The 22.1.3 version of the NSX Advanced Load Balancer supports Client/ Relying Party (RP)-initiated logout for OpenID. As the OAuth Client (RP), the NSX Advanced Load Balancer initiates a request, that directs the Identity Provider (IDP) to log out by redirecting the user agent to the logout endpoint of the IDP.
RP-initiated Logout is applicable only if OIDC is enabled.
Controller-Initiated Logout Flow
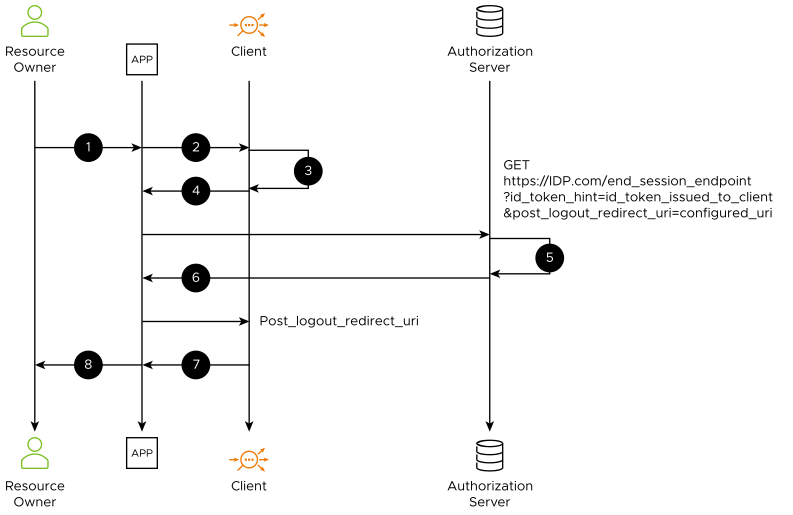
The flow of the Controller-initiated logout is explained below:
The Resource Owner or User clicks the Logout button provided by the application and navigates to the logout URI, for instance, /oauth/logout, which is configured in NSX Advanced Load Balancer.
Note:The Logout button is provided by the application and not by NSX Advanced Load Balancer.
Application or browser sends the logout request to the NSX Advanced Load Balancer.
The NSX Advanced Load Balancer clears out the session details of the user from the session DB.
The NSX Advanced Load Balancer sends the redirect request to the end session endpoint of the Authorization Server or IDP (which is configured in NSX Advanced Load Balancer) with the invalid cookie to clear out the existing application or Browser cookies.
GET https://IDP.com/end_session_endpoint?id_token_hint=id_token_issued_to_client&post_logout_redirect_uri=configured_uri
Authorization Server/IDP clears the session details of the user and,
The admin must first configure post_logout_redirect_uri at the IDP (for instance, okta) end, to which IDP redirects the user after logout is performed.
If step a is not done, the NSX Advanced Load Balancer will configure post_logout_redirect_uri.
Authorization Server/ IDP redirects to the NSX Advanced Load Balancer endpoint at post_logout_redirect_uri.
The user can log out successfully.
After successful logout, the user must provide the credentials to again access the resources, and the NSX Advanced Load Balancer initiates the OAuth login flow.
The above flow is applicable only when a valid session cookie is sent by the client on clicking the Logout button.
URI Endpoints
The three URI endpoints in RP-Initiated logout are as follows:
- Logout URI (Mandatory):
-
This endpoint is configured in NSX Advanced Load Balancer and the Logout button in the application navigates to this endpoint.
- End Session Endpoint (Mandatory):
-
This endpoint is configured in NSX Advanced Load Balancer and provided by IDP.
- Post Logout Redirect URI (Recommended):
-
The endpoint URI to which the RP requests that the end-user’s user agent be redirected to, after a logout has been performed. The same value must be configured in the IDP and the NSX Advanced Load Balancer.
