The expected isolation and administrative restrictions of a multi-tenant architecture extend to NSX Advanced Load Balancer GSLB.
Predefined Roles
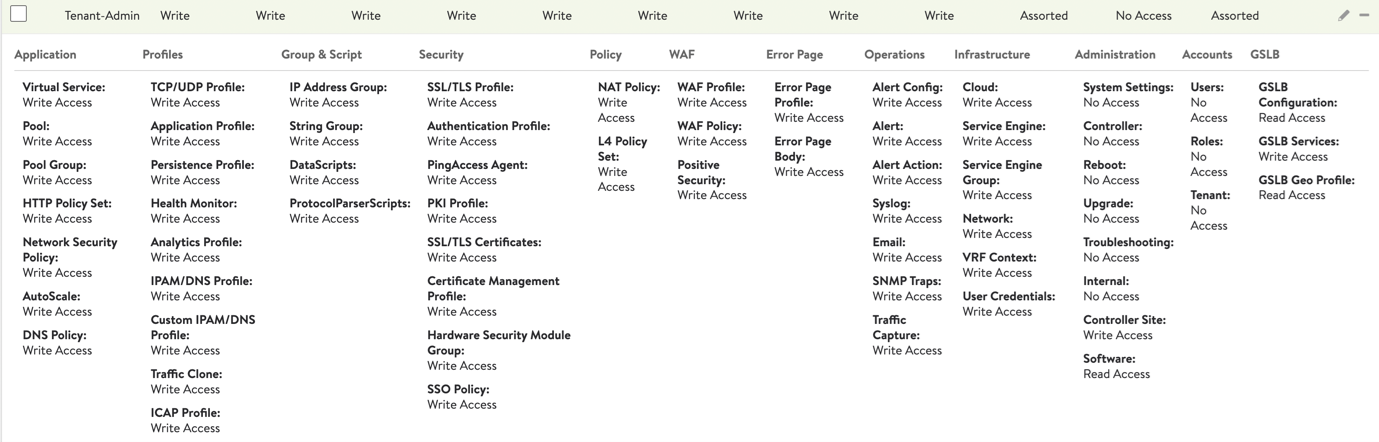
Navigate to to check the default predefined roles. These roles are assigned to authorized Controller users. In our particular example, clicking the plus sign at the right end of the Tenant-Admin role row expands all ten columns, revealing more details about different aspects of the NSX Advanced Load Balancer platform. GSLB rights (red rectangle) focus on access to three GSLB entities – the GSLB configuration, global applications (services), and the geolocation database that supports geolocation.
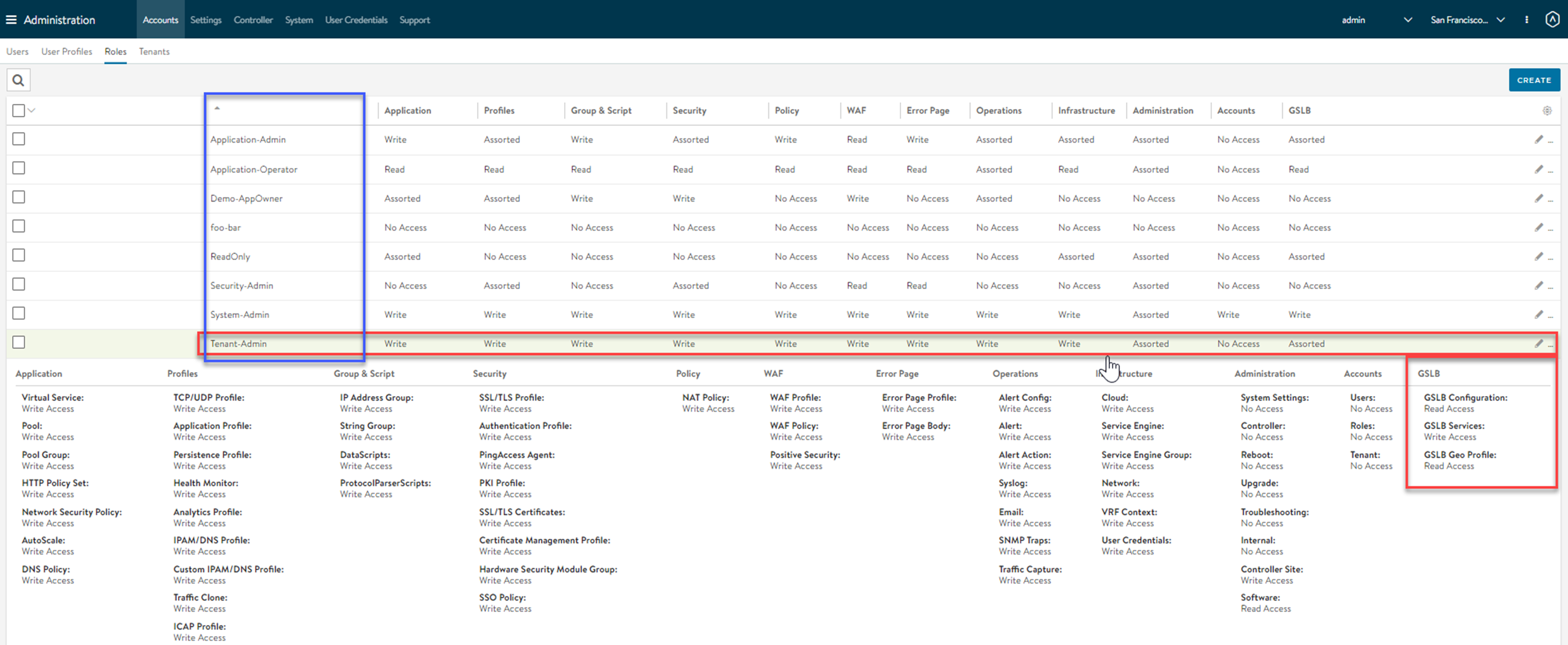
For each role in the system, access rights can be independently set. The following table summarizes GSLB access rights for three of the predefined roles. Custom-defined roles are also supported.
Predefined Roles |
Access Rights |
|
|---|---|---|
System-Admin |
GSLB configuration |
Write access to entire GSLB configuration |
GSLB services |
Write access to all GSLB services in all tenants |
|
GSLB geolocation database |
Write access to geolocation database |
|
Tenant-Admin |
GSLB configuration |
Read access to everything in the GSLB configuration relevant to the tenant |
GSLB services |
Write access to all GSLB services in all tenants |
|
GSLB geolocation database |
Read access to geolocation database |
|
Application-Admin |
GSLB configuration |
Read access to entire GSLB configuration |
GSLB services |
Write access to all GSLB services in all tenants to which this user is assigned |
|
GSLB geolocation database |
Read access to geolocation database |
|
