Starting with NSX Advanced Load Balancer release 21.1.1, ICAP support is available for the NSX Defender server to prevent malicious file uploads. When compared with OPSWAT, there are minor differences in the method using which the NSX Defender sends files back to the NSX Advanced Load Balancer.
This section covers the following:
NSX Defender ICAP configuration
NSX Advanced Load Balancer integration with NSX Defender
Required visibility changes for NSX Defender reported information
Configuring NSX Defender for ICAP
Log in to the NSX Defender and navigate to .
Enable the following options:
ICAP Server
INLINE ANALYSIS
Under the Blocking pages section, enable the following:
BLOCKED PAGE DETAILS
X-LASTLINE HEADER
LASTLINE LOGO
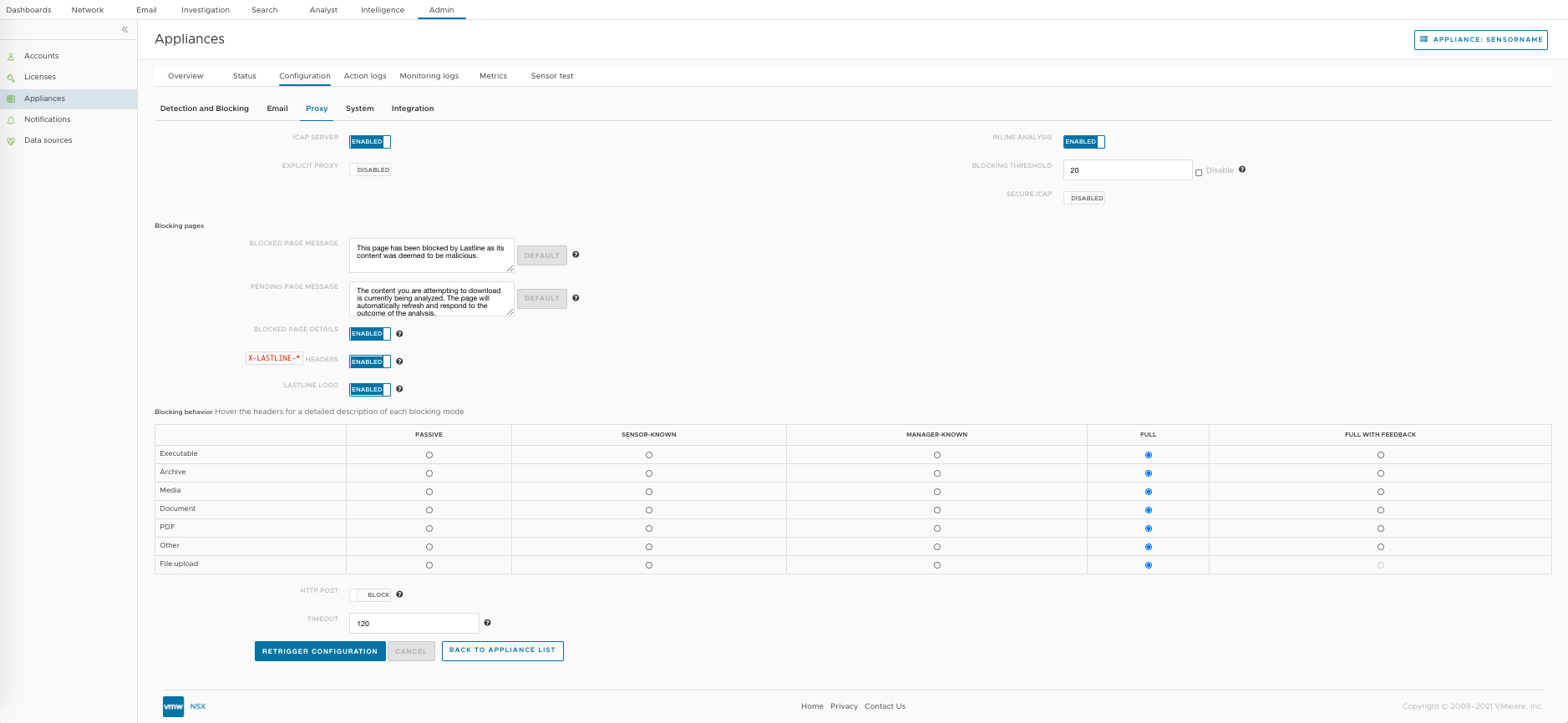
The following are the blocking types available on the NSX Defender. For more information, see NSX Defender documentation.
PASSIVE - No blocking is attempted on this type of file, but any relevant content will be analyzed.
SENSOR-KNOWN - Block all artifacts known to be malicious by the Sensor (listed in its local cache). This method offers the lowest levels of protection but ensures minimal lag.
MANAGER-KNOWN - Block all artifacts known to be malicious by the NSX Defender Manager. These data are listed in the Manager cache and shared across all managed appliances.
FULL - This mode allows the proxy to stall an ICAP request for until required to provide a verdict on the file, within the limits set by the ICAP timeout. Depending on the client implementation, this can cause the transaction to appear unresponsive for a long time (in the order of minutes in some cases).
This blocking mode is particularly suitable for integration with third-party proxies that implement mechanisms to improve the user experience. Such mechanisms can include data trickling or “patience pages”, providing feedback to the user.
FULL WITH FEEDBACK - This mode will generate “patience pages” that provide feedback to the user on the analysis progress. These mechanisms have been tested exclusively with the squid proxy. They can lead to unwanted side effects when using third-party proxies, which can implement caching mechanisms that disrupt the NSX Defender operation. Such third-party proxies often implement their mechanisms to improve user experience and therefore can perform better with the Full blocking mode.