Configuring RP-Initiated Logout Using the UI
For more information on prerequisite configuration steps for OIDC, see Client and Resource Server for OAuth / OIDC section above.
Navigate to .
Click Create or edit the existing Virtual Services.
Navigate to .
Under Access Policy, select OAUTH.
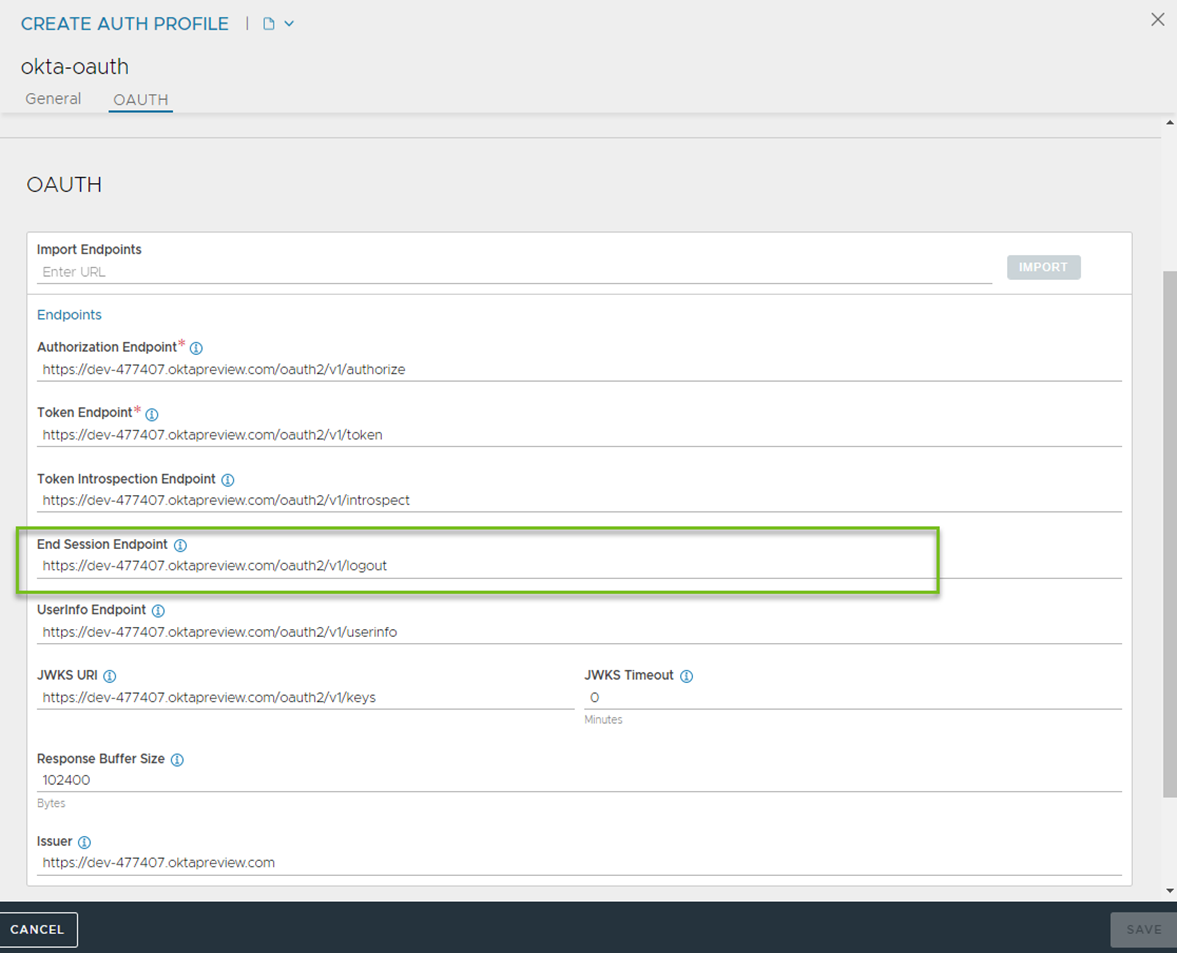
Create or edit an Auth Profile by configuring End Session Endpoint.
