The NSX Advanced Load Balancer supports the ability to terminate SSL connections between the client and the virtual service, and to enable encryption between NSX Advanced Load Balancer and the back-end servers.
The contains the list of accepted SSL versions and the prioritized list of SSL ciphers. To terminate client SSL connections, both an SSL profile and an SSL certificate must be assigned to the virtual service. To also encrypt traffic between NSX Advanced Load Balancer and the servers, an SSL profile must be assigned to the pool. When creating a new virtual service through the basic mode, the default system SSL profile is automatically used.
Each SSL profile contains default groupings of supported SSL ciphers and versions that may be used with RSA or an elliptic curve certificates, or both. Ensure that any new profile created includes ciphers that are appropriate for the certificate type that will be used. The default SSL profile included with NSX Advanced Load Balancer is optimized for security, rather than just prioritizing the fastest ciphers.
Creating a new SSL/ TLS profile or using an existing profile entails various trade-offs between security, compatibility, and computational expense. For example, increasing the list of accepted ciphers and SSL versions increases the compatibility with clients, while also potentially lowering security.
NSX Advanced Load Balancer can accommodate a broader set of security needs within a client community by associating multiple SSL profiles with a single virtual service, and have the Service Engines choose which to use based on the client’s IP address.
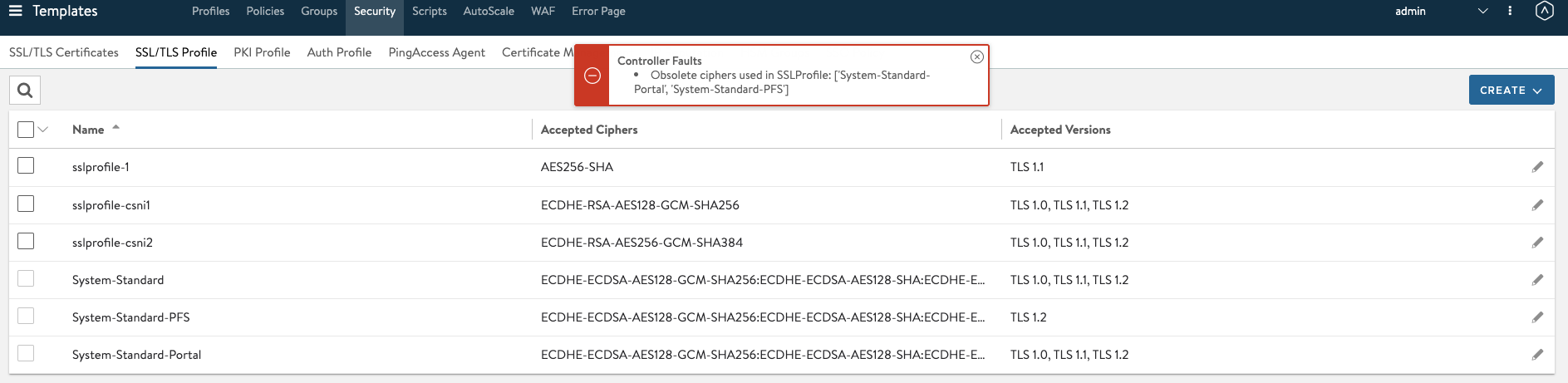
The virtual service creation without SSL profile must default to System-Standard-PFS SSL profile.Selecting unsafe ciphers will display the following error message.