Once the Prod-Xacc-Access is set up in the Prod AWS account (112233445566), any user or role in the IT AWS account (123456789012) will be able to assume the role with appropriate configuration, as explained in the steps given in this section:
Create the policy Cross-Account-AssumeRole-policy, which will be attached to the IT-AviController-Role role.
Prerequisites
Create the IT-NSX Advanced Load Balancer Controller-Role role in the IT AWS account (123456789012) to assume the role of Prod-Xacc-Access in the Prod AWS Account (112233445566). This is the role to which the Controller instance will be attached.
Procedure
- Navigate toIAM > Policies, and click Create Policy. Configure the policy with sts:AssumeRole action and provide the resource reference for Prod-Xacc-Access role’s ARN, which in this example is arn:aws:iam::112233445566:role/Prod-Xacc-Access.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::112233445566:role/Prod-Xacc-Access"
}
}
- Navigate to theJSON tab, provide the syntax mentioned above, and click on Review Policy to save the policy. For attaching multiple accounts, use the following policy syntax:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<ACCOUNT-ID1>:role/<Role-Name-1>"
},
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<ACCOUNT-ID1>:role/<Role-Name-2>"
},
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<ACCOUNT-ID2>:role/<Role-Name>"
}
]
}
- Navigate to , click Create Role. Select AWS Service, select Amazon EC2 as the role type, and click Next:Permissions.
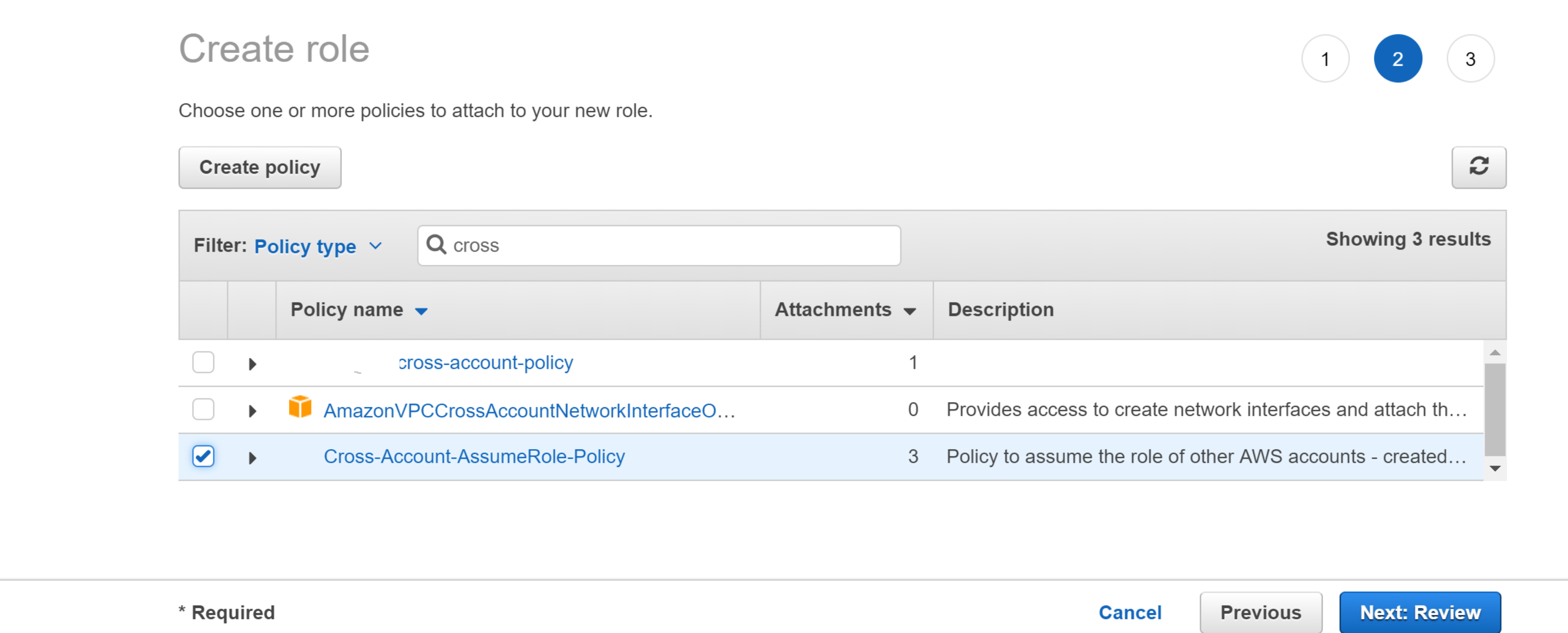
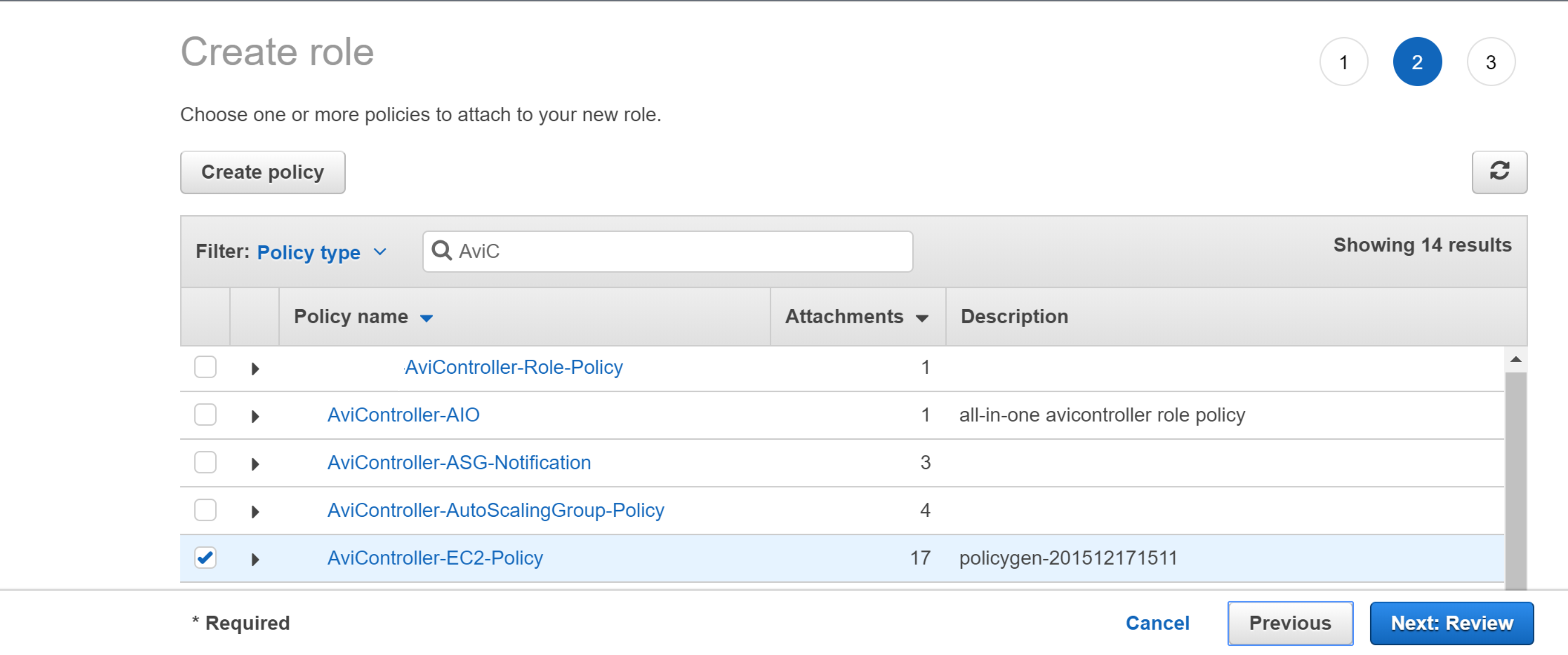
- Under Attach-Policy, select the Cross-Account-AssumeRole-Policy created earlier and also the AviController-EC2-Policy, which is required for the Controller’s internal operations.
- Provide the Role name as IT-AviController-role, the description (optional), and click Create role. Verify if both policies are now attached.