Under Access Policy, enter the details in the fields.
Enter Logout URI and Post Logout Redirect URI as shown below:
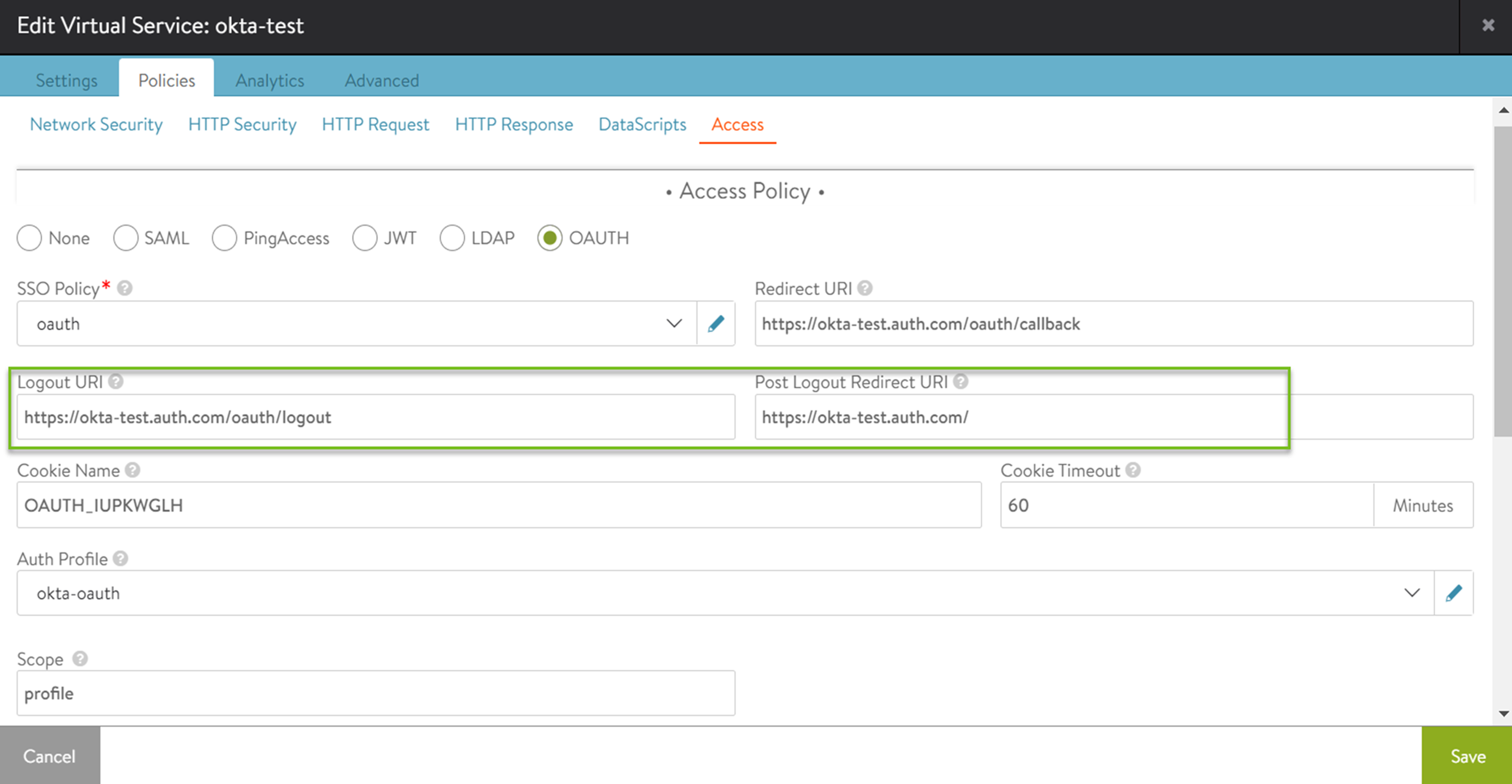
Click Save.