GSLB Administrators, Global Application Administrators
An authorized user can use different access rights, depending on the requirements.
GSLB is only configured by a user account having write access to GSLB Configuration. The access is predefined in the System-Admin role, and GSLB can be configured only within the admin tenant. A system administrator places the DNS virtual service in the admin tenant or another tenant. However, a site’s GSLB DNS virtual service can only be configured into a non-admin-tenant through the CLI using the UUID of the DNS virtual service. Each application administrator associated with the NSX Advanced Load Balancer tenant can use the shared-DNS virtual service for their global applications.
A user with write access to GSLB Services and read access to GSLB Configuration can define global applications (GSLB services) in their tenant. The requisite DNS records are registered on the shared DNS service. The tenant administrator can get analytics of the GSLB services defined only for that tenant.
GSLB service creation depends on the permissions of the GSLB user and not on the tenant user who is logged in.
For better audit trails, It is recommended to log in to a user account set up for GSLB configuration. For example, you might create a user named gslb and assign it admin roles in all the Controller Clusters.
Custom Defined Roles
NSX Advanced Load Balancer also supports creating custom roles for GSLB. In a scenario that does not require System-admin/admin user for GSLB configuration, a custom user and role can be defined for the same.
Use Case 1
Need a non-admin user (user that don’t need full System-Admin role) account in the site configuration:
Create a new role.
