Add a new certificate from a trusted Certificate Authority. If more than one CA is included in the PKI profile then, a client’s certificate must match with one of them to be considered as valid.
A client’s certificate must match the CA as the root of the chain. If the presented certificate has an intermediate chain then, each link in the chain must be included here. Enable Ignore Peer Chain to ignore intermediate validation checking.
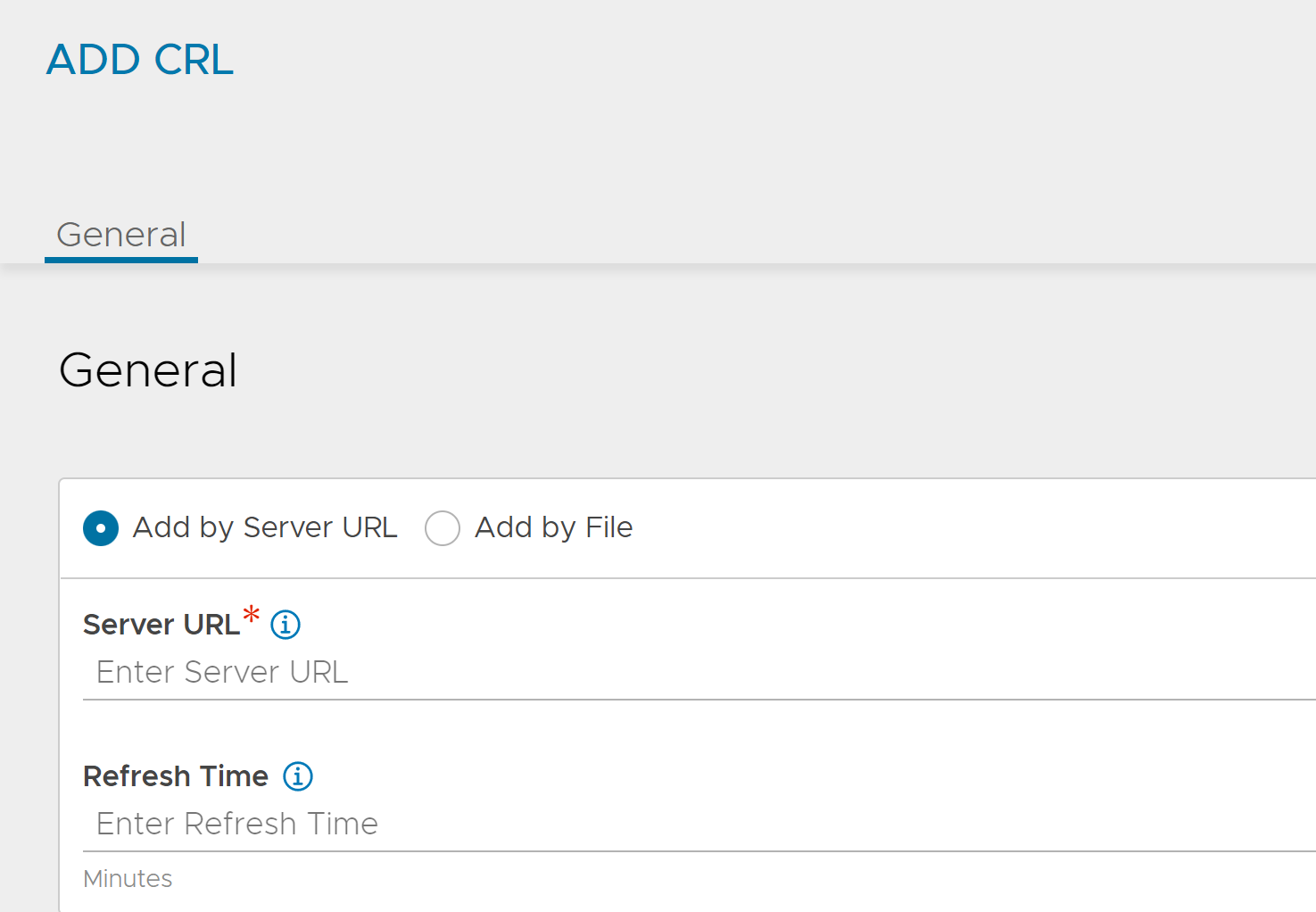
Certificate Revocation List
The CRL allows invalidation of certificates (serial number). The revocation list may be updated by uploading a new CRL manually, or by downloading from a CRL server periodically. If a client or server certificate is found to be in the CRL, the SSL handshake will fail, with a resulting log created to provide further information about the handshake.
