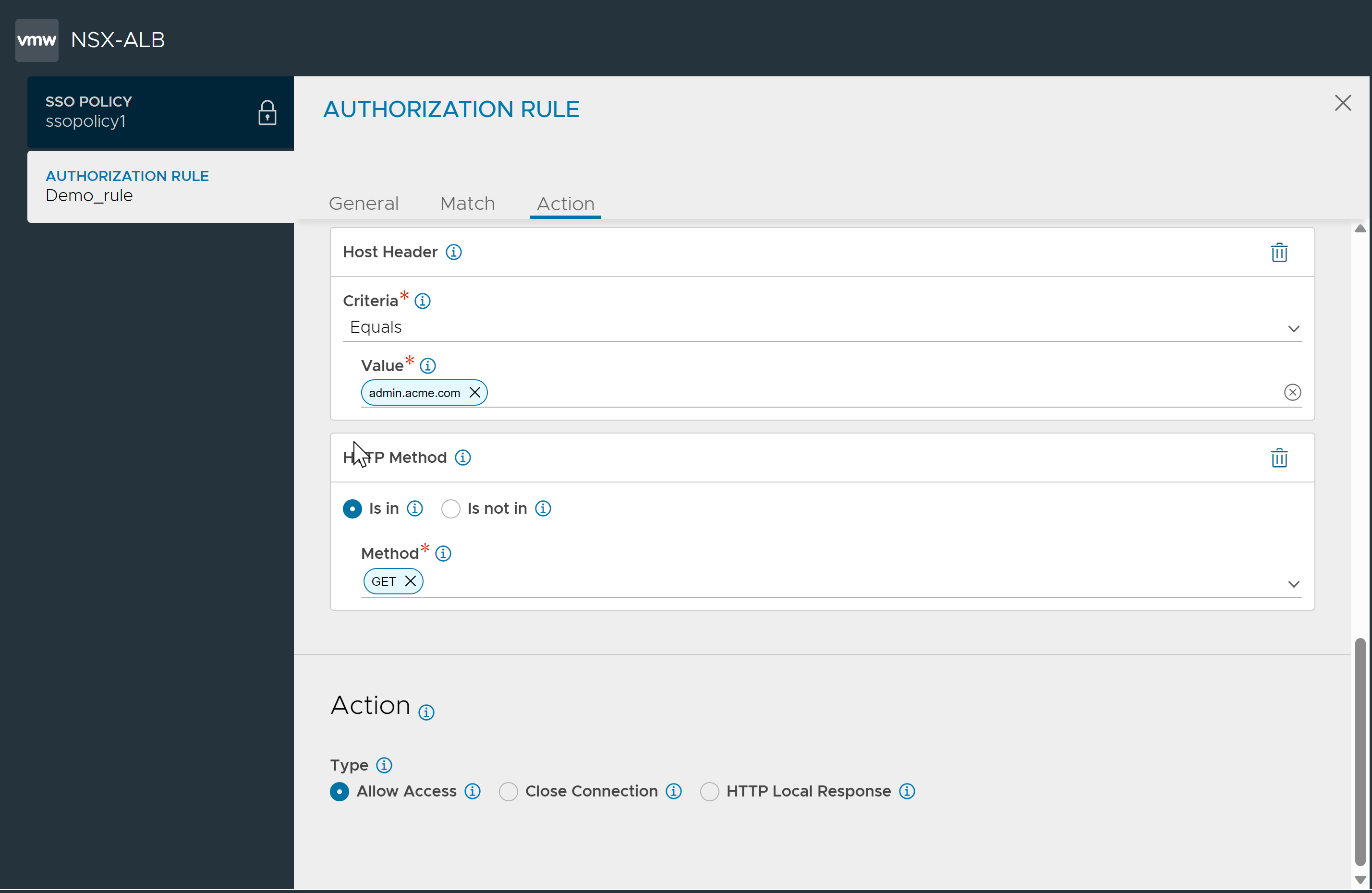
Under Action,
Select HTTP Local Response as the Type.
Select the Status Code as 403.