For creating new role, navigate to and create a new role as shown below:
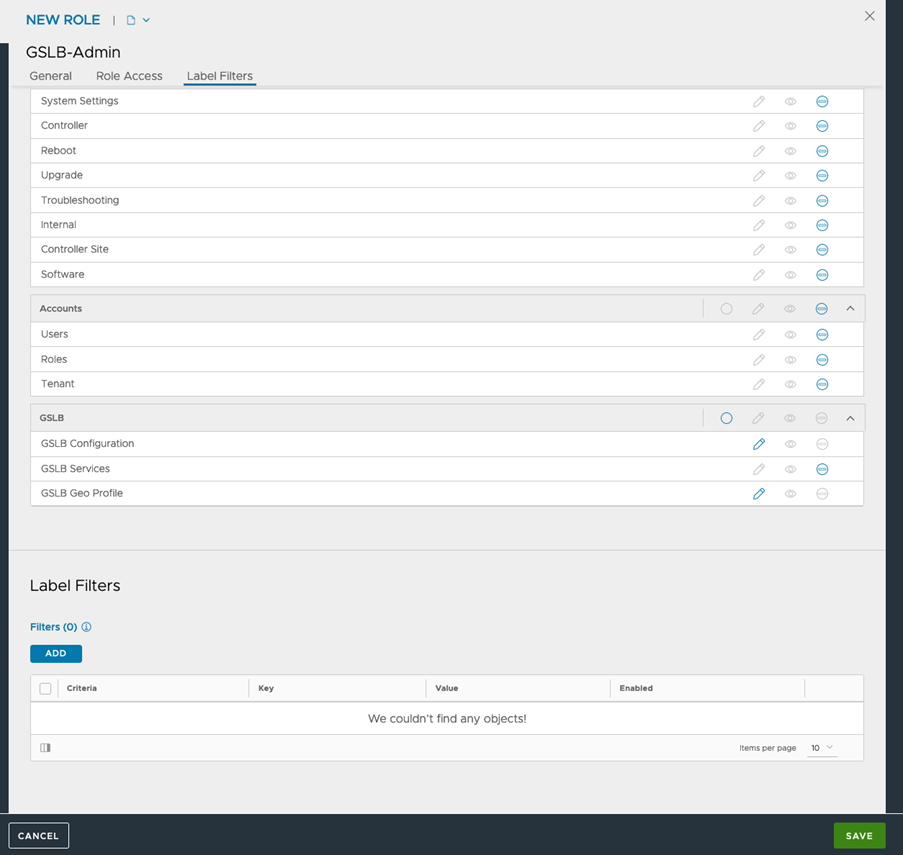
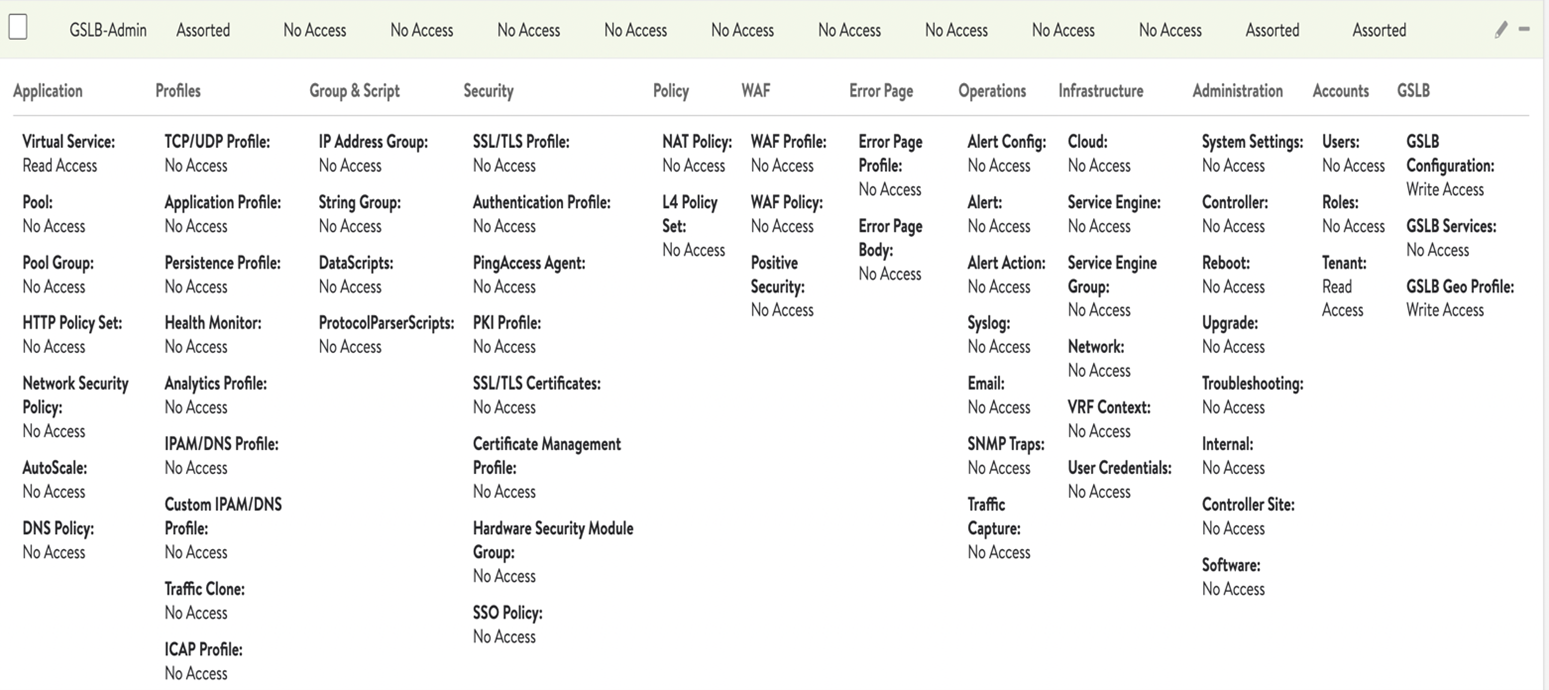
The settings to be used for this role are shown below:
-
Note:
This role does not provide any access to GSLB services. This is primarily for site creation. If GSLB service access is also required, ensure to enable the same for GSLB services.