Leaf Certificate CRL validation only: When enabled, NSX Advanced Load Balancer will only validate the leaf certificate against the CRL. The leaf is the next certificate in the chain up from the client certificate. A chain may consist of multiple certificates. To validate all certificates against the CRL, disable this option. Deactivating this option means you need to upload all the CRLs issued by each certificate in the chain. Even if one CRL is missing, the validation process will fail.
Server URL: Specify a server from which CRL updates can be downloaded. Access to this server will be done from the NSX Advanced Load Balancer Controller IP addresses, which means they will require firewall access to this destination. The CRL server may be identified by an IP address or a fully qualified domain name (FQDN) along with an HTTP path, such as https://www.avinetworks.com/crl.
Refresh Time: Enter the time (in minutes) after which NSX Advanced Load Balancer checks for a CRL update and automatically downloads an updated version of the CRL. For more information, see the below section.
Upload Certificate Revocation List File: Navigate to the CRL file to upload. Subsequent CRL updates can be done by manually uploading newer lists, or configuring the Server URL and Refresh Time to automate the process.
Refresh Time
NSX Advanced Load Balancer checks for a CRL update and automatically downloads an updated version of the CRL on a regular schedule starting from the time of the creation of the PKI Profile.
NSX Advanced Load Balancer checks the CRL distribution point for a new CRL at the configured Refresh Interval. If no Refresh Interval is configured or if the Refresh Interval is greater than 1440 minutes (one day), then an interval of 1440 minutes is used.
The CRL Distribution Server must support ETag semantics. NSX Advanced Load Balancer checks the CRL distribution point using the If-None-Match option and ETag obtained from the last downloaded CRL response. If the CRL has not been modified, the server responds with 304 Not Modified and no further action is taken until the next refresh interval.
In general, most Certificate Authorities update CRLs on a known regular schedule but in some cases CRL publishing intervals may be variable and the expiry (Next Update) time for a given CRL can also vary. The Refresh Interval must be configured such that NSX Advanced Load Balancer checks for an updated CRL with sufficient frequency to ensure the CRL will never expire.
If the expiry (Next Update) time of the CRL is passed without a new CRL being downloaded, the CRL will become invalid and NSX Advanced Load Balancer will fail close and treat all submitted certificates as untrusted. Override this behavior by deferring the certificate validation to a DataScript and treating the expired CRL condition as fail open. See NSX Advanced Load Balancer SSL Client Certificate Validation section in VMware NSX Advanced Load BalancerDataScript guide.
If the NSX Advanced Load Balancer Controller is rebooted or is down for a certain time then upon reboot the Controller will resume the regular refresh schedule using the last_refreshed time stored in the PKI Profile. If the Controller comes back online after being down for an extended period such that one or more scheduled refresh intervals have been missed (based on the last_refreshed timestamp and configured refresh interval in the PKI Profile), then the Controller will immediately check for an updated CRL.
To configure the Refresh Timer, navigate to .
Dynamic Scheduling of CRL Update
Starting with NSX Advanced Load Balancer 22.1.3, CRL update is dynamically scheduled if Refresh Time is not configured. If Refresh Time is configured, CRL update occurs regularly using this interval. If Refresh Time is not configured or left blank, NSX Advanced Load Balancer dynamically schedules the next CRL update attempt after (NextUpdate – Now)/2 seconds.