The easiest and most scalable method to provide network layer access control lists is through a Network Security Policy pointing to an IP Group. The IP Group can be used by multiple virtual services. When an IP is added to the group, that address will be blocked by all virtual services with a network security policy blocking the list of addresses of the IP Group.
Create an IP ACL
Set up the environment using the following steps:
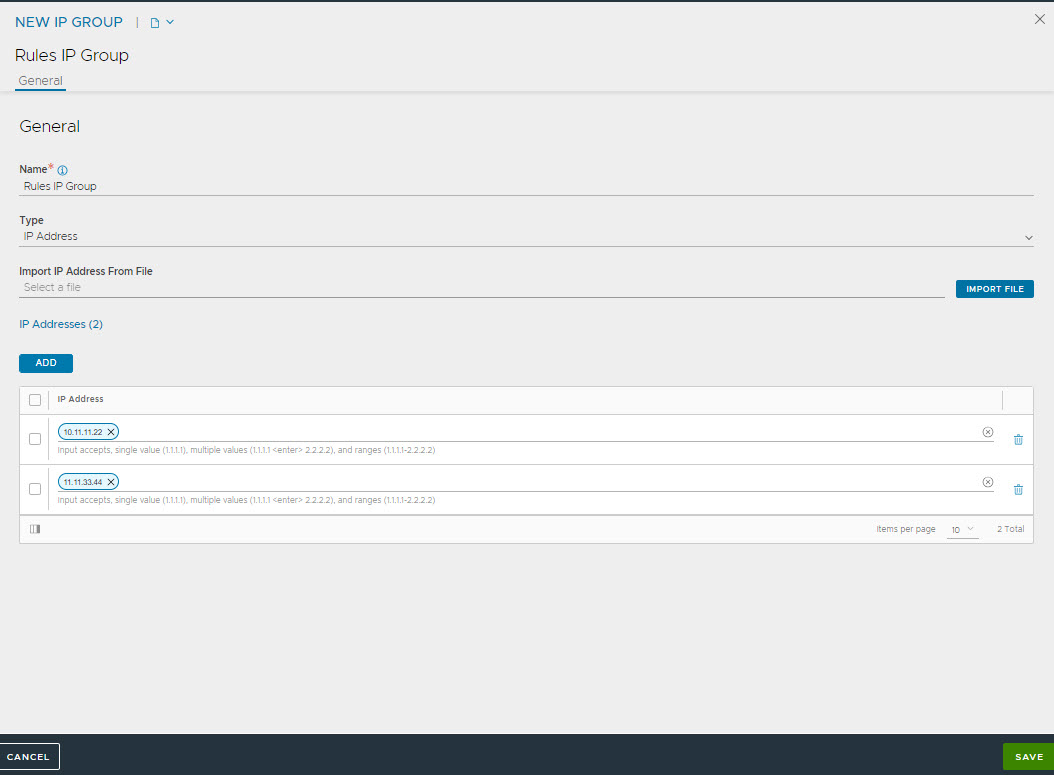
In the NSX Advanced Load Balancer UI, navigate to and create a new IP Group.
Create or edit a virtual service.
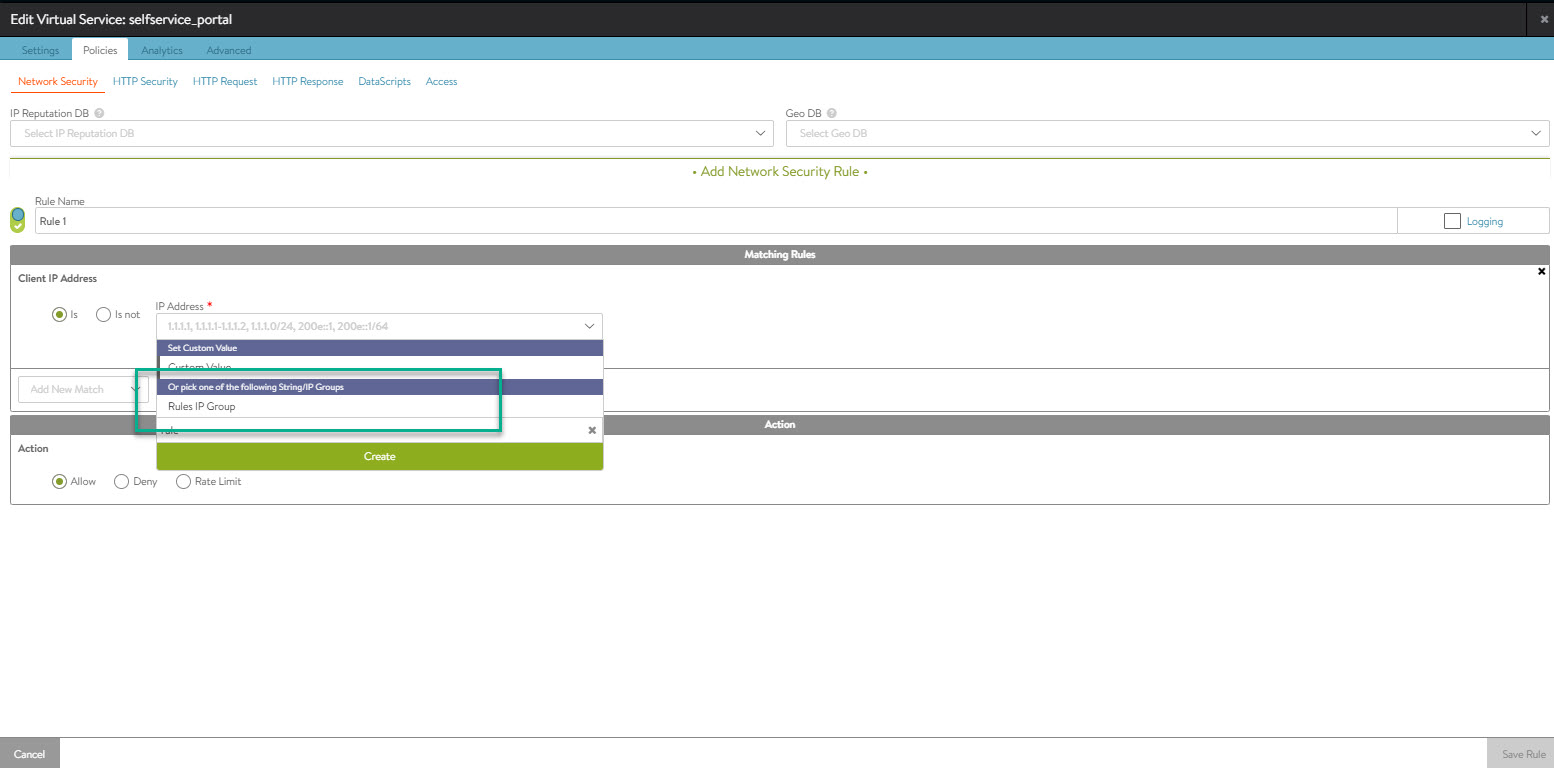
Navigate to and add a new Network Security rule. Set the match to IP address and select the new IP Group from the drop-down menu.
For more information on creating an IP access control list through DataScripts, see Block an IP Address from Access to a Virtual Service.
Retrieve the UUID of the IP Group
To update the ACL list, first acquire the UUID of the IP Group. API calls can be made to the name of an object. UUIDs are preferred over object names for API calls as they are unique. In the following example, the Controller’s cluster IP is 10.1.1.1 and the IP Group is named blocklist.
https://10.1.1.1/api/ipaddrgroup?name=blacklist
The following JSON result is returned from the example query:
{
"count": 1,
"results": [