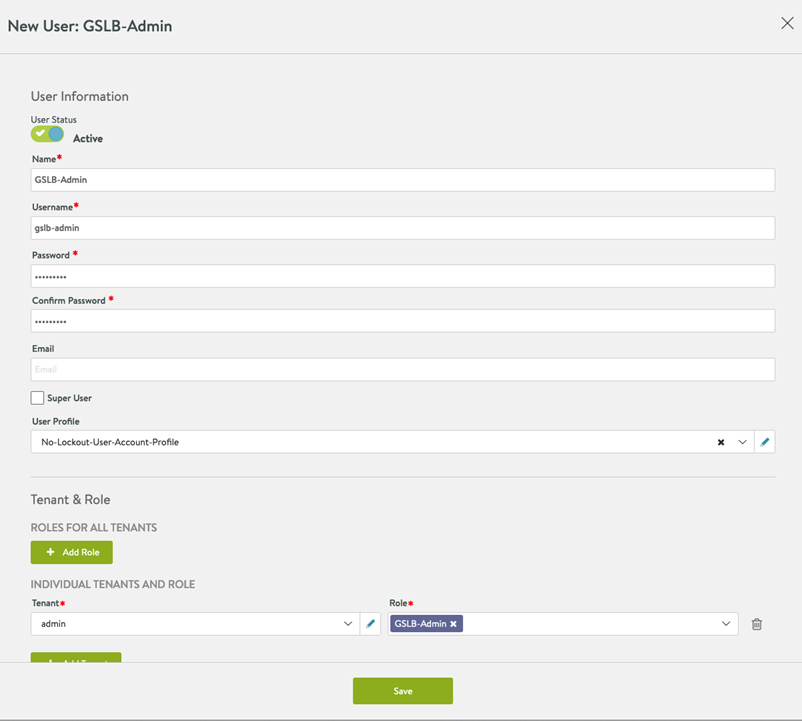
Create non-admin user and assign the role configured above. To create a new user, navigate to .
Use Case 2:
The user needs permission to create GSLB service within a tenant:
Create a role with the settings shown below:
Create a new user and assign this new role to the user.
Changes to NSX Advanced Load Balancer UI Access based on Privileges
If the privilege setting for the GSLB configuration is set to No Access and the privilege for the GSLB Service is set to Read or Write, the GSLB Services tab on the NSX Advanced Load Balancer UI is accessible.
The following are the additional features available, but with some limitations as mentioned below:
The access mentioned above is available only in Read only mode. You cannot edit existing GSLB Services or create a new GSLB service.
You can view the table, click the Service, and see Member Status and Events subtabs, but not the FQDN Insights subtab.
The Create option is greyed out, with hover text reading: GSLB Config permissions must be set to Read or Write to create a GSLB service.
The following are the options that remain the same:
If the privileges for the GSLB Service are set to Read only mode, and GSLB Configuration is Read or Write, then you will still be in Read only mode, but the FQDN Insights sub-tab will be available.
If GSLB Services is set to No Access, the entire GSLB Services tab is not available.
If the GSLB Service permission is set to Write, but the service site is a child site, the Create option will be greyed out, and the NSX Advanced Load Balancer UI exhibits GSLB Site {Leader Site Name} is the leader.
GSLB site can be configured based on the privileges for GSLB admin.