Configuring NSX Advanced Load Balancer for NSX Defender
The following configuration ICAP server-specific options are required to enable ICAP scanning using NSX Defender:
Service URI - This needs to be set to /lastline to use the NSX Defender service.
ICAP Pool - ICAP pool needs to point to NSX Defender ICAP server:port.
Status URL - Only applicable to NSX Defender and has a default value of https://user.lastline.com/portal#/analyst/task/$uuid/overview.
The remaining configuration options are generic and not tied to any particular ICAP server.
For the TLS connection to NSX Defender to work it is required to have an SSL policy with ciphers supported by NSX Defender. The default SSL Policy does not contain those ciphers.
If there are connection issues, adding TLS_RSA_WITH_AES_128_GCM_SHA256 to the applied SSL Profile will allow the connection to succeed.
Visibility Changes for NSX Defender Reported Information
X-Lastline HTTP headers - Pages analyzed by the ICAP instance may contain additional information on the analysis status using additional HTTP headers. The presence of such headers can be deactivated from the ICAP configuration.
X-Lastline-Status - Provides information on the state of the object at the time of analysis. The following values are possible:
new - The specific file hash has not been recently analyzed by NSX Defender and a score is not currently available.
known - The specific file is known, and a score is associated with it.
blacklist - The contacted remote endpoint has a low reputation.
timeout - The process reached its timeout while waiting for the analysis of the file.
error - An error is preventing the analysis of the file.
X-Lastline-Score — The score currently associated with the file, if known, is expressed as a value between 0-100.
X-Lastline-Task — The NSX Defender task UUID is associated with the analysis of the file. It is possible to use this UUID to access the analysis details from the NSX Defender Portal/Manager Web UI. The following is the REST API to access information about any upload using UUID:
Following is the snapshot of Analysis overview based on the task UUID:
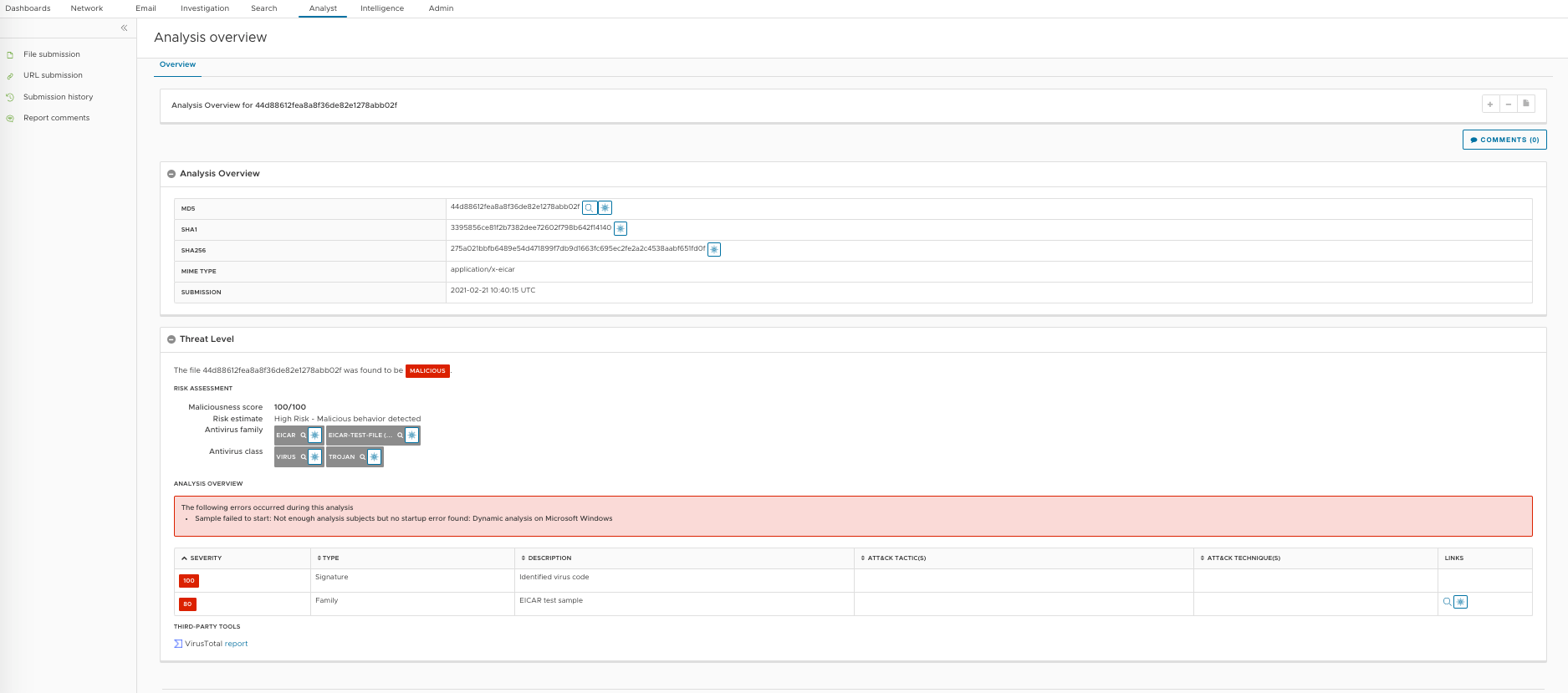
ICAP Response Header
NSX Defender can also send the following ICAP headers as part of the ICAP response as per the ICAP extension draft.
X-Infection-Found: Type=0;Resolution=1;Threat=LastlineArtifact(score=XX;md5=;uuid=)
X-Virus-ID: LastlineArtifact(score=100;md5=;task_uuid=)