{
"url": "https://10.1.1.1/api/ipaddrgroup/ipaddrgroup-dc43bd65-7227-4585-8213-34c84c9b1c3b",
"uuid": "ipaddrgroup-dc43bd65-7227-4585-8213-34c84c9b1c3b",
"name": "Blacklist"
"tenant_ref": "https://10.1.1.1/api/tenant/admin",
"prefixes": [
{
"ip_addr": {
"type": "V4",
"addr": "10.128.0.0"
},
"mask": 16
},
]
}
]
}
The query can be filtered to be more specific by appending &fields=uuid.
In this example, an IP network 10.128.0.0/16 already exists in the IP Group.
Modify the IP Group through API
To add the IP network 10.0.0.0/16 and the IP range 192.168.0.1- 192.168.1.250 to the IP group, make a PUT request to the IP group URL https://10.1.1.1/api/ipaddrgroup/ipaddrgroup-dc43bd65-7227-4585-8213-34c84c9b1c3b with the following payload:
{
"url": "https://10.1.1.1/api/ipaddrgroup/ipaddrgroup-dc43bd65-7227-4585-8213-34c84c9b1c3b",
"uuid": "ipaddrgroup-dc43bd65-7227-4585-8213-34c84c9b1c3b",
"name": "Blacklist",
"tenant_ref": "https://10.1.1.1/api/tenant/admin",
"ranges": [
{
"begin": {
"type": "V4",
"addr": "192.168.1.1"
},
"end": {
"type": "V4",
"addr": "192.168.1.250"
}
}
],
"prefixes": [
{
"ip_addr": {
"type": "V4",
"addr": "10.128.0.0"
},
"mask": 16
},
{
"ip_addr": {
"type": "V4",
"addr": "10.0.0.0"
},
"mask": 16
}
]
}
All the necessary configurations, including previously configured IP addresses, must be included in the PUT request.