Configuring RP-Initiated Logout Using the CLI
The prerequisite configuration steps for OIDC are explained here.
Configure OAuth oauth_profile of authprofile with end_session_endpoint or logout URI of IDP (For example, okta)
[admin: controller]: > configure authprofile okta-oauth [admin: controller]:authprofile > oauth_profile [admin: controller]:authprofile:oauth_profile> end_session_endpoint https://dev-477407.oktapreview.com/oauth2/v1/logout [admin: controller]:authprofile:oauth_profile>save [admin: controller]:authprofile>save [admin: controller]:>
Configure OAuth enabled virtual service with oidc_enable set to
trueusing configure virtualservice <VS_NAME> command.[admin: controller] configure virtualservice okta-test
Configure logout_uri and post_logout_redirect_uri under the oauth_vs_config submodule of virtual service.
[admin: controller]:virtualservice> oauth_vs_config [admin: controller]:virtualservice:oauth_vs_config> logout_uri https://okta-test.auth.com/oauth/logout [admin: controller]:virtualservice:oauth_vs_config> post_logout_redirect_uri https://okta-test.auth.com/ [admin: controller]:virtualservice:oauth_vs_config> save [admin: controller]:virtualservice> save [admin: controller]:>
Output:
[admin:controller]: virtualservice> oauth_vs_config [admin:controller]: virtualservice:oauth_vs_config> where Tenant: admin Cloud: Default-Cloud +--------------------------+-------------------------------------------------+ | Field | Value | +--------------------------+-------------------------------------------------+ | redirect_uri | https://okta-test.auth.com/oauth/callback | | cookie_name | OAUTH_IUPKWGLH | | cookie_timeout | 1 min | | oauth_settings[1] | | | auth_profile_ref | okta-oauth | | app_settings | | | oidc_config | | | oidc_enable | True | | profile | True | | userinfo | True | | client_id | 0oaubdgcuk6wLEfKq0h7 | | client_secret | <sensitive> | | resource_server | | | access_type | ACCESS_TOKEN_TYPE_OPAQUE | | opaque_token_params | | | server_id | 0oaubdgcuk6wLEfKq0h7 | | server_secret | <sensitive> | | key[1] | | | name | dc7dde0a-8a64-45b4-8ded-f65adb03c2a4 | | aes_key | b'sdZFYlVECVu9aW7XK4IhVaC8TfakvNSvp6m861tyVNc=' | | logout_uri | https://okta-test.auth.com/oauth/logout | | post_logout_redirect_uri | https://okta-test.auth.com/ |
The end_session_endpoint is configured under authprofile as shown below:
[admin:controller]: > show authprofile okta-oauth +--------------------------+---------------------------------------------------------+ | Field | Value | +--------------------------+---------------------------------------------------------+ | uuid | authprofile-998740b9-5123-4d4d-8fb9-f9f9a3886248 | | name | okta-oauth | | type | AUTH_PROFILE_OAUTH | | oauth_profile | | | authorization_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/authorize | | token_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/token | | introspection_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/introspect | | jwks_uri | https://dev-477407.oktapreview.com/oauth2/v1/keys | | jwks_timeout | 0 min | | issuer | https://dev-477407.oktapreview.com | | pool_ref | pool-okta | | oauth_resp_buffer_sz | 1000000 | | userinfo_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/userinfo | | end_session_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/logout | | tenant_ref | admin | +--------------------------+---------------------------------------------------------+
Logout URI is only applicable if OIDC is enabled.
End Session Endpoint must be configured to configure Logout URI.
End Session Endpoint cannot be removed if Logout URI is configured. To remove the End Session Endpoint, no value must be configured for the Logout URI.