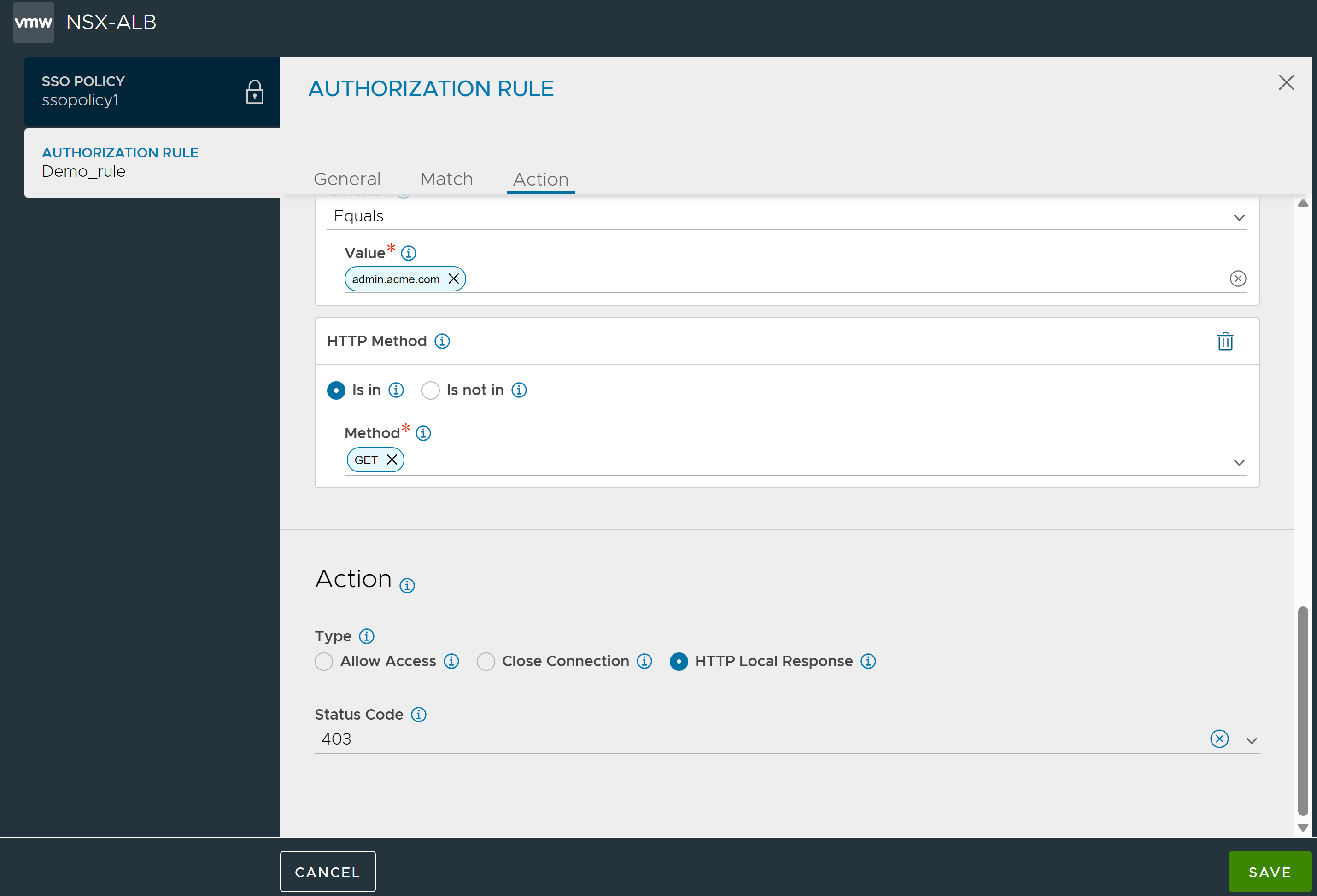
Click Save,
Configuring Multiple Rules
From the SSO policy, you can create multiple authorization rules by clicking the Add button.
The rules are prioritized according to the sequence in which they are listed in the SSO policy.
To change the sequence, click the elipses and drag the policy to the required position.